Deploying a Single Security Gateway in Monitor Mode
Introduction to Monitor Mode
You can configure Monitor Mode on a single Check Point Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources.'s interface.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources.'s interface.
The Check Point Security Gateway listens to traffic from a Mirror Port or Span Port on a connected switch.
Use the Monitor Mode to analyze network traffic without changing the production environment.
The mirror port on a switch duplicates the network traffic and sends it to the Security Gateway with an interface configured in Monitor Mode to record the activity logs.
You can use the Monitor Mode:
-
To monitor the use of applications as a permanent part of your deployment
-
To evaluate the capabilities of the Software Blades:
-
The Security Gateway neither enforces any security policy
 Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection., nor performs any active operations (prevent / drop / reject) on the interface in the Monitor Mode.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection., nor performs any active operations (prevent / drop / reject) on the interface in the Monitor Mode. -
The Security Gateway terminates and does not forward all packets that arrive at the interface in the Monitor Mode.
-
The Security Gateway does not send any traffic through the interface in the Monitor Mode.
-
Benefits of the Monitor Mode include:
-
There is no risk to your production environment.
-
It requires minimal set-up configuration.
-
It does not require TAP equipment, which is expensive.
Example Topology for Monitor Mode
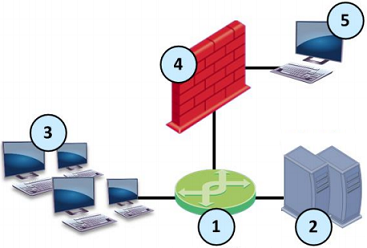
|
Item |
Description |
|---|---|
|
1 |
Switch with a mirror or SPAN port that duplicates all incoming and outgoing packets. The Security Gateway connects to a mirror or SPAN port on the switch. |
|
2 |
Servers. |
|
3 |
Clients. |
|
4 |
Security Gateway with an interface in Monitor Mode. |
|
5 |
Security Management Server |
For More About Monitor Mode
See the:
-
R81 Installation and Upgrade Guide > Chapter Special Scenarios for Security Gateways > Section Deploying a Security Gateway in Monitor Mode.
-
R81 Quantum Maestro Administration Guide > Chapter Deploying a Security Group in Monitor Mode.
-
R81 Quantum Scalable Chassis Administration Guide > Chapter Deploying a Security Group in Monitor Mode.
