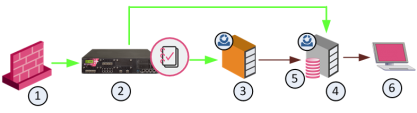
The SmartEvent Architecture
SmartEvent has some components that work together to help track down security threats and make your network more secure.
This is how they work together. The numbers refer to the diagram:
-
SmartEvent Correlation Unit
 SmartEvent software component on a SmartEvent Server that analyzes logs and detects events. (3) analyzes log entries on Log Servers (2) and stores the event
SmartEvent software component on a SmartEvent Server that analyzes logs and detects events. (3) analyzes log entries on Log Servers (2) and stores the event Record of a security or network incident that is based on one or more logs, and on a customizable set of rules that are defined in the Event Policy. in the same way the log server stores logs.
Record of a security or network incident that is based on one or more logs, and on a customizable set of rules that are defined in the Event Policy. in the same way the log server stores logs. -
SmartEvent Server
 Dedicated Check Point server with the enabled SmartEvent Software Blade that hosts the events database. (4) contains the Events Database (5).
Dedicated Check Point server with the enabled SmartEvent Software Blade that hosts the events database. (4) contains the Events Database (5). -
The SmartEvent and SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. clients (6) manage the SmartEvent Server.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. clients (6) manage the SmartEvent Server.
|
Item |
Description |
Purpose |
|---|---|---|
|
|
|
Log data flow |
|
|
|
Event data flow |
|
1 |
Sends logs to the Log Server |
|
|
2 |
Log Server |
Stores logs. |
|
3 |
SmartEvent Correlation Unit |
Identifies events: Analyzes each log entry from a Log Server, and looks for patterns according to the installed Event Policy. The logs contain data from Check Point products and certain third-party devices. When a threat pattern is identified, the SmartEvent Correlation Unit forwards the event to the SmartEvent Server. |
|
4 |
SmartEvent Server |
The SmartEvent Server:
|
|
5 |
Events database |
Stores events. Located on the SmartEvent Server. |
|
6 |
SmartEvent client |
Shows the received events. Uses the clients to manage events (for example: to filter and close events), fine-tunes, and installs the Event Policy. The clients are:
|
The SmartEvent components can be installed on one computer (that is, a standalone![]() Configuration in which the Security Gateway and the Security Management Server products are installed and configured on the same server. deployment) or multiple computers and sites (a distributed deployment). To handle higher volumes of logging activity, we recommend a distributed deployment. Each SmartEvent Correlation Unit can analyze logs from more than one Log Server or Domain Log Server.
Configuration in which the Security Gateway and the Security Management Server products are installed and configured on the same server. deployment) or multiple computers and sites (a distributed deployment). To handle higher volumes of logging activity, we recommend a distributed deployment. Each SmartEvent Correlation Unit can analyze logs from more than one Log Server or Domain Log Server.