Deploying Harmony Endpoint for Linux
This section explains how to install Harmony Endpoint on Linux operating systems in a web management environment.
If the server environment includes a proxy server for Internet access, it is necessary to configure a proxy server as described in this section. Otherwise, skip to Downloading the Installation Script
Configuring a Proxy Server on the Endpoint Security Management Server
-
Connect to the command line on the Endpoint Security Management Server
 A Security Management Server that manages your Endpoint Security environment. Includes the Endpoint Security policy management and databases. It communicates with endpoint clients to update their components, policies, and protection data..
A Security Management Server that manages your Endpoint Security environment. Includes the Endpoint Security policy management and databases. It communicates with endpoint clients to update their components, policies, and protection data.. - Log in to the Expert mode..
-
Stop the Check Point services:
cpstop -
Edit the
/$UEPMDIR/engine/conf/local.propertiesfile:vi /$UEPMDIR/engine/conf/local.properties -
Add these properties:

Important - Delete the # character from the beginning of each row that you edit.
-
The proxy server's IP address:
http.proxy.host=<IP Address>
-
The proxy server's listening port:
http.proxy.port=<Port>
-
The proxy server username:
If basic authentication is enabled on the proxy server, enter the user name. If no authentication is required, leave it empty.
http.proxy.user=<Username>
-
The proxy server password:
If basic authentication is enabled on the proxy server, then enter the password. If no authentication is required, leave it empty.
http.proxy.password=<Password>
-
-
Save the changes in the file and exit the editor.
-
Start the Check Point services:
cpstart
Downloading the Installation Script
-
Download the installation script from the Policy > Deployment Policy section to the target device.
-
Follow the applicable options:
-
To allow execution permission to the file, run:
chmod +x ./<Name of Install Script>
-
To deploy both Anti-Malware
 A component of the Endpoint Security client that protects against known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. and Threat Hunting, run:
A component of the Endpoint Security client that protects against known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. and Threat Hunting, run:sudo ./<Name of Install Script> install
-
To deploy Anti-Malware only, run:
sudo ./<Name of Install Script> install --product am
-
To deploy Threat Hunting only, run:
sudo ./<Name of Install Script> install --product edr
-
To enable Threat Hunting, make sure that Threat Hunting is enabled in the applicable policy rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session..
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session..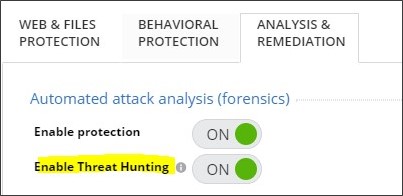
-
|
|
Notes:
|