More Network Object Types
This section includes explanations of additional network objects types.
Address Ranges
An address range is a range of IP addresses on the network, defined by the lowest and the highest IP addresses. Use an Address Range object when you cannot define a range of IP addresses by a network IP and a net mask. The Address Range objects are also necessary for the implementation of NAT and VPN.
Wildcard Objects
Wildcard objects let you define IP address objects that share a common pattern that can be permitted or denied access in a security policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection..
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection..
|
|
Note - This feature is only supported for R80.20 and above gateways. |
To create a new wildcard object
-
Open Object Explorer > New > More > Network Object > Wildcard object.
-
Enter the Wildcard IP address and Wildcard Netmask in IPv4 or IPv6 Format.
-
Click OK.
Understanding Wildcard Objects
The wildcard object contains a wildcard IP address and a wildcard netmask.
The wildcard netmask is the mask of bits that indicate which parts of the IP address must match and which do not have to match. For example:
|
Wildcard IP: |
194. |
29. |
0. |
1 |
|
Wildcard Netmask: |
0. |
0. |
3. |
0 |
The third octet represents the mask of bits. If we convert the 3 to binary, we get 00000011.
The 0 parts of the mask must match the equivalent bits of the IP address.
The 1 parts of the mask do not have to match, and can be any value.
|
0 |
0 |
0 |
0 |
0 |
0 |
1 |
1 |
|
Must match the equivalent bits in the IP address |
Do not have to match |
||||||
The binary netmask produces these possible decimal values:
|
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
|
|
|
|
|
|
|
|
|
Binary |
|
Decimal |
|
|
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
|
0 |
|
0 |
0 |
0 |
0 |
0 |
0 |
0 |
1 |
|
1 |
|
0 |
0 |
0 |
0 |
0 |
0 |
1 |
0 |
|
2 |
|
0 |
0 |
0 |
0 |
0 |
0 |
1 |
1 |
|
3 |
The netmask permits only these IP addresses:
-
194.29.0.1
-
194.29.1.1
-
192.29.2.1
-
194.29.3.1
Scenario One
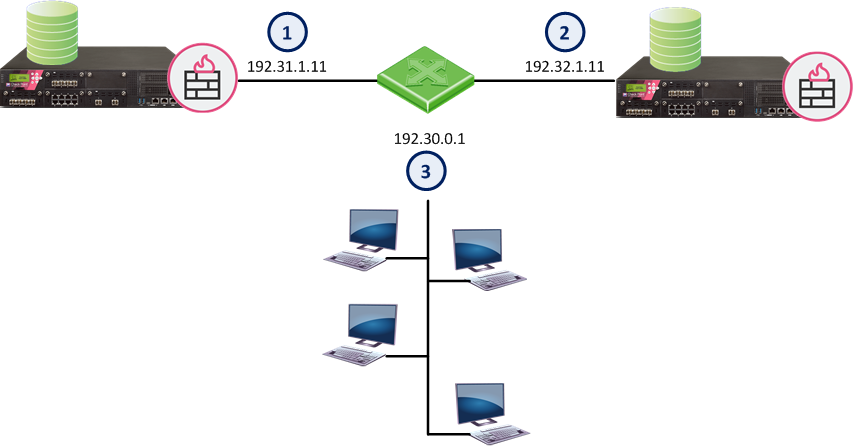
A supermarket chain has all of its cash registers on subnet 194.29.x.1, where x defines the region. In this use case, all the cash registers in this region must have access to the database server at 194.30.1.1.
Instead of defining 256 hosts (194.29.0.1, 194.29.1.1, 194.29.2.1....194.29.255.1), the administrator creates a wildcard object that represents all the cash registers in the region:
|
Wildcard IP: |
194. |
29. |
0. |
1 |
|
Wildcard Mask: |
0. |
0. |
255. |
0 |
The wildcard object can now be added to the Access Control Policy.
|
Source |
Destination |
Action |
Track |
|---|---|---|---|
|
Wildcard Object |
Database server object |
Accept |
Log |
Scenario Two
In this use case, a supermarket chain has stores in Europe and Asia.
The 192.30.0-255.1 network contains both the Asian and European regions, and the stores within those regions.
|
Item |
Description |
|---|---|
|
1 |
Database Server for Europe |
|
2 |
Database Server for Asia |
|
3 |
European and Asia network |
The administrator wants stores in the European and Asia regions to access different database servers. In this topology, the third octet of the European and Asia network's IP address will be subject to a wildcard. The first four bits of the wildcard will represent the region and the last four bits will represent the store number.
|
Bits that represent the region |
Bits that represent the store number |
|
0000 |
0000 |
In the Wildcard IP:
-
The Asia region is represented by 0001xxxx (Region 1 in decimal)
-
The European region is represented by 0010xxxx (Region 2 in decimal)
In binary:
|
Binary |
|
Decimal |
|
Region |
Store |
|
|
0001 |
0000 |
16 - Asia Region |
|
0010 |
0000 |
32 - European Region |
To include all the stores of a particular region, the last four bits of the wildcard mask must be set to 1 (15 in Decimal):
|
Binary |
|
Decimal |
|
Region |
Store |
|
|
xxxx |
1111 |
15 - all Asian stores |
|
xxxx |
1111 |
15 - all European stores |
A wildcard object that represents all the Asian stores will look like this:
|
Wildcard IP address |
192.30.16.1 |
(The region) |
|
Wildcard netmask |
0.0.15.0 |
(for stores in the region) |
For this range of IP addresses: 192.30.16-31.1
A wildcard object that represents all the European stores will look like this:
|
Wildcard IP address |
192.30.32.1 |
(the region) |
|
Wildcard netmask |
0.0.15.0 |
(for stores in the region) |
For this range of IP addresses: 192.30.32-47.1
The administrator can now use these wildcard objects in the Access Control Policy:
|
Source |
Destination |
Action |
Track |
|---|---|---|---|
|
Asian Stores Wildcard |
Database Server for Asia |
Accept |
Log |
|
European Stores Wildcard |
Database Server for Europe |
Accept |
Log |
Scenario Three
In this scenario, the netmask bits are not consecutive.
|
Wildcard IP |
1 |
1 |
0 |
1 |
|
Wildcard mask |
0 |
0 |
5 |
0 |
|
Wildcard IP |
00000001.00000001.00000000.00000001 |
|
Wildcard Mask |
00000000.00000000.00000101.00000000 |
Mask:
|
00 |
01 |
02 |
03 |
04 |
05 |
06 |
07 |
08 |
09 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 |
30 |
31 |
|
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
1 |
0 |
1 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
Which will match only these IP addresses:
|
IP Address |
Binary |
Comment |
|---|---|---|
|
1.1.0.1 |
00000001.00000001.00000000.00000001 |
The IP address itself |
|
1.1.1.1 |
00000001.00000001.00000001.00000001 |
The equivalent bit at position 23 does not matter |
|
1.1.4.1 |
00000001.00000001.00000100.00000001 |
The equivalent bit at position 21 does not matter |
|
1.1.5.1 |
00000001.00000001.00000101.00000001 |
The equivalent bits at positions 21 and 23 do not matter |
IPv6
The same principles apply to IPv6 addresses. For example, if the wildcard object has these values:
|
IPv6 Address |
2001::1:10:0:1:41 |
|
Wildcard netmask |
0::ff:0:0 |
The wildcard will match: 2001::1:10:0-255:1:41
Domains
A Domain object lets you define a host or DNS domain by its name only. It is not necessary to have the IP address of the site.
You can use the Domain object in the source and destination columns of an Access Control Policy.
You can configure a Domain object in two ways:
-
Select FQDN
In the object name, use the Fully Qualified Domain Name (FQDN). Use the format .
x.y.z(with a dot "." before the FQDN). For example, if you use .www.example.comthen the Gateway matcheswww.example.comThis option is supported for R80.10 and higher, and is the default. It is more accurate and faster than the non-FQDN option.
The Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. looks up the FQDN with a direct DNS query, and uses the result in the Rule Base
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. looks up the FQDN with a direct DNS query, and uses the result in the Rule Base![]() All rules configured in a given Security Policy. Synonym: Rulebase..
All rules configured in a given Security Policy. Synonym: Rulebase..
This option supports SecureXL![]() Check Point product on a Security Gateway that accelerates IPv4 and IPv6 traffic that passes through a Security Gateway. Accept templates. Using domain objects with this option in a rule
Check Point product on a Security Gateway that accelerates IPv4 and IPv6 traffic that passes through a Security Gateway. Accept templates. Using domain objects with this option in a rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. has no effect on the performance of the rule, or of the rules that come after it.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. has no effect on the performance of the rule, or of the rules that come after it.
-
Clear FQDN
This option enforces the domain and its sub-domains. In the object name, use the format .x.y for the name. For example, use .example.com or .example.co.uk for the name. If you use .example.com, then the Gateway matches www.example.com and support.example.com
The Gateway does the name resolution using DNS reverse lookups, which can be inaccurate. The Gateway uses the result in the Rule Base, and caches the result to use again.
When upgrading from R77, this option is enforced.
Dynamic Objects
A dynamic object is a "logical" object where the IP address is resolved differently for each Security Gateway, using the dynamic_objects command.
For Security Gateways R80.10 and higher, dynamic objects support SecureXL Accept templates. Therefore, there is no performance impact on a rule that uses a dynamic object, or on rules that come after it.
Dynamic Objects are predefined for LocalMachine-all-interfaces. The DAIP computer interfaces (static and dynamic) are resolved into this object.
Security Zones
Security Zones let you to create a strong Access Control Policy that controls the traffic between parts of the network.
A Security Zone object represents a part of the network (for example, the internal network or the external network). You assign a network interface of a Security Gateway to a Security Zone. You can then use the Security Zone objects in the Source and Destination columns of the Rule Base.
Use Security Zones to:
-
Simplify the Policy. Apply the same rule to many Gateways.
-
Add networks to Gateways interfaces without changing the Rule Base.
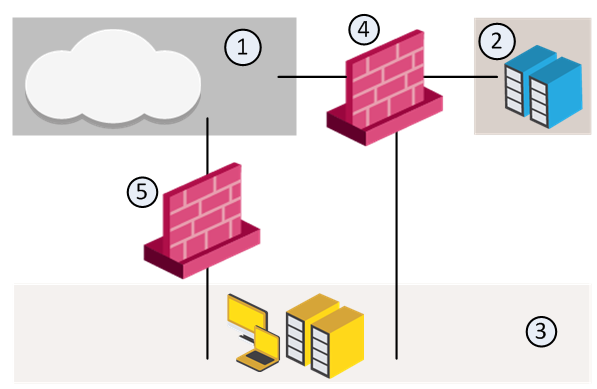
For example, in the diagram, we have three Security Zones for a typical network: ExternalZone (1), DMZZone (2) and InternalZone (3).
-
Gateway (4) has three interfaces. One interface is assigned to ExternalZone (1), one interface is assigned to DMZZone (2), and one interface is assigned to InternalZone (3).
-
Gateway (5) has two interfaces. One interface is assigned to ExternalZone (1) and one interface is assigned to InternalZone (3).
A Security Gateway interface can belong to only one Security Zone. Interfaces to different networks can be in the same Security Zone.
Workflow
-
Define Security Zone objects. Or, use the predefined Security Zones (see Predefined Security Zones ).
-
Assign Gateway interfaces to Security Zones (see Creating and Assigning Security Zones ).
-
Use the Security Zone objects in the Source and Destination of a rule. For example:
-
Install the Access Control Policy (see Installing the Access Control Policy).
Creating and Assigning Security Zones
Before you can use Security Zones in the Rule Base, you must assign Gateway interfaces to Security Zones.
To create a Security Zone
-
In the Objects bar (F11), click New > More > Network Object > Security Zone.
The Security Zone window opens.
-
Enter a name for the Security Zone.
-
Enter an optional comment or tag.
-
Click OK.
To assign an interface to a Security Zone
-
In the Gateways & Servers view, right-click a Security Gateway object and select Edit.
The Gateway Properties window opens.
-
In the Network Management pane, right-click an interface and select Edit.
The Interface window opens. The Topology area of the General pane shows the Security Zone to which the interface is already bound. By default, the Security Zone is calculated according to where the interface Leads To.
-
Click Modify.
The Topology Settings window opens.
-
In the Security Zone area, click User Defined and select Specify Security Zone.
-
From the drop-down box, select a Security Zone.
Or click New to create a new one.
-
Click OK.
Predefined Security Zones
These are the predefined Security Zones, and their intended purposes:
-
WirelessZone - Networks that can be accessed by users and applications with a wireless connection.
-
ExternalZone - Networks that are not secure, such as the Internet and other external networks.
-
DMZZone - A DMZ (demilitarized zone) is sometimes referred to as a perimeter network. It contains company servers that can be accessed from external sources.
A DMZ lets external users and applications access specific internal servers, but prevents the external users accessing secure company networks. Add rules to the Security Gateway Rule Base that allow traffic to the company DMZ. For example, a rule that allows HTTP and HTTPs traffic to your web server in the DMZ.
-
InternalZone - Company networks with sensitive data that must be protected and used only by authenticated users.
Limitations
-
NAT policy supports Security Zones only for R81 Security Gateways and higher.
-
The Threat Prevention Policy supports Security Zones only for R81 Security Gateways and higher.
-
If the clean-up rule contains Security Zones, it might prevent the creation of Drop templates for that rule.
Externally Managed Gateways/Hosts
An Externally Managed Security Gateway or a Host is a gateway or a Host which has Check Point software installed on it. This Externally Managed gateway is managed by an external Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server.. While it does not receive the Check Point Security Policy Security Policy, it can participate in Check Point VPN communities and solutions.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server.. While it does not receive the Check Point Security Policy Security Policy, it can participate in Check Point VPN communities and solutions.
Interoperable Devices
An Interoperable Device is a device that has no Check Point Software Blades installed.
The Interoperable Device:
-
Cannot have a policy installed on it
-
Can participate in Check Point VPN communities and solutions.
VoIP Domains
There are five types of VoIP Domain objects:
-
VoIP Domain SIP Proxy
-
VoIP Domain H.323 Gatekeeper
-
VoIP Domain H.323 Gateway
-
VoIP Domain MGCP Call Agent
-
VoIP Domain SCCP CallManager
In many VoIP networks, the control signals follow a different route through the network than the media. This is the case when the call is managed by a signal routing device. Signal routing is done in SIP by the Redirect Server, Registrar, and/or Proxy. In SIP, signal routing is done by the Gatekeeper and/or Gateway.
Enforcing signal routing locations is an important aspect of VoIP security. It is possible to specify the endpoints that the signal routing device is allowed to manage. This set of locations is called a VoIP Domain. For more information, see the R80.40 VoIP Administration Guide.
Logical Servers
A Logical Server is a group of machines that provides the same services. The workload of this group is distributed between all its members.
When a Server group is stipulated in the Servers group field, the client is bound to this physical server. In Persistent server mode the client and the physical server are bound for the duration of the session.
-
Persistency by Service - once a client is connected to a physical server for a specified service, subsequent connection to the same Logical Server and the same service will be redirected to the same physical server for the duration of the session.
-
Persistency by Server - once a client is connected to a physical server, subsequent connections to the same Logical Server (for any service) will be redirected to the same physical server for the duration of the session.
Balance Method
The load balancing algorithm stipulates how the traffic is balanced between the servers. There are several types of balancing methods:
-
Server Load - The Security Gateway determines which Security Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. is best equipped to handle the new connection.
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. is best equipped to handle the new connection. -
Round Trip Time - On the basis of the shortest round trip time between Security Gateway and the servers, executed by a simple ping, the Security Gateway determines which Security Management Server is best equipped to handle the new connection.
-
Round Robin - the new connection is assigned to the first available server.
-
Random - the new connection is assigned to a server at random.
-
Domain - the new connection is assigned to a server based on domain names.