Cooperative Enforcement Solution
Cooperative Enforcement![]() Integration of an on-premises Harmony Endpoint Security Server and Security Gateway. works with Check Point Point Endpoint Security Management Servers. This feature utilizes the Endpoint Security Management Server
Integration of an on-premises Harmony Endpoint Security Server and Security Gateway. works with Check Point Point Endpoint Security Management Servers. This feature utilizes the Endpoint Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. compliance function to make sure connections that come from different hosts across the internal network.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. compliance function to make sure connections that come from different hosts across the internal network.
Endpoint Security Management Server![]() Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. is a centrally managed, multi-layered endpoint security solution that employs policy based security enforcement for internal and remote PCs. The Endpoint Security Management Server mitigates the risk of hackers, worms, spyware, and other security threats.
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. is a centrally managed, multi-layered endpoint security solution that employs policy based security enforcement for internal and remote PCs. The Endpoint Security Management Server mitigates the risk of hackers, worms, spyware, and other security threats.
Features such as policy templates and application privilege controls enable administrators to easily develop, manage, and enforce Cooperative Enforcement.
With Cooperative Enforcement, a host that initiates a connection through a Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. is tested for compliance. This increases the integrity of the network because it prevents hosts with malicious software components to access the network.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. is tested for compliance. This increases the integrity of the network because it prevents hosts with malicious software components to access the network.
Cooperative Enforcement acts as a middle-man between hosts managed by an Endpoint Security Management Server and the Endpoint Security Management Server itself. It relies on the Endpoint Security Management Server compliance feature. It defines if a host is secure and can block connections that do not meet the defined prerequisites of software components.
|
|
Unauthorized |
|
|
Authorized |
-
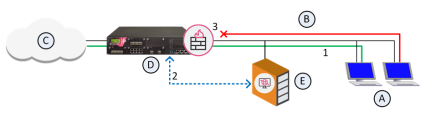
The Endpoint Security client (A) in the internal network (B) opens a connection to the internet (C) through a Security Gateway (D).
-
Cooperative Enforcement starts to work on the first server's reply to the client.
-
The Security Gateway sees the client's compliance in its tables and queries the Endpoint Security Management Server (E).
-
When a reply is received, a connection from a compliant host to the internet is allowed.
If the client is non-compliant and Cooperative Enforcement is not in Monitor-only mode, the connection is closed.
NAT Environments
Cooperative Enforcement is not supported by all the NAT configurations.
For Cooperative Enforcement to work in a NAT environment, the Security Gateway and the Endpoint Security Management Server must recognize the same IP address of a client. If NAT causes the IP address received by Security Gateway to be different than the IP address received by the Endpoint Security Management Server, Cooperative Enforcement will not work.
Configuring Cooperative Enforcement
To configure Cooperative Enforcement:
From the Security Gateway's Cooperative Enforcement page, click Authorize clients using Endpoint Security Server to enable Cooperative Enforcement.
-
Monitor Only The Security Gateway requests authorization from the Endpoint Security Management Server, but connections are not dropped. Hosts can connect while the Security Gateway grants authorization. The Security Gateway generates logs for unauthorized hosts. You can add unauthorized hosts to the host's exception list or make those hosts compliant in other ways.
If Monitor Only is not selected, Cooperative Enforcement works in Enforcement mode. The Endpoint Security Firewall blocks non-compliant host connections. For HTTP connections, the client is notified that its host is non-compliant. The user can change the computer to make compliant. For example, the user can upgrade the version of the Endpoint Security client.
-
Track unauthorized client status. Set a log, or alert option for the hosts that would be dropped if not in Monitor Only mode.
-
In the Endpoint Security Server Selection section, select which Endpoint Security Management Server is used:
-
To use this machine, select Use Endpoint Security Server installed on this machine.
-
To use another machine, select a server from Select Endpoint Security Server. Click New to create a new server.
-
-
In the Client Authorization. section, define exceptions for client authorization.
-
Check authorization of all clients - Get authorization from all clients.
-
Bypass authorization of the following clients - Allow clients in the selected groups to always connect, without authorization inspection. All other clients are inspected.
-
Check authorization only of the following clients - Inspect authorization of clients from the selected groups. All other clients bypass authorization.
-
Non-Compliant Hosts by Gateway View
The Non-Compliant Hosts by Gateway view lets you to see Host IP addresses by Endpoint Security Management Server compliance:
-
Authorized - Enables access to the internet. If a Security Gateway has Authorized status, it does not show in the Non-Compliant Hosts by Gateway view.
-
Unauthorized - The Endpoint Security client is not compliant and the host is not authorized.
-
Monitor Only mode - The Endpoint Security client has access to the internet, authorized or not.
-
Blocked mode - Blocks access to the internet.
-
-
No Endpoint Security client - The Security Gateway is not related to an Endpoint Security client.