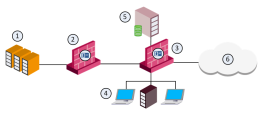
Perimeter Identity Awareness Gateway
Security Challenge
The Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. at the perimeter behaves as a primary gate for all incoming and outgoing traffic to and from your corporate network. Users in internal networks get access to the Internet resource and applications daily. Not all Internet applications and web sites are secure and some are restricted based on corporate policy. If you forbid all internal access, it affects productivity of employees that must have access as part of their daily work definition. You can control access to allowed applications with the Application Control
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. at the perimeter behaves as a primary gate for all incoming and outgoing traffic to and from your corporate network. Users in internal networks get access to the Internet resource and applications daily. Not all Internet applications and web sites are secure and some are restricted based on corporate policy. If you forbid all internal access, it affects productivity of employees that must have access as part of their daily work definition. You can control access to allowed applications with the Application Control![]() Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI. blade. But you must have a more granular Access Control Policy for user and computer identity.
Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI. blade. But you must have a more granular Access Control Policy for user and computer identity.
Use Access Roles to configure an Identity Awareness![]() Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. policy with Application Control to let an access to the applications on the Internet only to specified user groups.
Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. policy with Application Control to let an access to the applications on the Internet only to specified user groups.
Enable Identity Awareness on the perimeter Security Gateway.
Configuration Scenario
-
Configure the Security Gateway at the perimeter in Routing Mode. Create a specified external interface to the ISP (the Internet) and an internal interface points to the internal corporate network LAN.
Optional: You can create a different specified internal interface that protects DMZ servers.
-
Make sure there are no NAT or Proxy servers between the gateway and your network.

Best Practice - We recommend to use the Proxy server that is in the DMZ network.
-
Make sure that the Security Gateway connects to the internal AD domain controllers.
-
Make sure that users have an access to the internal interface of the Security Gateway.
-
Configure the Application Control blade.
|
|
Best Practice - If you have more than one perimeter Security Gateways that connect to the Internet, we recommend that you manage these Security Gateways with one Security Management Server |
Configuration Procedure
-
Enable Identity Awareness and select the applicable identity sources.
-
Create Access Roles functions that are based on Users and Computers. You can create multiple Access Roles that show different departments, user and computer groups and their location in the network.
-
Add the Access Roles to the source column of the applicable Firewall and application control policies.
This is a sample diagram for a small to medium corporate headquarters.