Introduction to Security Management
Check Point offers effective Security Management solutions to help you keep up with constantly growing needs and challenges of your organizational network. This Administration Guide focuses on the basic Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. deployment.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. deployment.
If you are interested in deployments for organizations with multiple sites, refer to the R81.10 Multi-Domain Security Management Administration Guide.
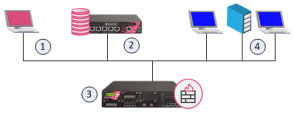
These are the basic components of Check Point security architecture.