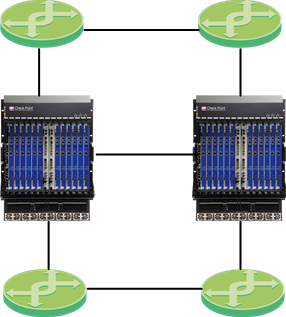
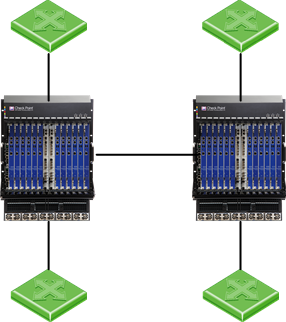
Dual Chassis in Bridge Mode
This chapter describes how to deploy Dual Chassis in Layer 2 Bridge mode![]() Security Gateway or Virtual System that works as a Layer 2 bridge device for easy deployment in an existing topology..
Security Gateway or Virtual System that works as a Layer 2 bridge device for easy deployment in an existing topology..
Bridge Mode Topologies
Active/Active Bridge Mode supports these topologies:
BPDU
The BDPU maximum age timer controls the maximum length of time that passes before a bridge port saves its configuration BPDU information.
The default time it takes to reach a chassis failover is 20 seconds. It is possible to configure be configure this time to a value from 6 to 40 seconds.
Example for Cisco switches:
Use the "spanning-tree vlan" command on each VLAN to configure the BDPU maximum age timer. For more information, see Cisco documentation.
Configuring Bridge Interfaces in Gateway Mode
Description
Use the applicable commands in Gaia gClish![]() The name of the global command line shell in Check Point Gaia operating system for Security Gateway Modules. Commands you run in this shell apply to all Security Gateway Module in the Security Group. to work with Bridge interfaces.
The name of the global command line shell in Check Point Gaia operating system for Security Gateway Modules. Commands you run in this shell apply to all Security Gateway Module in the Security Group. to work with Bridge interfaces.
For more information, see the R81 Scalable Platforms Gaia Administration Guide > Chapter Network Management > Section Network Interfaces - Subsection Bridge Interfaces.
Example
Configuring Bridge Interfaces in VSX Mode
Configure a Virtual System in Bridge Mode when you first create its object.
For more information, see the R81 Scalable Platforms VSX Administration Guide.
To configure an existing Virtual System in Active/Standby Bridge Mode:
Configuring Virtual Systems in Bridge Mode to Forward Non-IP Protocols
|
Step |
Instructions |
|
|---|---|---|
|
1 |
Connect to the command line on the Security Group. |
|
|
2 |
Log in to the Expert mode. |
|
|
3 |
Create the required empty file on all Security Group Members:
|
|
|
4 |