Exception Rules
If necessary, you can add an exception directly to a rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session.. An exception sets a different Action to an object in the Protected Scope from the Action specified Threat Prevention rule. In general, exceptions are designed to give you the option to reduce the level of enforcement of a specific protection and not to increase it.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session.. An exception sets a different Action to an object in the Protected Scope from the Action specified Threat Prevention rule. In general, exceptions are designed to give you the option to reduce the level of enforcement of a specific protection and not to increase it.
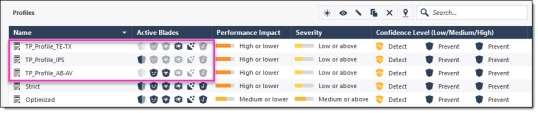
The Research and Development (R&D) network protections are included in a profile with the Prevent action. You can define an exception which sets the specific R&D network to Detect. For some Anti-Bot![]() Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT. and IPS
Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT. and IPS![]() Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System). signatures only, you can define exceptions which are stricter than the profile action.
Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System). signatures only, you can define exceptions which are stricter than the profile action.
You can add one or more exceptions to a rule. The exception is added as a shaded row below the rule in the Rule Base![]() All rules configured in a given Security Policy. Synonym: Rulebase.. It is identified in the No column with the rule's number plus the letter E and a digit that represents the exception number. For example, if you add two exceptions to rule number 1, two lines will be added and show in the Rule Base as E-1.1 and E-1.2.
All rules configured in a given Security Policy. Synonym: Rulebase.. It is identified in the No column with the rule's number plus the letter E and a digit that represents the exception number. For example, if you add two exceptions to rule number 1, two lines will be added and show in the Rule Base as E-1.1 and E-1.2.
You can use exception groups to group exceptions that you want to use in more than one rule. See the Exceptions Groups Pane.
You can expand or collapse the rule exceptions by clicking on the minus or plus sign next to the rule number in the No. column.
|
Step |
Instructions |
|---|---|
|
1 |
In the Policy pane, select the rule to which you want to add an exception. |
|
2 |
Click Add Exception. |
|
3 |
Select the Above, Below, or Bottom option according to where you want to place the exception. |
|
4 |
Enter values for the columns. Including these:
|
|
5 |
Install Policy. |
|
|
Note - You cannot set an exception rule to an inactive protection or an inactive blade. |
Disabling a Protection on One Server
Scenario: The protection Backdoor.Win32.Agent.AH blocks malware on windows servers. How can I change this protection todetectfor one server only?
In this example, create this Threat Prevention rule, and install the Threat Prevention policy:
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
In SmartConsole |
||
|
2 |
Click the rule that contains the scope of Server_1. |
||
|
3 |
Click the Add Exception toolbar button to add the exception to the rule. The gateway applies the first exception matched. |
||
|
4 |
Right-click the rule and select New Exception. |
||
|
5 |
Configure these settings:
|
||
|
6 |
In SmartConsole, install the policy. |
Blade Exceptions
You can configure an exception for an entire blade.
|
Step |
Instructions |
|---|---|
|
1 |
In the Policy, select the Layer rule to which you want to add an exception. |
|
2 |
Click Add Exception. |
|
3 |
Select the Above, Below, or Bottom option according to where you want to place the exception. |
|
4 |
In the Protection/Site column, select Blades from the drop-down menu. |
|
5 |
Select the blade you want to exclude. |
|
6 |
In SmartConsole, install the policy. |
-
Create a separate layer with a separate profile for each blade or a pair of blades (for example: Anti-Virus
 Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. and Anti-Bot, or Threat Emulation
Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. and Anti-Bot, or Threat Emulation Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. and Threat Extraction
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. and Threat Extraction Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX.):
Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX.): -
Create a separate profile for each layer and enable only the specific blade:
-
Create a custom Application/Site for each layer. For instructions, refer to sk165094:
-
Create a Rule Base for each layer, and a different exception rule with the created Custom Application/Site in Protection/Site/File/Blade:
-
In the Action column, select Detect or Inactive to disable the applicable Threat Prevention Blade for the applicable websites/URLs.
Creating Exceptions from IPS Protections
|
Step |
Instructions |
|---|---|
|
1 |
Go to Security Policies > Threat Prevention > Policy > IPS Protections. |
|
2 |
Right-click a protection and select Add Exception. |
|
3 |
Configure the exception rule. |
|
4 |
Click OK. |
|
5 |
Install Policy. |
Creating Exceptions from Logs or Events
In some cases, after evaluating a log or an event in the Logs & Monitor view, it may be necessary to update a rule exception in the SmartConsoleRule Base. You can do this directly from within the Logs & Monitor view. You can apply the exception to a specified rule or apply the exception to all rules that show under Global Exceptions.
|
Step |
Instructions |
|---|---|
|
1 |
Click Logs & Monitor > Logs tab. |
|
2 |
Right-click the log and select Add Exception. |
|
3 |
Configure the settings for the exception. |
|
4 |
Configure the settings for the exception. |
|
5 |
In the New Exception Rule window:
|
|
6 |
Install Policy. |