Mirror and Decrypt
The Mirror and Decrypt feature performs these actions on your Security Gateway / Cluster / Scalable Platform Security Group:
You can add a third-party Recorder or Packet-Broker in your environment and forward to it the traffic that passes through your Security Gateway / Cluster / Security Group.
This Recorder or Packet-Broker must work in monitor (promiscuous) mode to accept the decrypted and mirrored traffic from your Security Gateway / Cluster / Security Group.
Security Gateway / Cluster / Security Group works only with one Recorder, which is directly connected to a designated physical network interface (NIC) on the Check Point Security Gateway / Cluster / Security Group.
Example Topology and Traffic Flow:
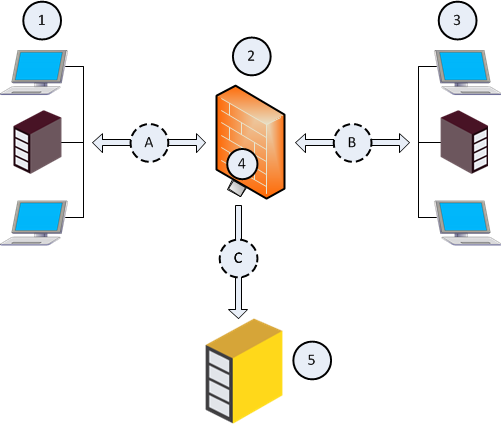
|
Item |
Description |
|---|---|
|
1 |
First network that sends and receives traffic through the Security Gateway (2). |
|
2 |
Security Gateway, through which networks (1) and (3) send and receive their traffic. |
|
3 |
Second network that sends and receives traffic through the Security Gateway (2). |
|
4 |
Designated physical interface on the Security Gateway (2). |
|
5 |
Recorder, or Packet-Broker that works in a monitor (promiscuous) mode. |
|
A |
Traffic flow between the first network (1) and the Security Gateway (2). |
|
B |
Traffic flow between the second network (3) and the Security Gateway (2). |
|
C |
Flow of the decrypted and mirrored traffic from the Security Gateway (2) to the Recorder, or Packet-Broker (5). |
Source MAC address of the decrypted and mirrored packets
|
Traffic |
Source MAC address of the decrypted |
|---|---|
|
Mirror only of all traffic |
MAC address of the designated physical interface. |
|
Mirror and Decrypt of HTTPS traffic |
00:00:00:00:00:00 |

