The Threat Emulation Solution
ThreatCloud Emulation
You can securely send files to the Check Point ThreatCloud![]() The cyber intelligence center of all of Check Point products. Dynamically updated based on an innovative global network of threat sensors and invites organizations to share threat data and collaborate in the fight against modern malware. for emulation. The ThreatCloud is always up-to-date with the latest Threat Emulation
The cyber intelligence center of all of Check Point products. Dynamically updated based on an innovative global network of threat sensors and invites organizations to share threat data and collaborate in the fight against modern malware. for emulation. The ThreatCloud is always up-to-date with the latest Threat Emulation![]() Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. releases.
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. releases.
The new Threat Emulation engine uses Internet-connected sandboxes to prevent multi-stage attacks at the earliest stage. The full infection chain is analyzed and is presented in the MITRE ATT&CK Matrix visualization in the Threat Emulation report. The Internet-connected sandbox capability is supported on Threat Emulation AWS cloud platform and all Threat Emulation vectors: Web download, Mail Transfer Agent![]() Feature on a Security Gateway that intercepts SMTP traffic and forwards it to the applicable inspection component. Acronym: MTA., CloudGuard SaaS, SandBlast Agent and APIs.
Feature on a Security Gateway that intercepts SMTP traffic and forwards it to the applicable inspection component. Acronym: MTA., CloudGuard SaaS, SandBlast Agent and APIs.
-
The Security Gateway
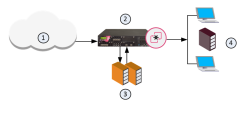
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. gets a file from the Internet or an external network.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. gets a file from the Internet or an external network. -
The Security Gateway compares the cryptographic hash of the file with the database.
-
If the file is already in the database, no additional emulation is necessary
-
If the file is not in the database, it is necessary to run full emulation on the file
-
-
The file is sent over a TLS connection to the ThreatCloud.
-
The virtual computers in the ThreatCloud run emulation on the file.
-
The emulation results are sent securely to the Security Gateway for the applicable action.
|
Item |
Description |
|---|---|
|
1 |
Internet and external networks |
|
2 |
Perimeter Security Gateway |
|
3 |
Check Point ThreatCloud servers |
|
4 |
Computers and servers in the internal network |
Watch the Video
For information about Private ThreatCloud, see the following Secure Knowledge articles:
-
sk149692: Private ThreatCloud
-
sk113332: Private ThreatCloud - Engine Updates
-
sk161534: How to configure Private ThreatCloud (PTC) on Scalable Platform Appliances
Threat Emulation Analysis Locations
You can choose a location for the emulation analysis that best meets the requirements of your company.
-
ThreatCloud - You can send all files to the Check Point ThreatCloud for emulation. Network bandwidth is used to send the files and there is a minimal performance impact on the Security Gateway.
- Threat Emulation Appliance in the Internal network - You can use a Threat Emulation appliance to run emulation on the files, whether locally or on a remote appliance.
Local or Remote Emulation
You can install a Threat Emulation appliance in the internal network.
-
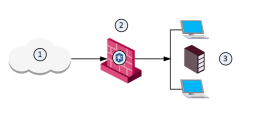
The Security Gateway receives the traffic, and aggregates the files.
-
The Security Gateway compares the cryptographic hash of the file with the database.
- The file is already in the database, no emulation is needed.
- If the file is not in the database, the virtual computers in the Security Gateway run full emulation on the file.
|
Item |
Description |
|---|---|
|
1 |
Internet and external networks |
|
2 |
Security Gateway/Threat Emulation appliance |
|
3 |
Computers and servers in the internal network |
-
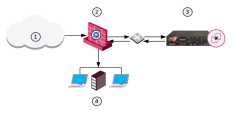
The Security Gateway aggregates the files, and the files are sent to the Threat Emulation appliance.
-
The Threat Emulation appliance compares the cryptographic hash of the file with the database. Files have unique cryptographic hashes. These file hashes are stored in a database after emulation is complete
-
If the file is already in the database, no emulation is needed.
-
If the file is not in the database, the virtual computers in the Threat Emulation appliance run full emulation on the file.
-
|
Item |
Description |
|---|---|
|
1 |
Internet and external networks |
|
2 |
Perimeter Security Gateway |
|
3 |
Threat Emulation Appliance |
|
4 |
Computers and servers in the internal network |
Selecting the Threat Emulation Deployment
|
Option |
Description |
|---|---|
|
Inline |
Traffic is sent for emulation before it is allowed to enter the internal network. You can use the Threat Prevention policy to block malware. |
|
Monitor (SPAN/TAP) |
You can use a mirror or TAP port to duplicate network traffic. Files are sent to the computer in the internal network. If Threat Emulation discovers that a file contains malware, the appropriate log action is done. |
|
MTA (see Configuring the Security Gateway as a Mail Transfer Agent) |
SMTP traffic goes to the Security Gateway, and is sent for emulation. The MTA acts as a mail proxy, and manages the SMTP connection with the source. The MTA sends email files to emulation after it closes the SMTP connection. When the file emulation is completed, the emails are sent to the mail server in the internal network. |
To switch between the Inline and Monitor modes, see the R81.10 Gaia Administration Guide
I want to use the Prevent![]() UserCheck rule action that blocks traffic and files and can show a UserCheck message. action and be able to block malicious files, what are my deployment options? See Threat Emulation Deployments with a Mail Transfer Agent
UserCheck rule action that blocks traffic and files and can show a UserCheck message. action and be able to block malicious files, what are my deployment options? See Threat Emulation Deployments with a Mail Transfer Agent
|
Option |
Description |
|---|---|
|
ThreatCloud |
Files are sent to the ThreatCloud for emulation. When the emulation is complete, ThreatCloud sends a notification to the Security Gateway that the files are safe. Then they go to computers in the internal network. |
|
Threat Emulation |
Threat Emulation Appliance with inline deployment - The files are kept in the Threat Emulation appliance and after emulation, safe files go to the computer in the internal network. |
This table summarizes how Threat Emulation sends traffic for emulation:
|
Traffic |
Block Malware |
|---|---|
|
Inline |
Yes |
|
Monitor (SPAN/TAP) |
No |
|
MTA |
Recommended with Prevent action for emails |
Inline Deployments
The ThreatCloud or Threat Emulation appliance gets a file from the Security Gateway. After emulation is done on the file, if the file is safe, it is sent to the computer in the internal network. If the file contains malware, it is quarantined and logged. The computer in the internal network is not changed.
Monitor (SPAN/TAP) Deployments
The Security Gateway gets a file from the Internet or an external network and lets it enter the internal network. The Threat Emulation appliance receives a copy of the file and the original file goes to the computer in the internal network. The Threat Emulation appliance compares the cryptographic the file with the database. If the file is already in the database, then no additional emulation is necessary. If the file is not in the database, the virtual computers in the Threat Emulation appliance do emulation of the file.
If the file is identified as malware, it is logged according to the Track action of the Threat Prevention rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session.. Monitor deployments support only the Detect action.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session.. Monitor deployments support only the Detect action.
Threat Emulation Deployments with a Mail Transfer Agent
SMTP traffic goes to the Security Gateway, and is sent for emulation. The MTA acts as a mail proxy, and manages the SMTP connection with the source. The MTA sends email files to emulation after it closes the SMTP connection. When the file emulation is completed, the emails are sent to the mail server in the internal network.
For more information on how to work with the Mail Transfer Agent, see Configuring the Security Gateway as a Mail Transfer Agent.
Threat Emulation Handling Mode
Emulation Connection Handling Mode lets you configure Threat Emulation to allow or block a connection while it finishes the analysis of a file. The handling mode you select affects the form of the file that the user receives and the timing at which the user receives it. This section explains the difference between the Threat Emulation handling modes and the interaction between the Threat Emulation and Threat Extraction![]() Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX. components with regards to the handling mode selected.
Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX. components with regards to the handling mode selected.
The first part of the section explains what happens when Threat Emulation works with Threat Extraction disabled and the second part explains how the Threat Emulation and the Threat Extraction components work together. You can also specify a different mode for SMTP and HTTP services. To configure the settings for the Threat Emulation handling mode, go to Security Policies > Threat Prevention > Policy > right-click a profile > Threat Emulation > Advanced.
Selecting an Emulation connection handling mode when Threat Extraction is disabled
If Threat Emulation reaches a verdict regarding a file within 3 seconds or less:
-
If the file is benign, the gateway sends the original file to the user.
-
If the file is malicious, the gateway blocks the page.
If Threat Emulation takes longer than 3 seconds to check the file:
-
In Rapid Delivery mode - The gateway sends the original file to the user (even if it turns out eventually that the file is malicious).
-
In Maximum Prevention mode - The user waits for Threat Emulation to complete. If the file is benign, the gateway sends the original file to the user. If the file is malicious, the gateway presents a Block page and the user does not get access to the file. Maximum Prevention mode gives you more security, but may cause time delays in downloading files.
In Custom mode- You can set a different handling mode for SMTP and HTTP. For example: you can set HTTP to Rapid Delivery and SMTP to Maximum Prevention.
Selecting an Emulation connection handling mode when Threat Extraction is enabled
With Threat Extraction, the gateway removes potentially malicious parts from downloaded/attached files and delivers them instantly to the user. Threat Emulation continues to run in the background, and examine the original files. Threat Extraction supports certain file types, primarily Microsoft Office files and PDFs, but not all file types, for example, executables.
-
If Threat Emulation rules that the file is benign, the user gets access to the original file, using the link in the file itself or the email body banner, , without help desk overhead.
-
If Threat Emulation rules that the file is malicious, the original file is blocked and the user only gets access to the cleaned file.
This way administrators can ensure maximum security, while not harming end-user productivity.
This behavior would be the same for both the Rapid Delivery and Maximum Prevention modes. Nevertheless, if you select Maximum Prevention, In CLI, you can configure an even more restrictive mode, such that:
-
The user always waits for Threat Emulation to complete, even if the file is supported by Threat Extraction.
-
The user receives the file only if the file is deemed benign, and if the file is supported by Threat Extraction, it will also be cleaned. To configure this mode, see sk146593.
When Threat Extraction is enabled, but the file is not supported by Threat Extraction, the user is not able to receive a cleaned version of the file. The behavior therefore, will be the same as when Threat Extraction is disabled. In Rapid Delivery mode, the user gets the original file and in Maximum Prevention mode, the user waits for the Threat Emulation verdict.
|
|
Best Practice: If Threat Extraction is enabled, use Maximum Prevention as your handling mode (without the extra preventive CLI configuration). Because most files that users work with on a daily basis are documents, that are supported by Threat Extraction, the time penalty for waiting for the non-supported files is manageable. Users will be able to receive most files in a timely manner. If Threat Extraction is disabled, select the handling mode based on balancing your security needs versus time constraints. |
If you use the Prevent action, a file that Threat Emulation already identified as malware is blocked. Users cannot get the file even in Rapid Delivery mode.