Site-to-Site VPN
The basis of Site-to-Site VPN is the encrypted VPN tunnel. Two Security Gateways negotiate a link and create a VPN tunnel and each tunnel can contain more than one VPN connection. One Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. can maintain more than one VPN tunnel at the same time.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. can maintain more than one VPN tunnel at the same time.
Sample Site-to-Site VPN Deployment
|
Item |
Description |
|---|---|
|
A, B |
Security Gateways |
|
2 |
VPN tunnel |
|
3 |
Internal network in VPN domain |
|
4 |
Host 4 |
|
5 |
Host 5 |
In this sample VPN deployment, Host 4 and Host 5 securely send data to each other. The Security Gateways perform IKE negotiation and create a VPN tunnel. They use the IPsec protocol to encrypt and decrypt data that is sent between Host 4 and Host 5.
VPN Workflow
VPN Communities
A VPN Domain is a collection of internal networks that use Security Gateways to send and receive VPN traffic. Define the resources that are included in the VPN Domain for each Security Gateway. Then join the Security Gateways into a VPN community - collection of VPN tunnels and their attributes. Network resources of different VPN Domains can securely communicate with each other through VPN tunnels that terminate at the Security Gateways in the VPN communities.
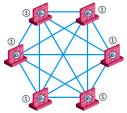
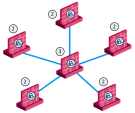
VPN communities are based on Star and Mesh topologies. In a Mesh community, there are VPN tunnels between each pair of Security Gateway. In a Star community, each satellite Security Gateway has a VPN tunnel to the central Security Gateway, but not to other Security Gateways in the community.
|
Mesh Topology |
|
Star Topology |
|
|
|
Item |
Description |
|---|---|
|
1 |
Security Gateway |
|
2 |
Satellite Security Gateways |
|
3 |
Central Security Gateway |
This section explains how to configure a VPN star community. This deployment lets the satellite Security Gateways connect to the internal network of the central Security Gateway. The internal network object is named: Internal-network.
To create a new VPN Star Community:
-
In SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., go to the Security Policies page.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., go to the Security Policies page. -
In the Access Tools section, click VPN Communities.
-
Click New and select Star Community.
The New Star Community window opens.
-
Enter the name for the community.
-
From the navigation tree, select Encryption.
-
Configure the VPN encryption methods and algorithms for the VPN community.
-
Click OK.
For each Security Gateway in the VPN community, follow these configuration steps.
-
In SmartConsole, go to the Gateways & Servers page and double-click the Security Gateway object.
The Security Gateway properties window opens.
-
In the Network Security section of the General Properties page, select IPsec VPN.
-
From the navigation tree, go to Network Management > VPN Domain.
-
For the central Security Gateway, click Manually defined and select the Internal-network object
-
For a satellite Security Gateway, select All IP addresses
-
-
From the navigation tree, click IPsec VPN.
-
Configure the Security Gateway as a member of a VPN star community.
-
In the This Security Gateway participates in the following VPN Communities section, click Add.
The Add this Gateway to Community window opens.
-
Select the VPN Community.
-
Click OK.
-
-
Click OK.
After you create a community and configure Security Gateways, add those Security Gateways to the community as a center or as a satellite Security Gateway.
-
In SmartConsole, go to the Security Policies page.
-
In the Access Tools section, click VPN Communities.
-
Select the new star community and click Edit.
The Star Community window opens.
-
In the Gateways page, add Security Gateways to the community:
-
Center Gateways - Click Add and select center Security Gateways. Select Mesh center gateways, if necessary.
-
Satellite Gateways - Click Add and select satellite Security Gateways.
-
-
Click OK.
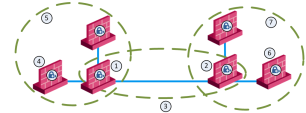
Sample Combination VPN Community
|
Item |
Description |
|---|---|
|
1 |
London Security Gateway |
|
2 |
New York Security Gateway |
|
3 |
London - New York Mesh community |
|
4 |
London company partner (external network) |
|
5 |
London Star community |
|
6 |
New York company partner (external network) |
|
7 |
New York Star community |
This deployment is composed of a Mesh community for London and New York Security Gateways that share internal networks. The Security Gateways for external networks of company partners do not have access to the London and New York internal networks. However, the Star VPN communities let the company partners access the internal networks of the sites that they work with.
Allowing VPN Connections
To allow VPN connections between Security Gateways in specific VPN communities, add Access Control rules that accept such connections.
To allow all VPN traffic to hosts and clients on the internal networks of a specific VPN community, select these options in the Encrypted Traffic section of the properties configuration window for that VPN Community:
-
For a meshed community: Accept all encrypted traffic
-
For a Star Community: Accept all encrypted traffic on Both center and satellite gateways, or Accept all encrypted traffic on Satellite gateways only.
Sample VPN Access Control Rules
This table shows sample VPN rules for an Access Control Rule Base![]() All rules configured in a given Security Policy. Synonym: Rulebase.. (The Action, Track and Time columns are not shown. Action is set to Allow, Track is set to Log, and Time is set to Any.)
All rules configured in a given Security Policy. Synonym: Rulebase.. (The Action, Track and Time columns are not shown. Action is set to Allow, Track is set to Log, and Time is set to Any.)
-
Automatic rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. that SmartConsole adds to the top of the Implied Rules when the Accept All Encrypted Traffic configuration option is selected for the
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. that SmartConsole adds to the top of the Implied Rules when the Accept All Encrypted Traffic configuration option is selected for the BranchOfficesVPN community and theLondonOfficesVPN community. This rule is installed on all the Security Gateways in these communities. It allows all VPN traffic to hosts and clients on the internal networks of these communities. Traffic that is sent to the Security Gateways in these VPN communities is dropped.Note - This automatic rule can apply to more than one VPN community.
-
Site-to-site VPN - Connections between hosts in the VPN Domains of all Site-to-Site VPN communities are allowed. These are the only protocols that are allowed: FTP, HTTP, HTTPS and SMTP.
-
Remote access - Connections between hosts in the VPN Domains of Remote Access VPN community are allowed. These are the only protocols that are allowed: HTTP, HTTPS, and IMAP.
To Learn More About Site-to-Site VPN
To learn more about site-to-Site VPN, see the R81.20 Site to Site VPN Administration Guide.