Deploying a Security Group in Bridge Mode
Introduction to Bridge Mode
If it is not possible divide the existing network into several networks with different IP addresses, you can configure a Security Group![]() A logical group of Security Appliances that provides Active/Active cluster functionality. A Security Group can contain one or more Security Appliances. Security Groups work separately and independently from each other. To the production networks, a Security Group appears a single Security Gateway. Every Security Group contains: (A) Applicable Uplink ports, to which your production networks are connected; (B) Security Appliances (the Quantum Maestro Orchestrator determines the applicable Downlink ports automatically); (C) Applicable management port, to which the Check Point Management Server is connected. in the Bridge Mode.
A logical group of Security Appliances that provides Active/Active cluster functionality. A Security Group can contain one or more Security Appliances. Security Groups work separately and independently from each other. To the production networks, a Security Group appears a single Security Gateway. Every Security Group contains: (A) Applicable Uplink ports, to which your production networks are connected; (B) Security Appliances (the Quantum Maestro Orchestrator determines the applicable Downlink ports automatically); (C) Applicable management port, to which the Check Point Management Server is connected. in the Bridge Mode.
A Security Group in Bridge Mode is invisible to Layer 3 traffic.
When traffic arrives at one of the bridge slave interfaces, the Security Group inspects it and passes it to the second bridge slave interface.
Example Topology for Bridge Mode
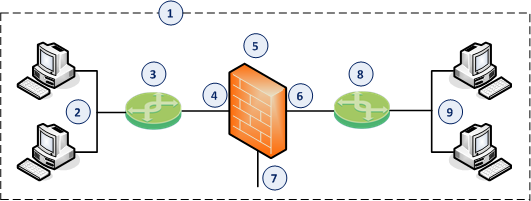
|
Item |
Description |
|---|---|
|
1 |
Network, which an administrator needs to divide into two Layer 2 segments. The Security Group in Bridge Mode connects between these segments. |
|
2 |
First network segment. |
|
3 |
Switch that connects the first network segment to one bridged slave interface (4) on the Security Group in Bridge Mode. |
|
4 |
One bridged slave interface (for example, |
|
5 |
Security Group in Bridge Mode. |
|
6 |
Another bridged slave interface (for example, |
|
7 |
Dedicated Gaia Management Interface (for example, |
|
8 |
Switch that connects the second network segment to the other bridged slave interface (6) on the Security Group in Bridge Mode. |
|
9 |
Second network segment. |
Supported Software Blades in Bridge Mode
This table lists Software Blades, features, and their support for the Bridge Mode.
|
|
Notes:
|
Limitations in Bridge Mode
You can configure only two slave interfaces in one Bridge interface. You can think of this Bridge interface as a two-port Layer 2 switch. Each port can be a Physical interface, a VLAN interface, or a Bond interface.
These features and deployments are not supported in Bridge Mode:
-
NAT rules (specifically, Firewall kernel in logs shows the traffic as accepted, but Security Gateway does not actually forward it). For more information, see sk106146.
-
Access to Multi-Portal (Mobile Access Portal, Identity Awareness Captive Portal, Data Loss Prevention Portal, and so on) from bridged networks, if the bridge does not have an assigned IP address.
For more information, see sk101371: Bridge Mode on Gaia OS and SecurePlatform OS.

