Creating an Administrator Account with SAML Authentication Login
With SAML authentication, administrators log in to SmartConsole![]() Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. through a central 3rd party Identity Provider with the SAML protocol. The Identity Provider holds the information about the administrators, including the ability to authenticate the administrators. Check Point supports these Identity Providers: Okta, Ping Identity, Azure.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. through a central 3rd party Identity Provider with the SAML protocol. The Identity Provider holds the information about the administrators, including the ability to authenticate the administrators. Check Point supports these Identity Providers: Okta, Ping Identity, Azure.
Use Case
Administrators with accounts in Azure want to work with SmartConsole. If each administrator uses two different administrator names and passwords, one for Azure and one for SmartConsole, this causes a number of issues:
-
The administrators must handle different password and expiration policies (in addition to other corporate passwords).
-
The administrators must remember two different passwords, one for Azure and one for SmartConsole (in addition to other corporate passwords).
-
It requires additional maintenance of the administrators. For example, when an administrator leaves, you must remove them from all applications they are registered to. If you use an Identity Provider, you simply need to remove the administrator from the Identity Provider database.
Therefore, the organization prefers that each administrator uses one password for both Azure and SmartConsole. With the Identity Provider, the administrator can authenticate once to Azure, and when the administrator connects to SmartConsole, SmartConsole already recognizes them and they do not have to enter another password. This way, the administrator also does not reveal their password to the Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server..
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server..
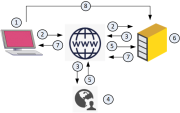
SAML Authentication Process Flow:
-
The administrator tries to log in to SmartConsole.
-
SmartConsole redirects the administrator back to the browser to a URL which is pre-configured on the Security Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server..
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server.. -
The Security Management Server redirects the browser with a SAML request to the Identity Provider.
-
The Identity Provider authenticates the administrator.
-
The Identity Provider generates a SAML assertion and sends it back to the Security Management Server through the browser.
-
The Security Management Server validates the SAML assertion.
-
If the administrator is authenticated, the Security Management Server redirects the browser to SmartConsole with the necessary data required for authentication.
-
SmartConsole opens a session to the Security Management Server with this authentication data.
SAML Authentication Login
|
|
Note - By default, SAML authentication for SmartConsole login requires Gaia Portal |
-
 In your Identity Provider, create the SmartConsole application and configure its settings
In your Identity Provider, create the SmartConsole application and configure its settings
See your Identity Provider documentation for instructions.

Notes:
-
Make sure the client can connect to the Identity Provider website and that there is no policy rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. that blocks it.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. that blocks it. -
The SmartConsole application integration in your Identity Provider must have attribute mappings for "username", and it must have the "sign assertion and response" option selected.
-
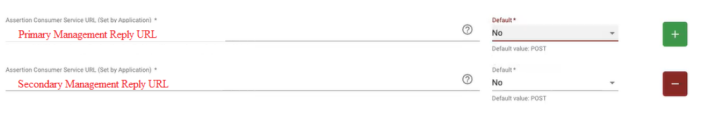
The Identity Provider can return response to more than one URL. In a Management High Availability
 Deployment and configuration mode of two Check Point Management Servers, in which they automatically synchronize the management databases with each other. In this mode, one Management Server is Active, and the other is Standby. Acronyms: Management HA, MGMT HA. environment, enter the required number of Reply URLs.
Deployment and configuration mode of two Check Point Management Servers, in which they automatically synchronize the management databases with each other. In this mode, one Management Server is Active, and the other is Standby. Acronyms: Management HA, MGMT HA. environment, enter the required number of Reply URLs.When the Identity Provider sends the response, the response must contain the IP address that the response is returned to.
If the required destination is not included in the response, the response is eliminated.
Make sure to disable the use of "Default" for the Reply URLs:
-
-
 In SmartConsole, create an Identity Provider object and configure it
In SmartConsole, create an Identity Provider object and configure it
-
In the Object Explorer, click New > More > User/Identity > Identity Provider.
The New Identity Provider window opens.
-
Configure these properties for the Identity Provider object:
-
Name (for example: Azure).
-
Use Identity Provider for - Select Managing administrator access. This handles the authentication to SmartConsole through an Identity Provider.
Note - To use the SAML authentication for Security Gateway and logs, see the R81.20 Identity Awareness Administration Guide.
-
Data Required by the SAML Identity Provider - SmartConsole creates the Identifier (Entity ID) and the Reply URLs according to the environment.
Take the Identifier (Entity ID) and Reply URL that SmartConsole showed you and enter them in the relevant places in the properties of the SmartConsole application you created in your Identity Provider.
 To use a Domain name instead of a URL
To use a Domain name instead of a URL

Note - For a Security Management Server and Multi-Domain Server
 Dedicated Check Point server that runs Check Point software to host virtual Security Management Servers called Domain Management Servers. Synonym: Multi-Domain Security Management Server. Acronym: MDS. behind NAT, these steps must be followed.
Dedicated Check Point server that runs Check Point software to host virtual Security Management Servers called Domain Management Servers. Synonym: Multi-Domain Security Management Server. Acronym: MDS. behind NAT, these steps must be followed.In a Management High Availability environment, you must do these steps on each Management Server.
-
Connect to the command line on the Management Server.
-
Log in to the Expert mode.
-
Edit the $CPDIR/tmp/.CPprofile.sh file:
vi $CPDIR/tmp/.CPprofile.sh -
Add this line at the bottom of the file:
SAML_IP_OR_NAME=<Your Domain Name>;export SAML_IP_OR_NAMEExample:
SAML_IP_OR_NAME=example.com;export SAML_IP_OR_NAME -
Save the changes in the file and exit the editor.
-
Restart Check Point services (this action disconnects SmartConsole clients):
-
On a Security Management Server, run:
cpstop ; cpstart -
On a Multi-Domain Server, run:
mdsstop ; mdsstart
-
-
Connect with SmartConsole to the Management Server.
-
Open the Identity Provider Website.
-
In the Reply URLs, replace the IP address with the Domain Name.
-
- Data received from the SAML Identity Provider:
Import metadata file - The Identity Provider creates this file. The metadata file has all the information required to establish trust between the Identity Provider and the Management Server.
If the Identity Provider has no metadata file, enter this information of the Identity Provider manually:
Identifier (Entity ID) - Unique identifier of the Identity Provider.
Login (URL) - This is the endpoint on the Identity Provider side where SAML requests are posted.
Certificate file - The Management Server takes the certificate file from the Identity Provider to validate the Identity Provider's signature. The certificate is stored on the Management Server and used whenever responses are posted.
-
-
Click OK.
-
Publish the SmartConsole session.
-
-
In SmartConsole, go to the Manage & Settings view > Permissions & Administrators > Advanced > Identity Provider > Identity Provider for Managing Administrator Access > Select the Identity Provider object that you created.

 Notes:
Notes:
-
On a Security Management Server, you can use only one Identity Provider
-
On a Multi-Domain Security Management Server:
-
You can use only one Identity Provider for a Domain.
-
If you configure an Identity Provider for the Multi-Domain Server and do not configure an Identity Provider for a Domain, the Domain Management Server takes the Identity Provider configured for the Multi-Domain Server.
-
Only super user can assign an Identity Provider to a Domain.
-
To access the Domain with the Domain's Identity Provider, open SmartConsole and connect to the Domain's IP address.
-
Domain's Identity Provider can only authenticate for administrators or groups that have a permission profile for the Domain.
-
-
-
 Create the administrator (or group of administrators) that authenticates with an Identity Provider
Create the administrator (or group of administrators) that authenticates with an Identity Provider
-
In SmartConsole, go to Manage & Settings > Permissions & Administrators > Administrators.
-
Click the icon
 and from the drop-down list select New Administrator or New Identity Provider Administrator Group.
and from the drop-down list select New Administrator or New Identity Provider Administrator Group. -
For an administrator, configure these settings:
-
Name - The administrator name must be identical to the name defined in the Identity Provider's username attribute.
-
Authentication Method - Select Identity Provider.
-
Permissions - Assign the required permission profile.
For an administrator group, configure these settings:
-
Name - Enter a name for the administrator group object. You can select any name.
-
Group ID/name - Must be identical to the group attribute defined in the Identity Provider.
-
Permission - Assign the required permission profile.

Notes:
-
The Expiration date is grayed out because it is defined in the Identity Provider's database.
-
In the Identity Provider's interface, configure a SAML attribute:
-
Define an optional attribute named "groups".
-
Configure the attribute according to the Identity Provider's requirements.
-
-
-
-
There are two ways to log in to SmartConsole with Identity Provider.
 Logging in through the SmartConsole login window
Logging in through the SmartConsole login window
-
Open SmartConsole.
-
From the first drop-down menu, select Identity Provider.
The Security Management Server checks if the administrator exists in the Security Management Server database.
-
If the administrator exists, the SmartConsole logs the administrator in.
-
If the administrator does not exist, the Security Management Server checks if the administrator is in an administrator group in the Security Management Server database.
If the administrator exists in such a group, SmartConsole logs in the administrator, and the Security Management Server assigns the administrator the permissions of the group.
-
-
Enter the IP address or hostname of the Management Server.
-
Click Login with SSO.

Notes:
-
If an administrator has an administrator account and is also part of an administrator group, the Security Management Server assigns to the administrator the administrator account permissions.
-
If the administrator belongs to more than one administrator group, the Security Management Server assigns to the administrator the permissions of the administrator group which comes first in alphabetical order in the Security Management Server database.
-
The administrator session is not disconnected if you disconnect or edit the administrator object in the Identity Provider while the Security Management Server session is active.

Best Practice - We recommend to use at least one administrator that is not authenticated through the Identity Provider, in case the Identity Provider is not available.
 Logging in with a SmartConsole configuration file
Logging in with a SmartConsole configuration file
CLI Syntax:
To launch SmartConsole with a configuration file for SAML login, use this command in the Windows Command Prompt:
SmartConsole.exe -p "Full Path to the Configuration File"Example:
cd /d "C:\Program Files (x86)\CheckPoint\SmartConsole\R81.20\"SmartConsole.exe -p "D:\MySAML_Configuration.xml"Required Configuration File:
This is the required configuration file (plain-text XML):
Copy<?xml version="1.0" encoding="utf-8"?>
<RemoteLaunchParemeters xmlns:xsi="http:/www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http:/www.w3.org/2001/XMLSchema">
<ServerIP>IP Address of the Management Server</ServerIP>
<DomainName>Name of the Domain Management Server</DomainName>
<ReadOnly>False</ReadOnly>
<CloudDemoMode>False</CloudDemoMode>
<IsSamlLogin>1</IsSamlLogin>
</RemoteLaunchParemeters>Parameters:
Parameter
Description
<ServerIP>Specifies the IP Address of the Management Server.
<DomainName>Specifies the name of the Domain Management Server object when connecting to a Multi-Domain Security Management Server.
<ReadOnly>Specifies if to open SmartConsole in the Read-Only mode.
Valid values:
-
False- Opens SmartConsole in the Write mode. -
True- Opens SmartConsole in the Read-Only mode.
<CloudDemoMode>Specifies if to enable the Demo Mode.
Valid values:
-
False- Opens SmartConsole in regular mode. -
True- Opens SmartConsole in the Demo mode.
<IsSamlLogin>Specifies if to enable the SAML login.
Valid values:
-
1- Enables the SAML login. -
0- Disables the SAML login.
Example of the configuration file for a Security Management Server with the IP address 172.30.44.55:
Copy<?xml version="1.0" encoding="utf-8"?>
<RemoteLaunchParemeters xmlns:xsi="http:/www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http:/www.w3.org/2001/XMLSchema">
<ServerIP>172.30.44.55</ServerIP>
<ReadOnly>False</ReadOnly>
<CloudDemoMode>False</CloudDemoMode>
<IsSamlLogin>1</IsSamlLogin>
</RemoteLaunchParemeters> -
After you configure SAML authentication, you can, in addition, configure authentication with a certificate file. The administrator can then authenticate to SmartConsole with the SAML Identity Provider or the certificate file.
You create the certificate file in SmartConsole. The administrator can use the certificate to log in to SmartConsole in two ways:
-
Log in to SmartConsole with the Certificate File option. The administrator must provide the password to use the certificate file.
-
You can import the certificate file to the Windows Certificate Store on the Microsoft Windows SmartConsole computer. The administrator can use this stored certificate to log in to SmartConsole with the CAPI Certificate option. The administrator does not need to provide a password to log in.
The administrator can also give the certificate to other administrators to log in to SmartConsole with no administrator account of their own.