Monitoring GPRS Network Security
To effectively manage your network and make informed decisions, you need to gather information on the network's traffic patterns. If you experience connectivity or security related problems, you need to be able to identify changes in the traffic. Carrier Security provides a set of tools that address the special needs of cellular networks.
GTP Tracking Logs and Alerts
Carrier Security records cellular-specific information of GTP![]() GPRS Tunnel Protocol. signaling activity, including APN
GPRS Tunnel Protocol. signaling activity, including APN![]() Access Point Name - the identifier of an external packet data network., IMSI
Access Point Name - the identifier of an external packet data network., IMSI![]() International Mobile Subscriber Identity - a user's unique ID in GSM/GPRS networks., Selection Mode, GSN
International Mobile Subscriber Identity - a user's unique ID in GSM/GPRS networks., Selection Mode, GSN![]() GPRS Support Node. addresses and more. The information recorded in these logs can help you determine why certain GTP traffic may be dropped or rejected, and to decide if whether to adjust the Security Policy
GPRS Support Node. addresses and more. The information recorded in these logs can help you determine why certain GTP traffic may be dropped or rejected, and to decide if whether to adjust the Security Policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. to accept that traffic.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. to accept that traffic.
The Carrier Security GTP Inspection Gateway generates a wide range of detailed security alerts in the event of protocol and Security Policy violations, including PDU![]() Protocol Data Unit - a packet. details, network information and protocol violation type. Carrier Security also provides GTP-specific alerts on malformed packets and malicious activity. For information on setting the alert type, see Configuring Monitoring
Protocol Data Unit - a packet. details, network information and protocol violation type. Carrier Security also provides GTP-specific alerts on malformed packets and malicious activity. For information on setting the alert type, see Configuring Monitoring
Note - As in all security rules, you must set the tracking option of the rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. to Log if you want to record GTP activity.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. to Log if you want to record GTP activity.
Recording GTP Data from Unmatched PDUs
Carrier Security can record GTP traffic that is not matched by a GTP rule in the rule base![]() All rules configured in a given Security Policy. Synonym: Rulebase.. Normally, traffic that is not matched is logged in the general log as a simple
All rules configured in a given Security Policy. Synonym: Rulebase.. Normally, traffic that is not matched is logged in the general log as a simple Drop. Carrier Security provides a tool for capturing this data with the special GTP-related fields that can help to discover the cause of these drops. To configure this feature, see: Configuring Monitoring
GTP Accounting
By setting a GTP user traffic rule to Log, Carrier Security generates a log entry for every terminated PDP context![]() Information sets held in MS and GSNs for a specific PDP address. that matches on the rule. The log records the total number of user packets (
Information sets held in MS and GSNs for a specific PDP address. that matches on the rule. The log records the total number of user packets (n_pdu) and bytes (n_byte) transferred in the user plane during the PDP![]() Packet Data Protocol - a network protocol used by an external packet data network (usually IP). context. Carrier Security issues logs for the following events:
Packet Data Protocol - a network protocol used by an external packet data network (usually IP). context. Carrier Security issues logs for the following events:
-
PDP context/session delete
-
Tunnel expiration
-
Tunnel recreation
-
Active Gateway goes down (when in High Availability mode)
Excessive Logs Protection
Due to the small packet nature of cellular communications, Carrier Security records a vast amount of data each day, far more than a typical Check Point firewall. This data collection is essential to accurately diagnose network status, and to troubleshoot network errors.
This intensive logging activity could make some systems more vulnerable to Denial of Service (DoS) attacks. Carrier Security protects against this type of attack by setting a similar logging threshold, above which it does not generate similar logs. This feature is configurable. See gtp_loggrace in Adjusting Settings with Database Tool (GuiDBEdit Tool).
The default is every 10 seconds.
Monitor-Only Mode
Monitor-Only Mode tracks certain unauthorized traffic without blocking it. While in this mode, the firewall continues to inspect GTP traffic, but does not enforce any of the GTP related protections. It does continue to enforce GTP-related security rules, log GTP-related activity, and issue GTP error logs and alerts. Monitor-Only Mode enables operators to preview the results of changes to global properties and settings concerning GTP inspection. This mode is helpful in preventing unanticipated behavior when phasing in Carrier Security for the first time, and whenever changes are made to the global properties.
After a careful review of the logs and ensuring that the changes do not impede legitimate cellular traffic, the cellular operator can turn off Monitor-Only Mode, and the firewall can commence blocking malicious GTP traffic.
Carrier Security follows the GTP tunnels and keeps their state as it would in regular operation mode. Therefore you can smoothly switch Monitor-Only Mode on and off - all tunnel information continues to exist in both modes, and no tunnels are lost in transition.
For configuration information, see gtp_monitor_mode in: Adjusting Settings with Database Tool (GuiDBEdit Tool)
Configuring Monitoring
-
Produce extended log on unmatched PDUs logs GTP packets not matched by previous rules with Carrier Security's extended GTP-related log fields. These logs appear brown and their Action attribute is empty. The default setting is
checked. -
Protocol violation track option allows you to set the appropriate track or alert option to be used when a protocol violation (malformed packet) is detected. The default setting is
Log.
Monitoring GSN Handover Group Limits
You can enable these options in Global Properties > Carrier Security > Track.
Use this command to see tunnel use for handover groups. Run the command in the Expert mode on the Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources..
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources..
Syntax
fw gtp ho_groups [-s { name | tunnels | limit | util } [-r]] [-m <lines>]
fw gtp ho_groups -g <name>
fw gtp ho_groups -l
fw gtp ho_groups -h
|
Parameter |
Description |
|---|---|
|
|
Sort the output by tunnel name, assigned limit or tunnel utilization |
|
|
Sort the output in in reverse alphabetical order |
|
|
Show, at most, the specified number of lines |
|
|
Show only the handover group names (no data) |
|
|
Show only the specified handover group |
Example:
|
|
SNMP Extensions for GTP Statistics
Carrier Security can be configured to send SNMP![]() Simple Network Management Protocol runs over TCP/IP and is used to control and manage IP gateways and other network functions. polling data and traps. Various cellular-specific statistics, such as the number of PDP contexts created and deleted, can be polled by SNMP monitoring stations. Alerts and logs can also be set via GTP-aware security rules to send SNMP traps to a monitoring station when events that require attention occur.
Simple Network Management Protocol runs over TCP/IP and is used to control and manage IP gateways and other network functions. polling data and traps. Various cellular-specific statistics, such as the number of PDP contexts created and deleted, can be polled by SNMP monitoring stations. Alerts and logs can also be set via GTP-aware security rules to send SNMP traps to a monitoring station when events that require attention occur.
The Check Point MIB![]() Management Information Base - a collection of managed objects defined by their attributes and visible to the network management system. is a data file that contains the collection of Check Point's SNMP-manageable network devices. It contains SNMP extensions for Carrier Security.
Management Information Base - a collection of managed objects defined by their attributes and visible to the network management system. is a data file that contains the collection of Check Point's SNMP-manageable network devices. It contains SNMP extensions for Carrier Security.
For more information about SNMP and MIB, see the R81 Gaia Administration Guide.
The Check Point MIB file can be found on the Security Gateway in the $CPDIR/lib/snmp/ directory.
Understanding Check Point OIDs:
-
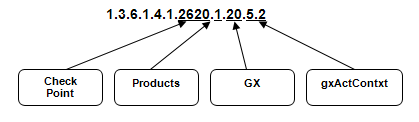
Prefix OID for Check Point root is: 1.3.6.1.4.1.2620. (Check Point is 2620)
-
Prefix OID for GX root is: 1.3.6.1.4.1.2620.1.20. (Products is 1, GX is 20)
GX SNMP Counters Tree
GX (20)
gxProdVerMajor (5.2)
gxProdVerMinor (5.3)
gxBuild (5.4)
gxInfo(1)
gxProdName (1)
gxProdVersion (2)
gxCreateInfo(5)
gxCreateSinceInstall (1)
gxActContxt (2)
gxDropPlicyCreate (3)
gxDropMalformedReqCreate (4)
gxDropMalformedRespCreate (5)
gxExpiredCreate (6)
gxBadCauseCreate (7)
gxSecondaryNsapiEntries (8)
gxDeleteInfo (6)
gxDeleteSinceInstall (1)
gxDropOutOfContxtDelete (2)
gxDropMalformedReqDelete (3)
gxDropMalformedRespDelete (4)
gxExpiredDelete (5)
gxBadCauseDelete (6)
gxUpdateInfo (7)
gxUpdateSinceInstall (1)
gxDropOutOfContxtUpdate (2)
gxDropMalformedReqUpdate (3)
gxDropMalformedRespUpdate (4)
gxExpiredUpdate (5)
gxBadCauseUpdate (6)
gxPathMngInfo (8)
gxEchoSinceInstall (1)
gxVnspSinceInstall (2)
gxDropPolicyEcho (3)
gxDropMalformedReqEcho (4)
gxDropMalformedRespEcho (5)
gxExpiredEcho (6)
gxDropVnsp (7)
gxGtpPathEntries (8)
gxGpduInfo (9)
gxGpdu1MinAvgRate (1)
gxDropOutOfContxtGpdu (2)
gxDropAnti-spoofingGpdu (3)
gxDropMs-MsGpdu (4)
gxDropBadSeqGpdu (5)
gxDropBadGpdu (6)
gxGpduExpiredTunnel (7)
Example
gxActContxt SNMP counter OID is: (GX Active Contexts - gtp_tunnels counter)
Testing SNMP Functionality
To test the Carrier Security's SNMP internal functionality, use this command on the module side:
gxstattest <oid>
