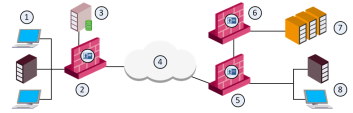
Distributed Enterprise with Branch Offices
Security Challenge
Distributed enterprises have a potential risk of malware and viruses that go from remote branch offices over VPN links to the corporate internal networks.
In addition, you must provide authorized access to users who come from remote branch offices and request an access to the Data Center and the Internet.
Configuration Scenario
|
|
Best Practice - We recommend that you configure Security Gateway |
-
At remote branch offices, you can configure low capacity Security Gateway because of a relatively low number of users.
You configure the remote branch Security Gateway in IP Routing Mode and establish a VPN link to the corporate Security Gateway. The remote branch Security Gateways now works as a perimeter Firewall and VPN gateway.
 >
>
Best Practice - At the corporate headquarters, we recommend that you configure Data Center Security Gateway to protect access to Data Center resources and applications, and to a perimeter Security Gateway. You can install the Data Center Security Gateway in Bridge Mode
 Security Gateway or Virtual System that works as a Layer 2 bridge device for easy deployment in an existing topology. to prevent changes to the current network.
Security Gateway or Virtual System that works as a Layer 2 bridge device for easy deployment in an existing topology. to prevent changes to the current network. -
The local branch office Security Gateway identifies users from the branch office, learns their identities, and then connects to the corporate network over VPN.
-
The branch office Security Gateway shares these user identities with the headquarters' internal and perimeter Security Gateway. When a user from a branch office attempts to connect to the Data Center, the Security Gateway identifies this user at the headquarters Data Center without the need for additional authentication.
Configuration
-
Select a Security Gateway in accordance with the performance guideline for your remote branch offices.
-
Configure the Security Gateway at the branch offices in Routing Mode. Make a specified VPN site-to-site if necessary.
-
Configure Security Gateway inline at the Data Center. We recommend to use Bridge Mode.
-
Configure a Security Gateway at the perimeter that protects the internal network in Routing Mode. This perimeter Security Gateway can serve as a VPN Security Gateway for branch offices.
 >
>
Best Practice
-
If you have Active Directory domain controllers replicated across your branch offices, make sure that local Security Gateway can connect to the domain controller.
-
If you do not have a local domain controller, make sure that the Security Gateway has an access to the headquarters' internal domain controller over VPN.
-
-
Enable Identity Awareness and select the appropriate methods to get identity.
-
Create an Access Role
 Access Role objects let you configure network access according to: Networks, Users and user groups, Computers and computer groups, Remote Access Clients. After you activate the Identity Awareness Software Blade, you can create Access Role objects and use them in the Source and Destination columns of Access Control Policy rules. and apply the roles in the Security Policy
Access Role objects let you configure network access according to: Networks, Users and user groups, Computers and computer groups, Remote Access Clients. After you activate the Identity Awareness Software Blade, you can create Access Role objects and use them in the Source and Destination columns of Access Control Policy rules. and apply the roles in the Security Policy Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. on the branch office Security Gateway, perimeter and Data Center Security Gateway.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. on the branch office Security Gateway, perimeter and Data Center Security Gateway. -
Share identities between the branch offices with the headquarters and Data Center Security Gateway:
-
Go to the Identity Awareness tab.
-
Select Get identities from other gateways and Share local identities with other gateways.
-
|
|
Best Practice We recommend these configurations:
|