SAML Identity Provider for Identity Awareness
This section describes how to configure authentication using a 3rd party Identity Provider over the SAML protocol as an authentication method for an Identity Awareness![]() Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. Gateway (Captive Portal
Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. Gateway (Captive Portal![]() A Check Point Identity Awareness web portal, to which users connect with their web browser to log in and authenticate, when using Browser-Based Authentication.) as a Service Provider.
A Check Point Identity Awareness web portal, to which users connect with their web browser to log in and authenticate, when using Browser-Based Authentication.) as a Service Provider.
An Identity Provider is a system entity that creates, maintains, and manages identity information and provides authentication services. A Service Provider is a system entity that provides services for users authenticated by the Identity Provider.
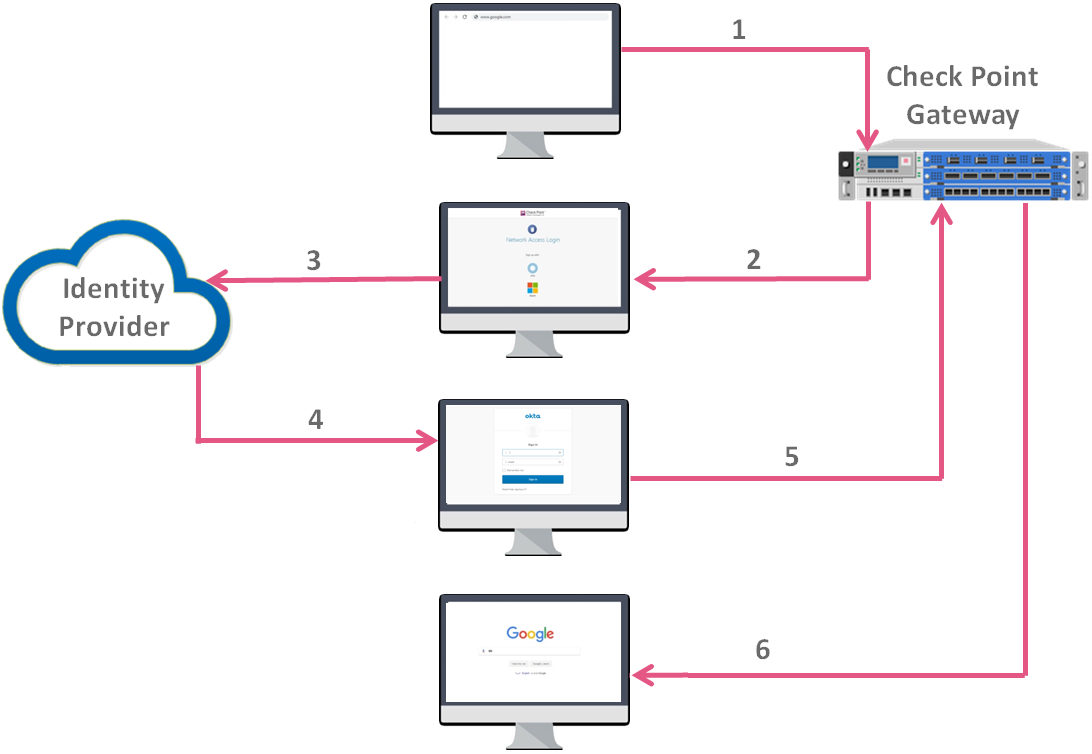
SAML Authentication Process Flow
In the example diagram below:
-
The service is
google.com. -
The service provider is Identity Awareness Gateway (Captive Portal).
-
The Identity Provider is Okta.
|
|
|
Important - When you sign out from the Check Point service portal, it does not automatically sign out from the Identity Provider's session. |
Basic SAML Configuration for Identity Awareness
-
 Configure the Identity Awareness Software Blade
Configure the Identity Awareness Software Blade
-
Enable the Identity Awareness Software Blade
 Specific security solution (module): (1) On a Security Gateway, each Software Blade inspects specific characteristics of the traffic (2) On a Management Server, each Software Blade enables different management capabilities. (see Getting Started with Identity Awareness).
Specific security solution (module): (1) On a Security Gateway, each Software Blade inspects specific characteristics of the traffic (2) On a Management Server, each Software Blade enables different management capabilities. (see Getting Started with Identity Awareness). -
Configure the Identity Awareness Captive Portal (see Configuring Browser-Based Authentication).
-
-
 Configure an External User Profile object
Configure an External User Profile object
External User Profile represents all the users authenticated by the Identity Provider.
-
In SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., click Manage & Settings > Blades.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., click Manage & Settings > Blades. -
In the Mobile Access section, click Configure in SmartDashboard.
-
In the bottom left pane, click Users.
-
In the bottom left pane, right click on an empty space below the last folder in the pane and select New > External User Profile > Match all users.
-
Configure the External User Profile properties:
-
On the General Properties page:
In the External User Profile name field, leave the default name generic*.
In the Expiration Date field, set the applicable date.
-
On the Authentication page:
From the Authentication Scheme drop-down list, select and configure the applicable option.
-
On the Location, Time, and Encryption pages, configure other applicable settings.
-
Click OK.
-
-
From the top toolbar, click Update (or press Ctrl + S).
-
Close SmartDashboard.
-
In SmartConsole, install the Access Control Policy.
Note - It is not mandatory to install policy at the end of this step.
-
-
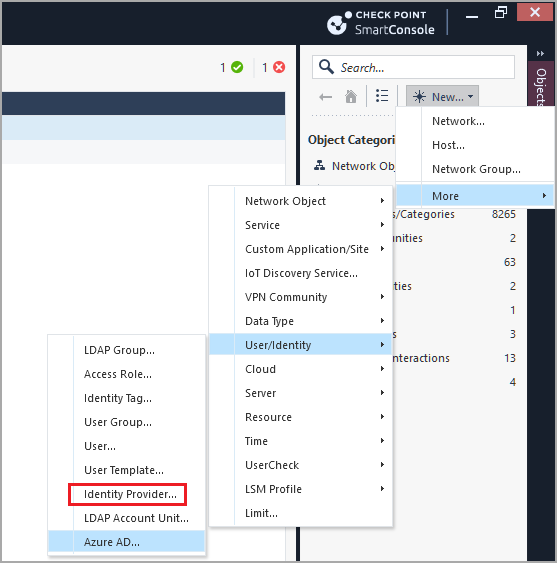
 Configure an Identity Provider object
Configure an Identity Provider object
-
In SmartConsole, from the Gateways & Servers view click New > More > User/Identity > Identity Provider.
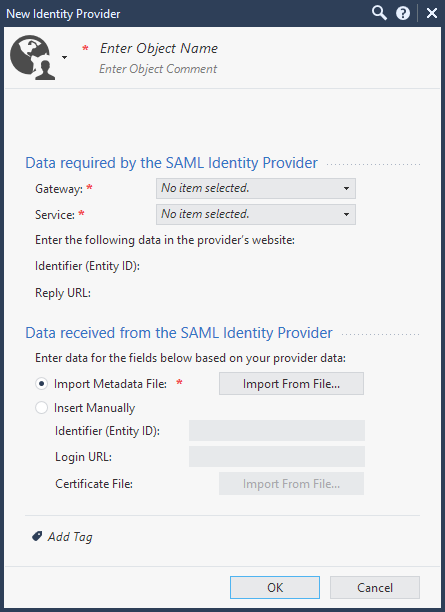
A New Identity Provider window opens:
-
In the New Identity Provider window, in the Data required by the SAML Identity Provider section, configure these settings:
-
In the Gateway field, select the Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., which needs to perform the SAML authentication.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., which needs to perform the SAML authentication. -
In the Service field, select Identity Awareness.
SmartConsole automatically generates the data in these fields based on the previous two fields:
-
Identifier (Entity ID) – This is a URL that uniquely identifies a service provider (the Security Gateway, in our case)
-
Reply URL – This is a URL, to which the SAML assertions are sent
-
-
Configure SAML Application on an Identity Provider website.

Important:
-
Do not close the New Identity Provider window while you configure the SAML application in your Identity Provider’s website. You continue the configuration later with the information you receive from the Identity Provider.
-
Follow the Identity Provider's instructions.
-
You must provide the values from the New Identity Provider window from the Identifier (Entity ID) and the Reply URL fields.
Copy these values from SmartConsole and paste them in the corresponding fields on the Identity Provider's website.

Note - The exact names of the target fields on the Identity Provider's website might differ between Identity Providers.
-
Make sure to configure the Identity Provider to send the authenticated username in the email format (
alias@domain). -
Optional: If you wish to receive the Identity Provider's groups, in which the user is defined, make sure to configure the Identity Provider to send the group names as values of the attribute called group_attr.
-
Make sure that at the end of the configuration process you get this information from the Identity Provider:
-
Entity ID - a URL that uniquely identifies the application
-
Login URL - a URL to access the application
-
Certificate – for validation of the data exchanged between the Security Gateway and the Identity Provider

Note - Some Identity Providers supply a metadata XML file, which contains this information.
-
-
-
In the New Identity Provider window, in the Data received from the SAML Identity Provider section, configure one of these settings:
-
Select Import the Metadata File to upload the metadata file supplied by the Identity Provider.
-
Select Insert Manually to paste manually the Entity ID and Login URL into the corresponding fields, and to upload the Certificate File. All these are supplied by the Identity Provider.
-

Note - Identity Provider object in SmartConsole does not support the import of RAW Certificate.

Important - If later you change the settings of the Browser-Based Authentication
 Authentication of users in Check Point Identity Awareness web portal - Captive Portal, to which users connect with their web browser to log in and authenticate. in the Identity Awareness Gateway object, then you must update the applicable settings in the SAML application on the Identity Provider's website.
Authentication of users in Check Point Identity Awareness web portal - Captive Portal, to which users connect with their web browser to log in and authenticate. in the Identity Awareness Gateway object, then you must update the applicable settings in the SAML application on the Identity Provider's website. -
-
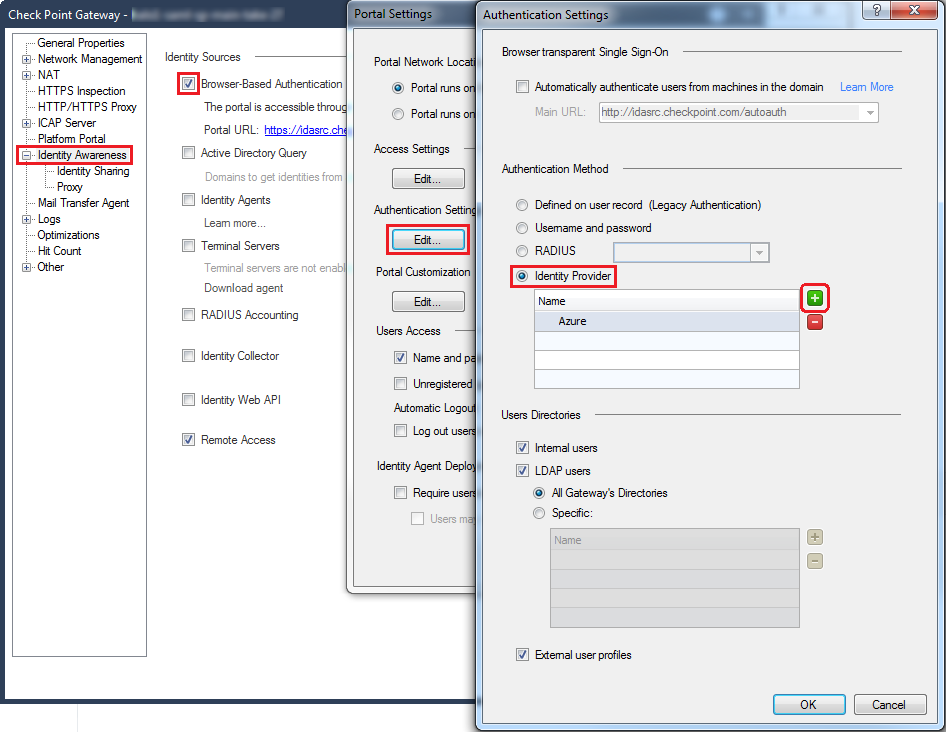
 Configure the Identity Provider as an authentication method
Configure the Identity Provider as an authentication method
To use the SAML Identity Provider object as an authentication method, you must configure the authentication settings for the Identity Awareness:
-
In SmartConsole, click the Gateways & Servers panel.
-
Open the Security Gateway object.
-
From the left tree, click Identity Awareness.
-
Near the Browser-Based Authentication, click Settings.
-
In the Authentication Settings section, click Edit.
-
In the Authentication Method section, select Identity Provider.
-
Click the green [+] button and select the SAML Identity Provider object.
Example:
-
Click OK.

Notes:
-
If you configure only one Identity Provider object, the end user is redirected to that Identity Provider's portal.
-
If you configure more than one Identity Provider object, the end user is asked to choose the Identity Provider for authentication.
-
-
 Optional: Configure group authorization
Optional: Configure group authorization
 Part A - Configuring
Part A - Configuring
For each group configured in your SAML application, you must create an equivalent Identity Tag object in SmartConsole.
The value of the Identity Tag must be identical to the value of the provided group or to the Object ID.

Note - If you use Azure AD, you must create the Identity Tag in SmartConsole by the Azure AD Group Object ID and not by the User Group name:
-
Open your Azure AD.
-
Go to the User Group you created in Azure.
-
Copy the Object ID and paste it in the Identity Tag > External Identifier field in SmartConsole.
For more information, see Using Identity Tags in Access Role Matching.
 Part B - Configuring group authorization behavior
Part B - Configuring group authorization behavior

Important - In a Cluster
 Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing., you must configure all the Cluster Members in the same way.
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing., you must configure all the Cluster Members in the same way.A Security Gateway can authorize groups in different ways.
Authorization can refer to two types of groups:
-
Identity Provider groups - these are groups the Identity Provider sends
-
Internal groups - these are groups received from User Directories configured in SmartConsole
Available options to configure the authorization behavior:

Note - This configuration is for each Realm.
To receive group information from Microsoft Entra ID, you must set the value of the parameter
userLoginAttron the Management Server Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. to
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. to mail. This is because Microsoft Entra ID sends a username in the form of an email address. If you want the PDP Check Point Identity Awareness Security Gateway that acts as Policy Decision Point: acquires identities from identity sources; shares identities with other gateways. Gateway to return user groups, the relevant users' Microsoft Entra ID usernames must be in the form of an email address.
Check Point Identity Awareness Security Gateway that acts as Policy Decision Point: acquires identities from identity sources; shares identities with other gateways. Gateway to return user groups, the relevant users' Microsoft Entra ID usernames must be in the form of an email address.To enable a Policy Decision Point (PDP) Identity Awareness Gateway to receive group information from Microsoft Entra ID:
-
Back up the Security Management Server
 Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. / applicable Domain Management Server.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. / applicable Domain Management Server.Refer to:
-
Close all SmartConsole windows.
Note - To make sure there are no active sessions, run the "
cpstat mg" command in the Expert mode on the Security Management Server / in the context of eachDomain Management Server. -
Connect with Database Tool (GuiDBEdit Tool) to the Security Management Server / applicable Domain Management Server.
-
In the top left pane, go to Table > Network Objects > network_objects.
-
In the top right pane, select the object for the relevant Security Gateway. The Class Name of this object is gateway_ckp.
-
Press the CTRL+F keys (or go to the Search menu > click Find) > paste UserLoginAttr > click Find Next.
-
In the lower pane, right-click on the UserLoginAttr > select Edit > select "mail" > click OK.
-
Save the changes: go to the File menu > click Save All.
-
Close the Database Tool (GuiDBEdit Tool).
-
Connect with SmartConsole to the Security Management Server / applicable Domain Management Server.
-
Install the Access Control Policy on the applicable Security Gateway / Cluster / VSX
 Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts.Virtual System object.
Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts.Virtual System object.
You can view and change the authorization behavior on the Security Gateway.
 Viewing the configured authorization behavior
Viewing the configured authorization behavior
You see the configured behavior in one of these ways:
-
On the Identity Awareness Gateway / each Cluster Member
 Security Gateway that is part of a cluster., examine the applicable value in Check Point Registry in the Expert mode:
Security Gateway that is part of a cluster., examine the applicable value in Check Point Registry in the Expert mode:ckp_regedit -p SOFTWARE/Checkpoint/Ex_Groups "<Realm Name>" -
On the Identity Awareness Gateway / each Cluster Member (in the Expert mode or Gaia Clish
 The name of the default command line shell in Check Point Gaia operating system. This is a restricted shell (role-based administration controls the number of commands available in the shell).):
The name of the default command line shell in Check Point Gaia operating system. This is a restricted shell (role-based administration controls the number of commands available in the shell).):pdp idp groups status
 Configuring the authorization behavior
Configuring the authorization behavior
You can set the behavior in one of these ways:
-
On the Identity Awareness Gateway / each Cluster Member, change the applicable value in Check Point Registry in the Expert mode:
ckp_regedit -a SOFTWARE/Checkpoint/Ex_Groups "<Realm Name>" -n {0 | 1 | 2 | 3} -
On the Identity Awareness Gateway / each Cluster Member (in the Expert mode or Gaia
 Check Point security operating system that combines the strengths of both SecurePlatform and IPSO operating systems. Clish):
Check Point security operating system that combines the strengths of both SecurePlatform and IPSO operating systems. Clish):pdp idp groups set {only | prefer | union | ignore}

Notes:
-
Make sure SAML directory and the applicable User Directory
 Check Point Software Blade on a Management Server that integrates LDAP and other external user management servers with Check Point products and security solutions. can synchronize with each other.
Check Point Software Blade on a Management Server that integrates LDAP and other external user management servers with Check Point products and security solutions. can synchronize with each other. -
Make sure that the LDAP lookup type of the applicable realm is set to "
mail".
 Part C - Configuring an internal User Group "EXT_ID_<name>"
Part C - Configuring an internal User Group "EXT_ID_<name>"
-
In SmartConsole top right corner, click the Objects panel.
-
Click New > More > User/Identity > User Group.
-
In the name field, enter:
EXT_ID_<Name_of_User_Group_in_Azure>
Example name:
EXT_ID_AzureAD_Users -
Optional: In the Comment field, enter the applicable text.
-
Do not add any users in this group object (leave it empty).
-
Click OK.
-
-
 Install the Access Control Policy
Install the Access Control Policy
-
In SmartConsole, click Install Policy.
-
Select the applicable policy.
-
Select Access Control.
-
Click Install.
-
|
|
Important - Before you use SAML configuration, make sure that your Security Policy |
Advanced SAML Configuration for Identity Awareness
Starting from R81.20 Jumbo Hotfix Accumulator Take 89, you can configure these advanced SAML features:
-
Request Signing: Verifies authenticity of SAML requests.
-
Assertion Decryption: Protects confidentiality of user attributes.
-
Forced Re-authentication: Enables mandatory login for each session.
For configuration instructions, refer to sk182042.