Configuring Clients for Non-Persistent Desktops
General
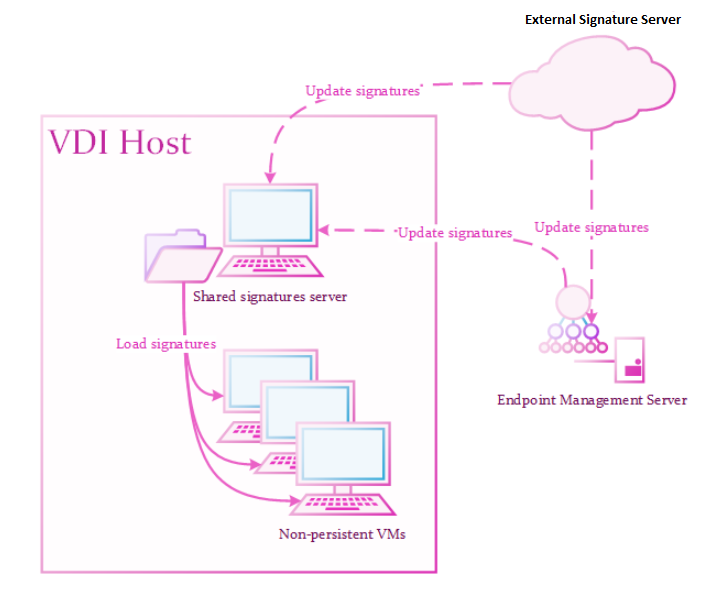
The Solution:
-
One or more Signature Servers responsible to store the latest Anti-Malware
 A component on Endpoint Security Windows clients. This component protects clients from known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. signatures in a shared location.
A component on Endpoint Security Windows clients. This component protects clients from known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. signatures in a shared location. -
Many specially configured clients that load signatures from the shared folder.
-
If the shared signatures server is not available, the client uses signatures from the golden image.
|
|
Note - All endpoints connected to the Shared Signature Server must be on the same domain. |
Recommended Steps:
-
Configure a signature server machine.
-
Configure a client machine (golden image).
-
Create a test pool.
-
Deploy the production pool.
Shared Signatures Server
A Shared Signatures Server:
-
Installs as a regular Endpoint Security Client and becomes a "signature server" later.
-
Responsible for holding the latest Anti-Malware signatures.
The signatures store in a read-only shared folder and update according to policy.
-
Must run on a persistent virtual machine, preferably on the same storage as the clients.
-
Must connect to the Endpoint Policy Server
 Endpoint Policy Server improves performance in large environments by managing most communication with the Endpoint Security clients. Managing the Endpoint Security client communication decreases the load on the Endpoint Security Management Server, and reduces the bandwidth required between sites. The Endpoint Policy Server handles heartbeat and synchronization requests, Policy downloads, Anti-Malware updates, and Endpoint Security client logs. or the Internet to update signatures.
Endpoint Policy Server improves performance in large environments by managing most communication with the Endpoint Security clients. Managing the Endpoint Security client communication decreases the load on the Endpoint Security Management Server, and reduces the bandwidth required between sites. The Endpoint Policy Server handles heartbeat and synchronization requests, Policy downloads, Anti-Malware updates, and Endpoint Security client logs. or the Internet to update signatures.
Configuring the Signatures Server
For the Endpoint Security Clients version E84.20 (and higher), you can configure the Signature Server with a policy.
-
Create a new Virtual Group.
-
Assign a Golden Image machine to the new group.
-
From the left navigation panel, click Policy.
-
In the left pane, click Threat Prevention.
-
In the policy, clone the applicable Threat Prevention rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session..
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session.. -
Assign the new Threat Prevention rule to the new Virtual Group.
-
In the right pane, click the Web & Files Protection tab.
-
Scroll down and click the Advanced Settings button.
-
From the left tree, click Files Protection > Signature.
-
In the Shared Signature Server section, select the “Set as shared signature server” and enter the local path of the folder.
Example:
C:\Signatures
Note - If the folder does not exist, the endpoint creates it automatically.
-
Configure the applicable frequency in the Frequency section.
-
Click OK.
-
At the bottom, click Save.
-
At the top, click Install Policy.
Setup Validation
Wait 20 minutes to make sure:
-
Anti-Malware Signatures version is current.
-
Shared Signatures folder exists with Anti-Malware signatures.
Important - If the folder is empty, the setup is not valid.
Client Machine Configuration for Non-Persistent Desktops
Creating a Basic Golden Image for Non-Persistent Desktops
See Basic Golden Image Settings for the procedure to create a basic golden image.
Configuring the Client Machine
For the Endpoint Security Clients version E84.20 (and higher), you can configure up the client machines (the golden image) by policy.
-
Disable the Anti-Malware Periodic Scan.
See Appendix.
-
Configure signature source for the VDI client.
 Procedure
Procedure
-
Create a new Virtual Group.
-
Assign a Golden Image machine to the new group.
-
From the left navigation panel, click Policy.
-
In the left pane, click Threat Prevention.
-
In the policy, clone the applicable Threat Prevention rule.
-
Assign the new Threat Prevention rule to the new Virtual Group.
-
In the right pane, click the Web & Files Protection tab.
-
Scroll down and click the Advanced Settings button.
-
From the left tree, click Files Protection > Signature.
-
In the Shared Signature Server section, enter the UNC of the shared folder.
Example:
\\192.168.18.5\Signatures -
Configure the applicable frequency.
-
Click OK.
-
At the bottom, click Save.
-
At the top, click Install Policy.
-
|
|
Important:
|
Post Setup Actions
-
Make sure the Shared Signatures folder is accessible from the golden image and the folder has signatures.
-
Make sure the Anti-Malware signatures are current.
-
Scan for malwares with the latest signatures.
Creating a Pool for Non-Persistent Desktops
|
|
Note - Check Point recommends that each created pool will use a different machine naming pattern. This will prevent situations where Management Server |
VMware Horizon Key Points
This procedure is mandatory to create supported Horizon pools for Non-Persistent Virtual Desktops.
-
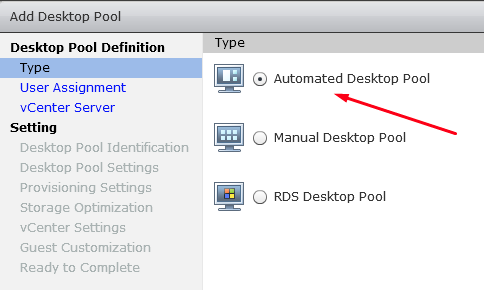
In VMware Horizon, choose Automated Desktop Pool in the Type panel of Add Desktop Pool.
-
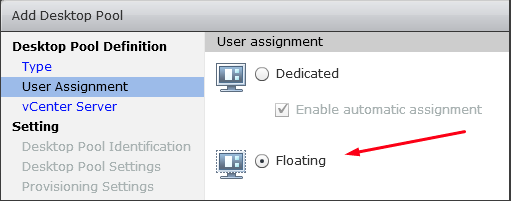
In the User Assignment panel, choose Floating.
-
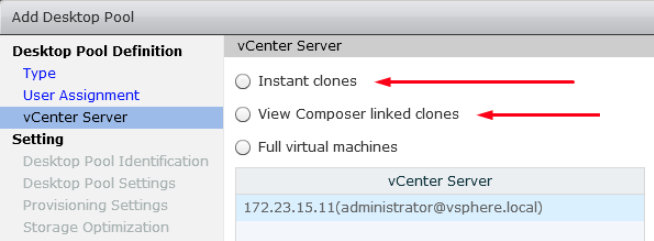
In the vCenter Server panel, choose Instant Clones or Linked Clones.
-
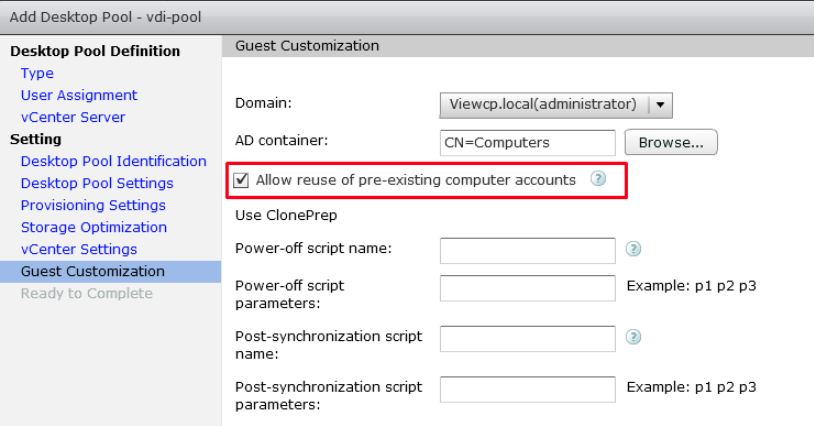
In the Guest Customization panel, select Allow reuse of pre-existing computer account.
Citrix Xen-Desktop Key Points
-
When you select the Operating System type, use Single-Session OS.
-
When you select the User Experience type, use a non-dedicated desktop experience.
Pool Validation
Access a few cloned machines and make sure that:
-
Applicable Software Blades run.
-
Anti-Malware Signatures are current.
-
Machines appear on the Server User Interface.
Disabling the Anti-Malware Periodic Scan
"Anti-Malware Scan Storms" can occur when several anti-virus scans run simultaneously on multiple virtual machines on the same physical server. In such situation, a degradation of system performance is possible, which can affect disk I/O and CPU usage. It is then recommended that you disable the Anti-Malware periodic scan:
-
Go to the Policy Page.
-
In the right pane, click the Web & Files Protection tab.
-
Scroll down and click the Advanced Settings button.
-
From the left tree, select Files Protection > Scan.
-
In the Perform Periodic Scan Every field, select Never.
Software Blades for Non-Persistent Desktops
The Endpoint Security client capabilities for non-persistent virtual desktops are:
-
Anti-Malware
-
Fully supported when configured with the Shared Signatures Server.
-
-
Compliance, Firewall and Application Control, Remote Access VPN, and URL Filtering
-
Fully supported.
-
-
Forensics
-
Partially supported.
-
The Forensics database contains data for the current session.
-
Forensics Reports generate as usual.
-
-
-
Threat Emulation and Anti-Exploit
-
Partially supported.
-
Signatures are not in cache.
-
Signatures download for each new instance.
-
-
-
Anti-Bot
-
Partially supported.
-
Signatures are not in cache.
- Signatures download for each new instance.
-
Cached data (such as the URLs checked against Threat-Cloud and Detection List) are lost on logoff.
-
-
-
Ransomware "Honeypots"
-
Partially supported.
-
Part of the Golden Image.
-
-
-
Behavioral Guard
-
Partially supported.
-
Signatures are not in cache.
-
Signatures download for each new instance.
-
-
-
Full Disk Encryption and Capsule Docs
-
Not supported for non-persistent desktops.
-
-
Media Encryption & Port Protection
-
Fully supported with VMware Horizon running the Harmony Endpoint client version E86.40 and higher.
-
Fully supported with Citrix Provisioning
 Check Point Software Blade on a Management Server that manages large-scale deployments of Check Point Security Gateways using configuration profiles. Synonyms: SmartProvisioning, SmartLSM, Large-Scale Management, LSM. Services (PVS) running the Harmony Endpoint client version E86.50 and higher.
Check Point Software Blade on a Management Server that manages large-scale deployments of Check Point Security Gateways using configuration profiles. Synonyms: SmartProvisioning, SmartLSM, Large-Scale Management, LSM. Services (PVS) running the Harmony Endpoint client version E86.50 and higher.
-

