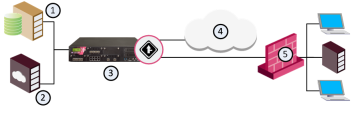
QoS Deployment
|
|
Notes:
|
QoS can manage up to the maximum number of interfaces supported by the Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., subject to these restrictions:
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., subject to these restrictions:
-
All of the traffic on a managed line must go through the gateway.
-
Each managed line must be connected (directly or indirectly via a router) to a separate physical interface on the QoS machine. Two managed lines cannot share a physical interface to the QoS gateway, and two network segments cannot connect to the same router.
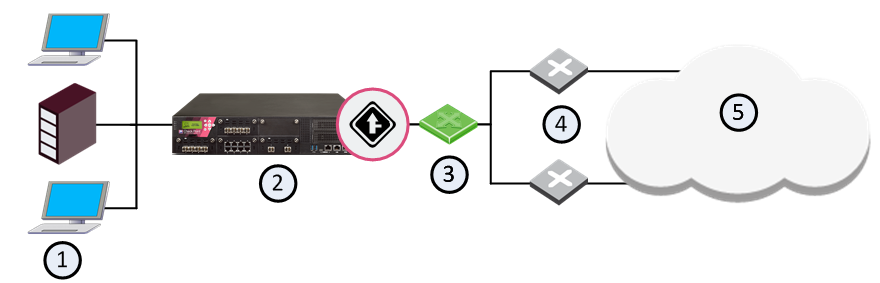
For example, in the configuration depicted in the following diagram, the routers can pass traffic to each other through the hub without the QoS gateway being aware of the traffic.
|
Item |
Description |
|---|---|
|
1 |
Internal network |
|
2 |
Security Gateway with QoS enabled |
|
3 |
Hub |
|
4 |
Routers |
|
5 |
Internet |
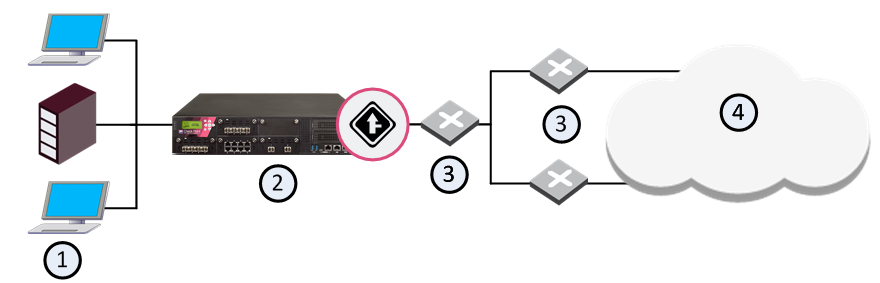
You cannot manage two networks connected to a single router since traffic may pass from one line to the other directly through the router, without the QoS gateway being aware of the traffic:
|
Item |
Description |
|---|---|
|
1 |
Internal network |
|
2 |
Security Gateway with QoS enabled |
|
3 |
Routers |
|
4 |
Internet |
In a correct configuration, the routers connect directly to the QoS gateway.
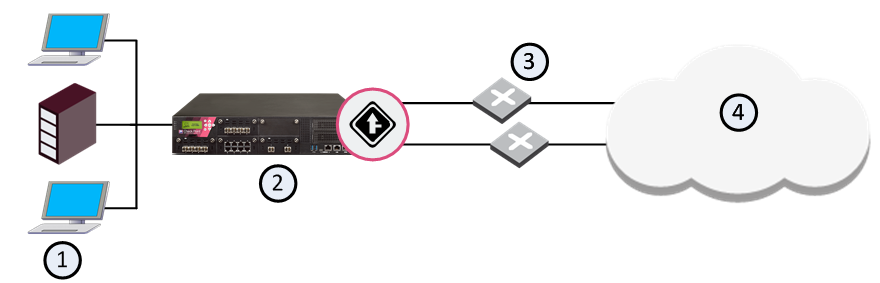
Sample Bandwidth Allocations
Frame Relay Network
|
Item |
Description |
|---|---|
|
1 |
Database server |
|
2 |
Web server |
|
3 |
Security Gateway with QoS enabled |
|
4 |
Internet |
|
5 |
Branch office |
The previous diagram shows that the branch office communicates with the central site and the opposite. It only communicates directly with the Internet through the central site. The Web server makes important company documents available to the branch office, and the database server supports the company's mission-critical applications.
The problem is that most of the branch office traffic is internal and external Web traffic, and the mission-critical database traffic suffers as a result. The network administrator has considered upgrading the 56K lines, but is reluctant to do so, not only because of the cost but also because upgrading would probably not solve the problem. The upgraded lines would still be filled mostly with Web traffic.
The goals are as follows:
-
Allocate the existing bandwidth so that access to the database server gets the largest share.
-
Take into account that the branch offices are connected to the network by 56K lines.
These goals are accomplished with the following Rule Base![]() All rules configured in a given Security Policy. Synonym: Rulebase.:
All rules configured in a given Security Policy. Synonym: Rulebase.:
Main Rules
|
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
|
Office 1 |
Office 1 |
Any |
Any |
Weight 10 Limit 56KBps |
|
Office n |
Office n |
Any |
Any |
Weight 10 Limit 56KBps |
|
Default |
Any |
Any |
Any |
Weight 10 |
Each office has sub-rules:
Office Sub-Rules
|
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
|
Database Rule |
Any |
Database server |
Database service |
Weight 50 |
|
Web Rule |
Any |
Web Server |
http |
Weight 10 |
|
Branch Offices |
Any |
Any |
Any |
Weight 10 |
|
End of Sub Rule |
The sub-rules give database traffic priority over Web traffic and other traffic.
Assumptions
The following assumptions are made in this example:
-
The problem (and its solution) apply to traffic outbound from the central site.

Note - QoS shapes the branch office lines in the outbound direction only. QoS shapes inbound traffic only on directly controlled interfaces (that is, interfaces of the QoS machine).
-
The central site has the capacity to handle the network's peak traffic load.
-
There is no traffic between the offices.