Getting Started
|
|
Important - Before you install or upgrade to R81.10:
|
Welcome
Thank you for choosing Check Point Software Blades for your security solution. We hope that you will be satisfied with this solution and our support services. Check Point products provide your business with the most up to date and secure solutions available today.
Check Point also delivers worldwide technical services including educational, professional, and support services through a network of Authorized Training Centers, Certified Support Partners, and Check Point technical support personnel to ensure that you get the most out of your security investment.
For additional information on the Internet Security Product Suite and other security solutions, go to https://www.checkpoint.com or call Check Point at 1(800) 429-4391.
For additional technical information, visit the Check Point Support Center.
Welcome to the Check Point family. We look forward to meeting all of your current and future network, application, and management security needs.
R81.10 Documentation
This guide is for administrators responsible for installing R81.10 on appliances and open servers that run the Gaia![]() Check Point security operating system that combines the strengths of both SecurePlatform and IPSO operating systems. Operating System.
Check Point security operating system that combines the strengths of both SecurePlatform and IPSO operating systems. Operating System.
To learn what is new in R81.10, see the R81.10 Release Notes.
See the R81.10 Home Page SK for information about the R81.10 release.
For New Check Point Customers
New Check Point customers can access the Check Point User Center to:
-
Manage users and accounts
-
Activate products
-
Get support offers
-
Open service requests
-
Search the Technical Knowledge Base
Disk Space
When you install or upgrade R81.10, the installation or upgrade wizard makes sure that there is sufficient space on the hard disk to install the Check Point products.
If there is not sufficient space on the hard disk, an error message is shown. The message states:
-
The amount of disk space necessary to install the product.
-
The directory where the product is installed.
-
The amount of free disk space that is available in the directory.
After there is sufficient disk space, install or upgrade the Check Point product.
Product Deployment Scenarios
There are different deployment scenarios for Check Point software products.
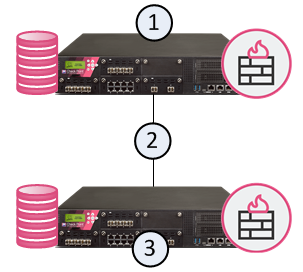
The Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. (1) and the Security Gateway
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. (1) and the Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. (3) are installed on different computers, with a network connection (2).
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. (3) are installed on different computers, with a network connection (2).
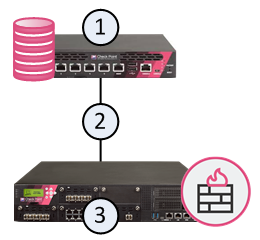
The Security Management Server![]() Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. (1) and the Security Gateway (3) are installed on the same computer (2).
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. (1) and the Security Gateway (3) are installed on the same computer (2).

A Primary Security Management Server (1) has a direct or indirect connection (2) to a Secondary Security Management Server (3).
The databases of the Security Management Servers are synchronized, manually or on a schedule, to back up one another.
The administrator makes one Security Management Server Active and the others Standby.
If the Active Security Management Server is down, the administrator can promote the Standby server to be Active.
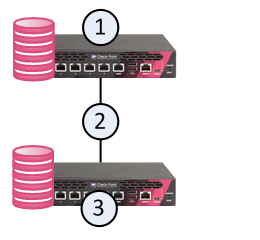
In a Full High Availability Cluster![]() Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. on two Check Point Appliances, each appliance runs both as a ClusterXL Cluster Member
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. on two Check Point Appliances, each appliance runs both as a ClusterXL Cluster Member![]() Security Gateway that is part of a cluster. and as a Security Management Server, in High Availability mode.
Security Gateway that is part of a cluster. and as a Security Management Server, in High Availability mode.
|
|
Important - You can deploy and configure a Full High Availability Cluster only on Check Point Appliances that support Standalone |
This deployment reduces the maintenance required for your systems.
In the image below, the appliances are denoted as (1) and (3).
The two appliances are connected with a direct synchronization connection (2) and work in High Availability mode:
-
The Security Management Server on one appliance (for example, 1) runs as Primary, and the Security Management Server on the other appliance (3) runs as Secondary.
-
The ClusterXL on one appliance (for example, 1) runs as Active, and the ClusterXL on the other appliance (3), runs as Standby.
-
The ClusterXL Cluster Members synchronize the information about the traffic over the synchronization connection (2).