Configuring VSX Clusters
|
|
Important - This chapter does not apply to Scalable Platforms (Maestro and Chassis). |
This chapter presents a conceptual overview of VSX![]() Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts. Cluster
Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts. Cluster![]() Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. deployments, with emphasis on clustering features and their application.
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. deployments, with emphasis on clustering features and their application.
It assumes you are familiar with network cluster applications and environments, particularly ClusterXL.
For more about Check Point ClusterXL features and functionality, see the R81.10 ClusterXL Administration Guide
VSX Cluster Overview
VSX Clusters provide redundancy and load sharing features for Virtual Systems and other Virtual Devices.
A VSX Cluster consists of two or more identical, interconnected VSX Gateways that ensure continuous data synchronization.
The advantages of using clusters in a VSX environment include:
-
Transparent failover in case of VSX Cluster Member
 Security Gateway that is part of a cluster. or Virtual System
Security Gateway that is part of a cluster. or Virtual System Virtual Device on a VSX Gateway or VSX Cluster Member that implements the functionality of a Security Gateway. Acronym: VS. failure
Virtual Device on a VSX Gateway or VSX Cluster Member that implements the functionality of a Security Gateway. Acronym: VS. failure -
State synchronization ensures zero downtime for mission-critical environments
-
Load Sharing maintains system throughput during peak demand
-
Enhanced scalability for future traffic growth
VSX Cluster Modes:
|
Mode |
Description |
||
|---|---|---|---|
|
Ensures continuous operation by means of transparent VSX Cluster Member failover. Enhances system performance by distributing Active Virtual Systems amongst VSX Cluster Members. Efficiently balances network traffic load by distributing active Virtual Systems between VSX Cluster Members. All VSX Cluster Members and Virtual Systems are continuously synchronized.
|
|||
|
High Availability |
Ensures continuous operation by means of transparent VSX Cluster Member failover. All VSX Cluster Members and Virtual Systems function in an the Active/Standby mode and are continuously synchronized.
|
Physical Clusters
VSX Cluster is based on Check Point ClusterXL concepts. This section reviews these concepts, and then demonstrates how these principles apply to VSX virtualization.
In typical Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. deployment, a cluster consists of two or more identical, interconnected physical Security Gateways that provide redundancy and/or Load Sharing. This cluster behaves as a single Security Gateway and is assigned its own IP address, which is known as its Cluster IP or Virtual IP address. This IP address is distinct from the physical IP addresses of its VSX Cluster Members, which are hidden from the networks connected to the cluster.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. deployment, a cluster consists of two or more identical, interconnected physical Security Gateways that provide redundancy and/or Load Sharing. This cluster behaves as a single Security Gateway and is assigned its own IP address, which is known as its Cluster IP or Virtual IP address. This IP address is distinct from the physical IP addresses of its VSX Cluster Members, which are hidden from the networks connected to the cluster.
Traffic from external networks or the Internet directed to the internal networks arrives at the external cluster IP address. Depending on the clustering mode (High Availability or Load Sharing), a designated VSX Cluster Member receives the traffic and performs the required inspection. After inspection, traffic is either sent to its destination on the internal network, or dropped.
Internal networks send traffic destined for the Internet or external networks, to the cluster IP address. This traffic is processed by the designated VSX Cluster Member, inspected, and forwarded to its external destination.
Each member interface has a unique, physical IP addresses. These IP addresses, which are invisible to physical networks, are used for internal communication between VSX Cluster Members and the Management Server![]() Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. for such tasks as downloading Security Policies
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. for such tasks as downloading Security Policies![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection., sending logs and checking the status of individual VSX Cluster Members.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection., sending logs and checking the status of individual VSX Cluster Members.
VSX Clusters
VSX Clusters, like their physical counterparts, connect two or more synchronized Gateways in such a way that if one fails, another immediately takes its place.
VSX Clusters are defined at two levels:
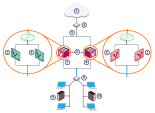
VSX ensures that Virtual Systems, Virtual Routers, Virtual Switches and their interfaces are provisioned and configured identically on each VSX Cluster Member.
The figure below shows that each VSX Cluster Member contains identical instances of each Virtual Device![]() Logical object that emulates the functionality of a type of physical network object. Virtual Device can be on of these: Virtual Router, Virtual System, or Virtual Switch..
Logical object that emulates the functionality of a type of physical network object. Virtual Device can be on of these: Virtual Router, Virtual System, or Virtual Switch..
These identical instances are referred to as peers.
VSX provides the management functionality to support network and security virtualization, including:
-
Assigning virtual IP addresses: Each Virtual Device interface requires its own virtual IP address.
-
State synchronization: Virtual Device state tables are synchronized to peers on other VSX Cluster Members.