Deploying a Security Gateway in Monitor Mode
Introduction to Monitor Mode
You can configure Monitor Mode on a single Check Point Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources.'s interface.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources.'s interface.
The Check Point Security Gateway listens to traffic from a Mirror Port or Span Port on a connected switch.
Use the Monitor Mode to analyze network traffic without changing the production environment.
The mirror port on a switch duplicates the network traffic and sends it to the Security Gateway with an interface configured in Monitor Mode to record the activity logs.
You can use the Monitor Mode:
-
To monitor the use of applications as a permanent part of your deployment
-
To evaluate the capabilities of the Software Blades:
-
The Security Gateway neither enforces any security policy
 Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection., nor performs any active operations (prevent / drop / reject) on the interface in the Monitor Mode.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection., nor performs any active operations (prevent / drop / reject) on the interface in the Monitor Mode. -
The Security Gateway terminates and does not forward all packets that arrive at the interface in the Monitor Mode.
-
The Security Gateway does not send any traffic through the interface in the Monitor Mode.
-
Benefits of the Monitor Mode include:
-
There is no risk to your production environment.
-
It requires minimal set-up configuration.
-
It does not require TAP equipment, which is expensive.
Example Topology for Monitor Mode
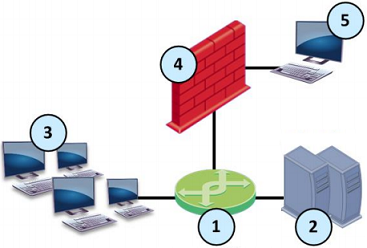
|
Item |
Description |
|---|---|
|
1 |
Switch with a mirror or SPAN port that duplicates all incoming and outgoing packets. The Security Gateway connects to a mirror or SPAN port on the switch. |
|
2 |
Servers. |
|
3 |
Clients. |
|
4 |
Security Gateway with an interface in Monitor Mode. |
|
5 |
Security Management Server |
Supported Software Blades in Monitor Mode
This table lists Software Blades and their support for the Monitor Mode in a single Security Gateway deployment.
|
|
Important - Check Point Cluster |
|
Software Blade |
Support for the Monitor Mode |
|---|---|
|
Firewall |
Fully supports the Monitor Mode. |
|
These protections and features do not work:
|
|
|
Does not support UserCheck. |
|
|
Does not support UserCheck. |
|
|
Does not support these:
|
|
|
Does not support these:
|
|
|
Does not support these:
|
|
|
Does not support the FTP inspection. |
|
|
Fully supports the Monitor Mode. |
|
|
Does not support the FTP inspection. |
|
|
Does not support the Monitor Mode. |
|
|
Does not support the Monitor Mode. |
|
|
Does not support the Monitor Mode. |
|
|
Does not support the Monitor Mode. |
Limitations in Monitor Mode
These features and deployments are not supported in Monitor Mode:
-
Passing production traffic through a Security Gateway, on which you configured Monitor Mode interface(s).
-
If you configure more than one Monitor Mode interface on a Security Gateway, you must make sure the Security Gateway does not receive the same traffic on the different Monitor Mode interfaces.
-
NAT rules.
-
HTTP / HTTPS proxy.
-
Anti-Virus in Traditional Mode.
-
User Authentication.
-
Client Authentication.
-
Check Point Active Streaming (CPAS).
-
Cluster deployment.
-
CloudGuard Gateways.
-
CoreXL
 Performance-enhancing technology for Security Gateways on multi-core processing platforms. Multiple Check Point Firewall instances are running in parallel on multiple CPU cores. Dynamic Dispatcher (sk105261).
Performance-enhancing technology for Security Gateways on multi-core processing platforms. Multiple Check Point Firewall instances are running in parallel on multiple CPU cores. Dynamic Dispatcher (sk105261). -
Setting the value of the kernel parameters "
psl_tap_enable" and "fw_tap_enable" to 1 (one) on-the-fly with the "fw ctl set int" command (Issue ID 02386641).
For more information, see sk101670: Monitor Mode on Gaia OS and SecurePlatform OS.

