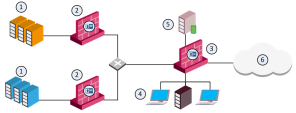
Large Scale Enterprise Environment
Security Challenge
In complex large-scale enterprise networks, you must control access from the local network to the Internet and to multiple Data Center resources. The Data Center contains sensitive corporate resources and information that must be securely protected from unauthorized access. Grant access only to policy-compliant users and computers. Protect your network and Data Center from malware, bots, and viruses.
Users in the internal networks access Internet resources and applications daily. Not all Internet applications and web sites are secure, and some are restricted by the corporate policy. If you block all internal access, it affects productivity of employees who must have access in the context of their daily work definition. You can control access to the allowed applications with the Application Control![]() Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI. blade. If you require a granular Access Control Policy works because of user and computer identity, use Access Roles with Application Control.
Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI. blade. If you require a granular Access Control Policy works because of user and computer identity, use Access Roles with Application Control.
Configuration Scenario
-
Configure or use current Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. at the perimeter and in front of the Data Center.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. at the perimeter and in front of the Data Center. -
Install the Security Gateway at the perimeter in routing mode, and use at least one external interface to the Internet and one to the internal network (make it an internal interface).

Best Practice -We recommend that you configure the Security Gateway as an inline device in front of the Data Center in Bridge Mode
 Security Gateway or Virtual System that works as a Layer 2 bridge device for easy deployment in an existing topology. to avoid network changes.
Security Gateway or Virtual System that works as a Layer 2 bridge device for easy deployment in an existing topology. to avoid network changes. -
Make sure that all Security Gateway in the Data Centers and perimeter can communicate directly with each other.
-
Make sure that there is connectivity from each Security Gateway to the Active Directory internal domain controllers.
-
Make sure that in an "Any Any Any Accept" Policy, users from the LAN can connect to the applicable resources.
-
Make sure there are no NAT or Proxy servers between the gateway and your network.

Best Practice - We recommend that you put your Proxy server in the DMZ network.
Configuration Procedure
-
Enable Identity Awareness
 Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. on the Security Gateway.
Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. on the Security Gateway. -
Select the identity source method for each Security Gateway, at the perimeter and at the Data Center.
-
Create Access Roles for users, and apply Access Roles to the applicable Firewall security rules.
-
Add Access Roles to the Policy.
-
On the Gateway Properties > Identity Awareness tab, select Share local identities with other gateways.
-
Install the Policy on the perimeter Security Gateway.
|
|
Best Practice:
|
To make a specified list of Security Gateways that share between them identity information:
-
Open Gateway Properties > Identity Awareness.
-
Select Get identities from other gateways.
-
Select the Security Gateway with the identities.