High Level Overview of Event Identification
Events are detected by the SmartEvent Correlation Unit![]() SmartEvent software component on a SmartEvent Server that analyzes logs and detects events.. The SmartEvent Correlation Unit scans logs for criteria that match an Event
SmartEvent software component on a SmartEvent Server that analyzes logs and detects events.. The SmartEvent Correlation Unit scans logs for criteria that match an Event![]() Record of a security or network incident that is based on one or more logs, and on a customizable set of rules that are defined in the Event Policy. Definition.
Record of a security or network incident that is based on one or more logs, and on a customizable set of rules that are defined in the Event Policy. Definition.
SmartEvent uses these procedures to identify these events:
Matching a Log Against Global Exclusions
When the SmartEvent Correlation Unit reads a log, it first checks if the log matches all defined Global Exclusions. Global Exclusions (defined on the Policy tab > EventPolicy > Global Exclusions) direct SmartEvent to ignore logs that are not expected to contribute to an event.
If the log matches a Global Exclusion, it is discarded by the system. If not, the SmartEvent Correlation Unit starts to match it against each Event Definition.
Matching a Log Against Each Event Definition
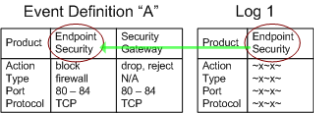
Each Event Definition contains a filter which is comprised of a number of criteria that must be found in all matching logs. The criteria are divided by product: The Event Definition can include a number of different products, but each product has its own criterion.
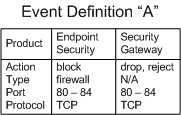
To match the Event Definition "A", a log from Endpoint Security must match the Action, Event Type, Port, and Protocol values listed in the Endpoint Security column. A log from a Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. must match the values listed in its column.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. must match the values listed in its column.
SmartEvent divides this procedure into two steps. The SmartEvent Correlation Unit first checks if the Product value in the log matches one of the permitted Product values of an Event Definition.
If Log 1 did not contain a permitted Product value, the SmartEvent Correlation Unit compares the log against Event Definition "B", and so on. If the log fails to match against an Event Definition, it is discarded.
The SmartEvent Correlation Unit checks if the log contains the Product-specific criteria to match the Event Definition. For example: The product Endpoint Security generates logs that involve the Firewall, Spyware, Malicious Code Protection, and others. The log contains this information in the field Event Type. If an event is defined to match on Endpoint Security logs with the event type Firewall, an Endpoint Security log with Event Type "Spyware" fails against the Event Definition filter. Other criteria can be specified to the Product.
In our example, Log 1 matched Event Definition "A" with a permitted product value. The SmartEvent Correlation Unit examines if the log contains the necessary criteria for an Endpoint Security log to match.
If the criteria do not match, the SmartEvent Correlation Unit continues to compare the log criteria to other event definitions.
Creating an Event Candidate
When a log matches the criteria, it is added to an Event Candidate. Event candidates let SmartEvent track logs until an event threshold is crossed, at which point an event is generated.
The logs can come from different log servers and be correlated in the same event.
The Event Candidate tracks logs until the criteria is matched (the criteria is the number of logs in a declared number of seconds).
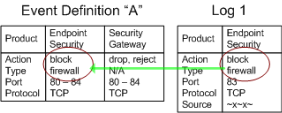
Each Event Definition can have multiple event candidates, each of which keeps track of logs grouped by equivalent properties. In the figure above the logs that create the event candidate have a common source value. They are dropped, blocked or rejected by a Security Gateway. They are grouped together because the Event Definition is designed to detect this type of activity that originates from one source. Depending on the event declaration, if there is a grouping declaration on the source field, it will create a new event candidate.
When a log matches the event definition, but has properties different than those of the existing event candidates, a new event candidate is created. This event candidate is added to what can be thought of as the Event Candidate Pool.
By default, SmartEvent creates a new event candidate for a log with a different source.
To customize the default behavior:
-
Go to SmartEvent > Policy.
-
Select an event and right-click > Select Properties.
The Edit Event Definition window opens.
-
In the Count logs tab, click the options under Select the fields by which distinct Event Candidates will be created.
-
In the Event Definition Wizard window, select the log fields and click OK.
To illustrate more, an event defined detects a high rate of blocked connections. SmartEvent tracks the number of blocked connections for each Security Gateway, and the logs of the blocked traffic at each Security Gateway forms an event candidate. When the threshold of blocked connection logs from a Security Gateway is surpassed, that Security Gateway event candidate becomes an event. While this Event Definition creates one event candidate for each Security Gateway monitored, other Event Definitions can create many more.
The Event Candidate Pool is a dynamic environment, with new logs added and older logs discarded when they have exceeded an Event Definition time threshold.
Matching a Log Against Event Exclusion
Before SmartEvent generates logs for a specific event, it checks to see if this event candidate attributes are listed in the exclusions table or not. Event Exclusions are defined on the Policy tab > Event Policy > Event Exclusions according to the attributes selected.
If an attribute matches an Event Exclusion, it is discarded by the system (an event is not generated). If not, the SmartEvent Correlation Unit starts to match it against each Event Definition.
Event Generation
When a candidate becomes an event, the SmartEvent Correlation Unit forwards the event to the Event Database. But to discover an event does not mean that SmartEvent stops to track logs related to it. The SmartEvent Correlation Unit adds matching logs to the event as long as they continue to arrive during the event threshold. To keep the event open condenses what can appear as many instances of the same event to one, and provides accurate, up-to-date information as to the start and end time of the event.