Directional VPN Enforcement
Overview of Directional VPN
When a VPN community is selected in the VPN column of the Security Policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. Rule Base
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. Rule Base![]() All rules configured in a given Security Policy. Synonym: Rulebase., the source and destination IP addresses can belong to any of the Security Gateways in the community. In other words, the traffic is bidirectional; any of the Security Gateways can be the source of a connection, any of the Security Gateways can be the destination endpoint. But what if the administrator (in line with the company's security policy) wished to enforce traffic in one direction only? Or to allow encrypted traffic to or from Security Gateways not included in the VPN community? To enable enforcement within VPN communities, VPN implements Directional VPN.
All rules configured in a given Security Policy. Synonym: Rulebase., the source and destination IP addresses can belong to any of the Security Gateways in the community. In other words, the traffic is bidirectional; any of the Security Gateways can be the source of a connection, any of the Security Gateways can be the destination endpoint. But what if the administrator (in line with the company's security policy) wished to enforce traffic in one direction only? Or to allow encrypted traffic to or from Security Gateways not included in the VPN community? To enable enforcement within VPN communities, VPN implements Directional VPN.
Directional VPN specifies where the source address must be, and where the destination address must be. In this way, enforcement can take place:
-
Within a single VPN community
-
Between VPN communities
Directional Enforcement within a Community
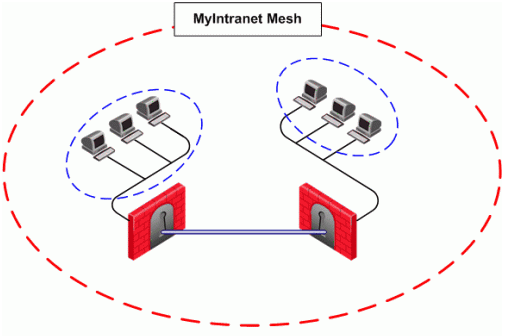
The example figure below shows a simple meshed VPN community called MyIntranet.
VPN traffic within the MyIntranet Mesh is bidirectional. Meaning, either of the Security Gateways (or the hosts behind the Security Gateways in the VPN domains) can be the source or destination address for a connection.
|
Source |
Destination |
VPN |
Service |
Action |
Track |
|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
The match conditions are represented by a series of compound objects. The match conditions enforce traffic in the following directions:
-
To and from the VPN Community
 A named collection of VPN domains, each protected by a VPN gateway. via VPN routing (MyIntranet => MyIntranet)
A named collection of VPN domains, each protected by a VPN gateway. via VPN routing (MyIntranet => MyIntranet) -
From the Community to the local VPN domains (MyIntranet =>internal_clear)
-
From the local VPN domains to the VPN community (internal_clear => MyIntranet)
Configurable Objects in a Direction
The table below shows all the objects that can be configured in a direction, including three new objects created for Directional VPN:
|
Name of Object |
Description |
|---|---|
|
Remote Access |
|
|
Site to Site VPN |
Regular Star or Mesh VPN community |
|
Any Traffic |
Any traffic |
|
All_GwToGw |
All Site to Site VPN |
|
All_Communities |
All Site to Site and Remote Access VPN communities |
|
External_clear |
For traffic outside the VPN community |
|
Internal_clear |
For traffic between local domains within the VPN community |
Note - Clear text connections originating from these objects are not subject to enforcement:
-
Any Traffic
-
External_clear
-
Internal_clear
There is no limit to the number of VPN directions that you can configure in a single rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session.. In general, if you have many directional enforcements, consider replacing them with a standard bidirectional condition.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session.. In general, if you have many directional enforcements, consider replacing them with a standard bidirectional condition.
Directional Enforcement between Communities
VPN Directional Enforcement can take place between two VPN communities. In this case, one Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. must be configured as a member of both communities and the enforcement point between them. Every other peer Security Gateway in both communities must have a route entry to the enforcement point Security Gateway in its
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. must be configured as a member of both communities and the enforcement point between them. Every other peer Security Gateway in both communities must have a route entry to the enforcement point Security Gateway in its $FWDIR/conf/vpn_route.conf file.
To add a route entry to the enforcement point Security Gateway:
On the management module of each Security Gateway in the community (except for the enforcement point Security Gateway), add an entry in the $FWDIR/conf/vpn_route.conf file:
|
Destination |
Next hop router interface |
Install on |
|---|---|---|
|
< |
< |
< |
These are the variables in the entry:
-
destination_community_obj- a network object for the combined encryption domain of the community -
enforcement_point_gw- the Security Gateway that is a member of both communities and transfers the encrypted traffic between them -
managed_FW_object- all community members that are managed by the management module
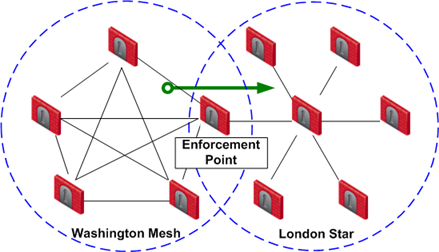
In the example below, Washington is a Mesh community, and London is a VPN Star.
The directional VPN rule below must be configured for the enforcement point Security Gateway in the Access Control Policy Rule Base:
|
Source |
Destination |
VPN |
Services & Applications |
Action |
|---|---|---|---|---|
|
|
|
Washington => London |
|
|
The rule is applied to all VPN traffic that passes through the enforcement point Security Gateway between the Washington and London communities. If a connection is opened from a source in the Washington Mesh, and the destination is in the London Star, the connection is allowed. Otherwise, the connection is denied.
Note - The Directional Enforcement applies only to the first packet of a connection. If the connection is permitted, the following packets of this connection are also permitted, including the packets in the opposite direction.
Configuring Directional VPN Within a Community
To configure Directional VPN within a community:
-
In SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., click > Global properties > VPN > Advanced.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., click > Global properties > VPN > Advanced. -
Select Enable VPN Directional Match in VPN Column.
-
Click OK.
-
In SmartConsole, from the left navigation panel, click Security Policies.
-
In the Access Control section, click in the applicable rule.
-
In the VPN column of this rule, select Directional Match Condition.
The New Directional Match Condition window opens.
-
In the Traffic reaching from drop-down box, select the object for Internal_clear (the source).
-
In the Traffic leaving to drop-down box, select the applicable VPN community object (the destination).
-
Add another directional match, in which the applicable VPN community object is both the source and destination.
This allows traffic from the local domain to the community, and within the community.
-
Click OK.
-
Install the Access Control Policy.
Configuring Directional VPN Between Communities
To configure Directional VPN between communities:
-
In SmartConsole, click > Global properties > VPN > Advanced.
-
Select Enable VPN Directional Match in VPN Column.
-
Click OK.
-
In SmartConsole, from the left navigation panel, click Security Policies.
-
In the Access Control section, click in the applicable rule.
-
In the VPN column of this rule, select Directional Match Condition.
The New Directional Match Condition window opens.
-
In the Traffic reaching from drop-down box, select the source of the connection.
-
In the Traffic leaving to drop-down box, select the destination of the connection
-
Click OK.
-
Install the Access Control Policy.
