Configuring a Single Security Gateway in Bridge Mode
|
|
Note - This procedure applies to both Check Point Appliances and Open Servers. |
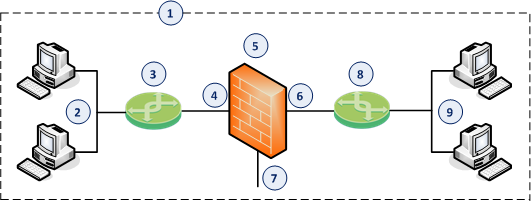
|
Item |
Description |
|---|---|
|
1 |
Network, which an administrator needs to divide into two Layer 2 segments. The Security Gateway |
|
2 |
First network segment. |
|
3 |
Switch that connects the first network segment to one bridged subordinate interface (4) on the Security Gateway in Bridge Mode. |
|
4 |
One bridged subordinate interface (for example, |
|
5 |
Security Gateway in Bridge Mode. |
|
6 |
Another bridged subordinate interface (for example, |
|
7 |
Dedicated Gaia |
|
8 |
Switch that connects the second network segment to the other bridged subordinate interface (6) on the Security Gateway in Bridge Mode. |
|
9 |
Second network segment. |
Procedure:
-
 Install the Security Gateway
Install the Security Gateway
Step
Instructions
1
Install the Gaia Operating System:
2
3
During the First Time Configuration Wizard, you must configure these settings:
-
In the Management Connection window, select the interface, through which you connect to Gaia operating system.
-
In the Internet Connection window, do not configure IP addresses.
-
In the Installation Type window, select Security Gateway and/or Security Management.
-
In the Products window:
-
In the Products section, select Security Gateway only.
-
In the Clustering section, clear Unit is a part of a cluster, type.
-
-
In the Dynamically Assigned IP window, select No.
-
In the Secure Internal Communication window, enter the applicable Activation Key (between 4 and 127 characters long).
-
-
 Configure the Bridge interface on the Security Gateway
Configure the Bridge interface on the Security Gateway
You configure the Bridge interface in either Gaia Portal
 Web interface for the Check Point Gaia operating system., or Gaia Clish
Web interface for the Check Point Gaia operating system., or Gaia Clish The name of the default command line shell in Check Point Gaia operating system. This is a restricted shell (role-based administration controls the number of commands available in the shell)..
The name of the default command line shell in Check Point Gaia operating system. This is a restricted shell (role-based administration controls the number of commands available in the shell).. Configuring the Bridge interface in Gaia Portal
Configuring the Bridge interface in Gaia Portal
Step
Instructions
1
In the left navigation tree, click Network Management > Network Interfaces.
2
Make sure that the subordinate interfaces, which you wish to add to the Bridge interface, do not have IP addresses assigned.
3
Click Add > Bridge.
To configure an existing Bridge interface, select the Bridge interface and click Edit.
4
On the Bridge tab, enter or select a Bridge Group ID (unique integer between 1 and 1024).
5
Select the interfaces from the Available Interfaces list and then click Add.

Notes:
-
Make sure that the subordinate interfaces do not have any IP addresses or aliases configured.
-
Do not select the interface that you configured as Gaia Management Interface.
-
A Bridge interface in Gaia can contain only two subordinate interfaces.
6
On the IPv4 tab, enter the IPv4 address and subnet mask.
You can optionally select the Obtain IPv4 Address automatically option.
7
On the IPv6 tab (optional), enter the IPv6 address and mask length.
You can optionally select the Obtain IPv6 Address automatically option.

Important - First, you must enable the IPv6 Support and reboot.
8
Click OK.

Note - The name of a Bridge interface in Gaia is "
br<Bridge Group ID>". For example, the name of a bridge interface with a Bridge Group ID of 5 is "br5". Configuring the Bridge interface in Gaia Clish
Configuring the Bridge interface in Gaia Clish
Step
Instructions
1
Connect to the command line on the Security Gateway.
2
Log in to Gaia Clish.
3
Make sure that the subordinate interfaces, which you wish to add to the Bridge interface, do not have IP addresses assigned:
show interface <Name of Interface> ipv4-addressshow interface <Name of Interface> ipv6-address4
Add a new bridging group:
add bridging group <Bridge Group ID 0 - 1024>5
Add subordinate interfaces to the new bridging group:
add bridging group <Bridge Group ID> interface <Name of First Subordinate Interface>add bridging group <Bridge Group ID> interface <Name of Second Subordinate Interface>
Notes:
-
Do not select the interface that you configured as Gaia Management Interface.
-
A Bridge interface in Gaia can contain only two subordinate interfaces.
6
Assign an IP address to the bridging group.
-
To assign an IPv4 address, run:
set interface <Name of Bridge Interface> ipv4-address <IPv4 Address> {subnet-mask <Mask> | mask-length <Mask Length>}You can optionally configure the bridging group to obtain an IPv4 Address automatically.
-
To assign an IPv6 address, run:
set interface <Name of Bridge Interface> ipv6-address <IPv6 Address> mask-length <Mask Length>You can optionally configure the bridging group to obtain an IPv6 Address automatically.

Important - First, you must enable the IPv6 Support and reboot.
7
Save the configuration:
save config
Note - The name of a Bridge interface in Gaia is "
br<Bridge Group ID>". For example, the name of a bridge interface with a Bridge Group ID of 5 is "br5". -
-
 Configure the Security Gateway object in SmartConsole
Configure the Security Gateway object in SmartConsole
You can configure the ClusterXL object in either Wizard Mode, or Classic Mode.
 Configuring the Security Gateway object in Wizard Mode
Configuring the Security Gateway object in Wizard Mode
Step
Instructions
1
Connect with SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. to the Security Management Server
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. to the Security Management Server Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. or Domain Management Server
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. or Domain Management Server Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. that should manage this Security Gateway.
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. that should manage this Security Gateway.2
From the left navigation panel, click Gateways & Servers.
3
Create a new Security Gateway object in one of these ways:
-
From the top toolbar, click the New (
 ) > Gateway.
) > Gateway. -
In the top left corner, click Objects menu > More object types > Network Object > Gateways and Servers > New Gateway.
-
In the top right corner, click Objects Pane > New > More > Network Object > Gateways and Servers > Gateway.
4
In the Check Point Security Gateway Creation window, click Wizard Mode.
5
On the General Properties page:
-
In the Gateway name field, enter the applicable name for this Security Gateway object.
-
In the Gateway platform field, select the correct hardware type.
-
In the Gateway IP address section, select Static IP address and configure the same IPv4 and IPv6 addresses that you configured on the Management Connection page of the Security Gateway's First Time Configuration Wizard.
Make sure the Security Management Server or Multi-Domain Server
 Dedicated Check Point server that runs Check Point software to host virtual Security Management Servers called Domain Management Servers. Synonym: Multi-Domain Security Management Server. Acronym: MDS. can connect to these IP addresses.
Dedicated Check Point server that runs Check Point software to host virtual Security Management Servers called Domain Management Servers. Synonym: Multi-Domain Security Management Server. Acronym: MDS. can connect to these IP addresses. -
Click Next.
6
On the Trusted Communication page:
-
Select the applicable option:
-
If you selected Initiate trusted communication now, enter the same Activation Key you entered during the Security Gateway's First Time Configuration Wizard.
-
If you selected Skip and initiate trusted communication later, make sure to follow Step 7.
-
-
Click Next.
7
On the End page:
-
Examine the Configuration Summary.
-
Select Edit Gateway properties for further configuration.
-
Click Finish.
Check Point Gateway properties window opens on the General Properties page.
8
If during the Wizard Mode, you selected Skip and initiate trusted communication later:
-
The Secure Internal Communication field shows Uninitialized.
-
Click Communication.
-
In the Platform field:
-
Select Open server / Appliance for all Check Point models 3000 and higher.
-
Select Open server / Appliance for an Open Server
 Physical computer manufactured and distributed by a company, other than Check Point..
Physical computer manufactured and distributed by a company, other than Check Point..
-
-
Enter the same Activation Key you entered during the Security Gateway's First Time Configuration Wizard.
-
Click Initialize.
Make sure the Certificate state field shows Established.
-
Click OK.
9
On the General Properties page:
-
On the Network Security tab, enable the applicable Software Blades.
-
On the Threat Prevention tab, enable the applicable Software Blades.

Important - See the Supported Software Blades in Bridge Mode and Limitations in Bridge Mode sections in Deploying a Security Gateway or a ClusterXL in Bridge Mode.
10
On the Network Management page, configure the Topology of the Bridge interface.

Notes:
-
If a Bridge interface connects to the Internet, then set the Topology to External.
-
If you use this Bridge Security Gateway object in Access Control Policy rules with Internet objects, then set the Topology to External.
11
Click OK.
12
Publish the SmartConsole session.
13
This Security Gateway object is now ready to receive the Security Policy
 Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection..
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection.. Configuring the Security Gateway object in Classic Mode
Configuring the Security Gateway object in Classic Mode
Step
Instructions
1
Connect with SmartConsole to the Security Management Server or Domain Management Server that should manage this Security Gateway.
2
From the left navigation panel, click Gateways & Servers.
3
Create a new Security Gateway object in one of these ways:
-
From the top toolbar, click the New (
 ) > Gateway.
) > Gateway. -
In the top left corner, click Objects menu > More object types > Network Object > Gateways and Servers > New Gateway.
-
In the top right corner, click Objects Pane > New > More > Network Object > Gateways and Servers > Gateway.
4
In the Check Point Security Gateway Creation window, click Classic Mode.
Check Point Gateway properties window opens on the General Properties page.
5
In the Name field, enter the applicable name for this Security Gateway object.
6
In the IPv4 address and IPv6 address fields, configure the same IPv4 and IPv6 addresses that you configured on the Management Connection page of the Security Gateway's First Time Configuration Wizard.
Make sure the Security Management Server or Multi-Domain Server can connect to these IP addresses.
7
Establish the Secure Internal Communication (SIC
 Secure Internal Communication. The Check Point proprietary mechanism with which Check Point computers that run Check Point software authenticate each other over SSL, for secure communication. This authentication is based on the certificates issued by the ICA on a Check Point Management Server.) between the Management Server and this Security Gateway:
Secure Internal Communication. The Check Point proprietary mechanism with which Check Point computers that run Check Point software authenticate each other over SSL, for secure communication. This authentication is based on the certificates issued by the ICA on a Check Point Management Server.) between the Management Server and this Security Gateway:-
Near the Secure Internal Communication field, click Communication.
-
In the Platform field:
-
Select Open server / Appliance for all Check Point models 3000 and higher.
-
Select Open server / Appliance for an Open Server.
-
-
Enter the same Activation Key you entered during the Security Gateway's First Time Configuration Wizard.
-
Click Initialize.
-
Click OK.
If the Certificate state field does not show
Established, perform these steps:-
Connect to the command line on the Security Gateway.
-
Make sure there is a physical connectivity between the Security Gateway and the Management Server (for example, pings can pass).
-
Run:
cpconfig -
Enter the number of this option:
Secure Internal Communication -
Follow the instructions on the screen to change the Activation Key.
-
In SmartConsole, click Reset.
-
Enter the same Activation Key you entered in the
cpconfigmenu. -
In SmartConsole, click Initialize.
8
In the Platform section, select the correct options:
-
In the Hardware field:
-
If you install the Security Gateway on a Check Point Appliance, select the correct appliances series.
-
If you install the Security Gateway on an Open Server, select Open server.
-
-
In the Version field, select R81.
-
In the OS field, select Gaia.
9
Enable the applicable Software Blades:
-
On the Network Security tab.
-
On the Threat Prevention tab.

Important - See the Supported Software Blades in Bridge Mode and Limitations in Bridge Mode sections in Deploying a Security Gateway or a ClusterXL in Bridge Mode.
10
On the Network Management page, configure the Topology of the Bridge interface.

Notes:
-
If a Bridge interface connects to the Internet, then set the Topology to External.
-
If you use this Bridge Security Gateway object in Access Control Policy rules with Internet objects, then set the Topology to External.
11
Click OK.
12
Publish the SmartConsole session.
13
This Security Gateway object is now ready to receive the Security Policy.
-
-
 Configure the applicable Security Policies for the Security Gateway in SmartConsole
Configure the applicable Security Policies for the Security Gateway in SmartConsole
Step
Instructions
1
Connect with SmartConsole to the Security Management Server or Domain Management Server that manages this Security Gateway.
2
From the left navigation panel, click Security Policies.
3
Create a new policy and configure the applicable layers:
-
At the top, click the + tab (or press CTRL T).
-
On the Manage Policies tab, click Manage policies and layers.
-
In the Manage policies and layers window, create a new policy and configure the applicable layers.
-
Click Close.
-
On the Manage Policies tab, click the new policy you created.
4
Create the applicable rules in the Access Control and Threat Prevention policies.

Important - See the Supported Software Blades in Bridge Mode and Limitations in Bridge Mode sections in Deploying a Security Gateway or a ClusterXL in Bridge Mode.
5
Install the Access Control Policy on the Security Gateway object.
5
Install the Threat Prevention Policy on the Security Gateway object.
-
For more information, see the:
-
Applicable Administration Guides on the R81 Home Page.
