Deployment Scenarios
Security Challenge
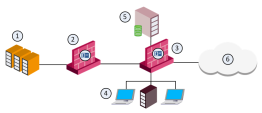
The Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. at the perimeter behaves as a main gate for all incoming and outgoing traffic to and from your corporate network. Users in internal networks access the Internet resource and applications daily. Not all Internet applications and web sites are secure and some are restricted according to corporate policy. If you block all internal access, it will affect productivity of employees that must have access as part of their daily work definition. You can control access to allowed applications with the Application Control
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. at the perimeter behaves as a main gate for all incoming and outgoing traffic to and from your corporate network. Users in internal networks access the Internet resource and applications daily. Not all Internet applications and web sites are secure and some are restricted according to corporate policy. If you block all internal access, it will affect productivity of employees that must have access as part of their daily work definition. You can control access to allowed applications with the Application Control![]() Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI. blade. However, you require a more granular Access Control Policy for user and computer identity.
Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI. blade. However, you require a more granular Access Control Policy for user and computer identity.
Access roles let you configure an identity aware policy with Application Control, to allow access only to specified user groups to the applications on the Internet.
Enable Identity Awareness![]() Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. on the perimeter Security Gateway.
Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. on the perimeter Security Gateway.
Deployment Scenario
-
Deploy the Security Gateway at the perimeter in routing mode and define an external interface towards the ISP (the Internet) and an internal interface points to the internal corporate network LAN.
Optional: You can define another internal interface, which protects DMZ servers.
-
Make sure there are no NAT or Proxy servers between the gateway and your network.
 >
>
Best Practice - We recommend that the Proxy server be in the DMZ network.
-
Check that the Security Gateway has connectivity to the internal AD domain controllers.
-
Make sure that users can reach the internal interface of the Security Gateway.
-
Configure the Application Control blade.
-
If you have several perimeter Security Gateway leading to the Internet, we recommend that you manage these Security Gateway with one Security Management Server
 Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. and SmartConsole
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. and SmartConsole Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. to deploy the relevant Security Policy
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. to deploy the relevant Security Policy Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection..
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection..
Configuration
-
Enable Identity Awareness and select the appropriate identity sources.
-
Create Access Roles based on users and computers. You can create multiple Access Roles that represent different departments, user and computer groups and their location in the network.
-
Add the Access Roles to the source column of the relevant Firewall and application control policies.
This is a sample diagram for a small to medium corporate headquarters.
Security Challenge
The Data Center contains sensitive corporate resources and information that you must securely protect from unauthorized access. You must also protect it from malwares and viruses that can harm databases and steal corporate information. Access to the Data Center and particularly to certain applications must be granted only to compliant users and computers.
Deployment Scenario
-
Deploy the Security Gateway inline in front of the Date Center core switch, protecting access to the Data Center from the LAN.
-
 >
>
Best Practice - We recommend that you deploy the Security Gateway in the bridge mode
 Security Gateway or Virtual System that works as a Layer 2 bridge device for easy deployment in an existing topology., to avoid any changes in the network. However, IP routing mode is also supported.
Security Gateway or Virtual System that works as a Layer 2 bridge device for easy deployment in an existing topology., to avoid any changes in the network. However, IP routing mode is also supported. -
Define at least two interfaces on the Security Gateway and configure them to be internal or bridged.
-
Make sure that the Security Gateway has connectivity to the Active Directory and all relevant internal domain controllers in the network (LAN).
-
Make sure that users from the LAN can connect to the Data Center through the Security Gateway with an "Any Any Any Accept" policy.
-
Make sure that you do not have a proxy or NAT device between the Security Gateway and users or the LAN.
Configuration
-
Enable Identity Awareness on the Security Gateway and select identity sources.
-
Create Access Roles for users and apply the Access Roles to relevant Access Control Policy rules.
Security Challenge
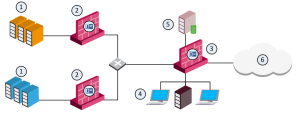
In complex large-scale enterprise networks, you must control access from the local network to the Internet and to multiple Data Center resources. The Data Center contains sensitive corporate resources and information that must be securely protected from unauthorized access. Grant access only to policy-compliant users and computers. Protect your network and Data Center from malware, bots, and viruses.
Users in the internal networks access Internet resources and applications daily. Not all Internet applications and web sites are secure, and some are restricted by the corporate policy. If you block all internal access, it will affect productivity of employees who must have access in the context of their daily work definition. You can control access to the allowed applications with the Application Control blade. If you require a granular Access Control Policy based on user and computer identity, use Access Roles with Application Control.
Deployment Scenario
-
Deploy or use existing Security Gateway at the perimeter and in front of the Data Center.
-
Install the Security Gateway at the perimeter in routing mode, and use at least one external interface to the Internet and one to the internal network (define it as an internal interface).
-
Deploy the Security Gateway as an inline device in front of the Data Center in bridge mode to avoid network changes. This is not required, but is recommended. Nonetheless, IP routing mode is also supported.
-
Make sure that all Security Gateway in the Data Centers and perimeter can communicate directly with each other.
-
Best Practice - We recommend that you manage the Security Gateway from one Security Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. and SmartConsole.
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. and SmartConsole. -
Make sure that there is connectivity from each Security Gateway to the Active Directory internal domain controllers.
-
Make sure that in an "Any Any Any Accept" Policy, users from the LAN can connect to the applicable resources.
-
Make sure there are no NAT or Proxy servers between the gateway and your network.
 >
>
Best Practice - We recommend that you put your Proxy server in the DMZ network.
Configuration
-
Enable Identity Awareness on the Security Gateway.
-
Choose the identity source method for each Security Gateway, at the perimeter and at the Data Center.
-
Create Access Roles for users, and apply Access Roles to the applicable Firewall security rules.
-
Add Access Roles to the Policy.
-
On the Gateway Properties > Identity Awareness tab, select Share local identities with other gateways.
-
Install the Policy on the perimeter Security Gateway.
|
|
Best Practice - AD Query Recommended Configuration - When you enable AD Query |
|
|
Best Practice - Identity Agents Recommended Configuration:
|
To define a list of Security Gateway, between which identity information is shared:
-
Open Gateway Properties > Identity Awareness.
-
Select Get identities from other gateways.
-
Select the Security Gateway with the identities.
Security Challenge
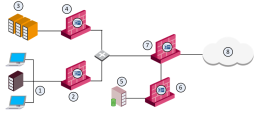
Networks consist of different network segments and subnets where your internal users reside. Users that connect to the network can potentially spread viruses and malwares across the network that can infect other computers and servers on the network. You want to make sure that only compliant users and computers can pass and connect across multiple network segments, as well as authenticate users connecting to the servers and the Internet.
Deployment Scenario
|
|
Best Practice - We recommend that you deploy Security Gateway close to access networks before the core switch. |
-
Access between the segments is controlled by the Security Gateway.
-
Access between the LAN and Data Center is controlled by the Security Gateway.
-
Access between the LAN and the Internet is controlled by the Security Gateway either at each segment or at the perimeter Security Gateway.
|
|
Best Practice - We recommend that you deploy the Security Gateway in bridge mode to avoid network and routing changes. |
-
Each Security Gateway of a particular segment authenticates users with the selected method.
-
Each Security Gateway of a particular segment authenticates users with the selected method.
Configuration
-
Deploy Security Gateway in each segment in bridge mode.
-
Make sure that there is no proxy or NAT device between the Security Gateway and the LAN.
-
Make sure that the Security Gateway can communicate with the Active Directory domain controller deployed in each segment (replicated domain controllers).
If there is a general domain controller that serves all users across the segments, make sure that all Security Gateway can connect to this domain controller.
-
Enable Identity Awareness on each Security Gateway and select an appropriate identity source method.
-
In the Identity Awareness tab, clear the Share local identities with other gateways option.
If you want to share identities with one Security Gateway, for example, the perimeter Security Gateway, keep this option selected and disable Get identities from other gateways in the segment Security Gateway. Then go to the perimeter Security Gateway and select Get identities from other gateways.
-
If you want to use Identity Agents, then define the particular Security Gateway DNS/IP in the agent Security Gateway configuration per access segment.
Security Challenge
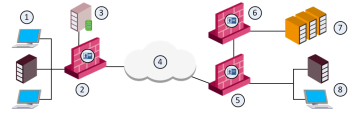
In distributed enterprises, there is a potential risk of malware and viruses spreading from remote branch offices over VPN links to the corporate internal networks. There is also a challenge of how to provide authorized access to users that come from remote branch offices that request and want to access the Data Center and the Internet.
Deployment Scenario
|
|
Best Practice - We recommend that you deploy Security Gateway at the remote branch offices and at headquarters in front of the Data Center and at the perimeter. . |
-
At remote branch offices, you can deploy low capacity Security Gateway due to a relatively low number of users.
-
Deploy the remote branch Security Gateway in IP routing mode and have them function as a perimeter Firewall and VPN gateway, establishing a VPN link to the corporate Security Gateway.
 >
>
Best Practice - At the corporate headquarters, we recommend that you deploy Data Center Security Gateway to protect access to Data Center resources and applications, as well as a perimeter Security Gateway. You can install the Data Center Security Gateway in bridge mode to avoid changes to the existing network.
-
In this scenario, users from the branch office are identified by the local branch office Security Gateway before connecting to the corporate network over VPN.
-
The identities learned by the branch office Security Gateway are then shared with the headquarters' internal and perimeter Security Gateway. When a user from a branch office attempts to connect to the Data Center, the user is identified by the Security Gateway at the headquarters Data Center without the need for additional authentication.
Configuration
-
Select a Security Gateway according to a performance guideline for your remote branch offices.
-
Deploy the Security Gateway at the branch offices in routing mode. Define VPN site-to-site if necessary.
-
Deploy Security Gateway inline at the Data Center. We recommend using bridge mode.
-
Deploy a Security Gateway at the perimeter that protects the internal network in routing mode. The perimeter Security Gateway can serve as a VPN Security Gateway for branch offices as well.
-
If you have Active Directory domain controllers replicated across your branch offices make sure that local Security Gateway can communicate with the domain controller. In case you do not have a local domain controller, make sure that the Security Gateway can access the headquarters' internal domain controller over VPN.
-
Enable Identity Awareness and select the appropriate methods to get identity.
-
Create an Access Role
 Access Role objects let you configure network access according to: Networks, Users and user groups, Computers and computer groups, Remote Access Clients. After you activate the Identity Awareness Software Blade, you can create Access Role objects and use them in the Source and Destination columns of Access Control Policy rules. and apply the roles in the Security Policy on the branch office Security Gateway, perimeter and Data Center Security Gateway.
Access Role objects let you configure network access according to: Networks, Users and user groups, Computers and computer groups, Remote Access Clients. After you activate the Identity Awareness Software Blade, you can create Access Role objects and use them in the Source and Destination columns of Access Control Policy rules. and apply the roles in the Security Policy on the branch office Security Gateway, perimeter and Data Center Security Gateway. -
Share identities between the branch offices with the headquarters and Data Center Security Gateway. In the Identity Awareness tab, select Get identities from other gateways and Share local identities with other gateways.
|
|
Best Practice - AD Query Recommended Configuration When you use AD Query to authenticate users from the local and branch offices, we recommend that you only configure a local domain controller list per site in the relevant Security Gateway. For example, if you have a branch office Security Gateway and a Data Center Security Gateway, enable AD Query on all Security Gateway. On the branch office Security Gateway, select the Active Directory domain controllers replications installed in the branch office only. On the Data Center Security Gateway, configure a list of domain controllers installed in the internal headquarters network. It is not necessary to configure all domain controllers available in the network, since the identity information is shared between branch and internal Security Gateway accordingly. |
|
|
Best Practice - Identity Agents Recommended Configuration. When using Identity Agents, we recommend that you configure the local branch office Security Gateway DNS/IP on the agent. The agents connect to the local Security Gateway and the user is authenticated, identities are shared with the internal headquarters Security Gateway. |
Security Challenge
You use wireless networks to grant access to employees that use Wi-Fi enabled devices, guests and contractors. Guests and contractors in some cases cannot use the corporate wired network connection and must connect through WLAN. Furthermore, it is not intended for guests and contractors to install any endpoint agents on their devices.
Wireless access is also intensively used to connect mobile devices such as smartphones where agents can be installed. These devices are not part of the Active Directory domain. Wireless networks do not give an applicable level of security in terms of network access.
Deployment Scenario
-
Deploy the Security Gateway in bridge mode in front of the Wireless Switch.
-
Make sure that the Security Gateway can access the Internet or any other required resource in the network.
-
Make sure that the Security Gateway can communicate with the authentication server, such as Active Directory or RADIUS.
-
Check that there is no NAT or proxy device between the Security Gateway and the WLAN network.
Configuration
-
Enable Identity Awareness on the Security Gateway.
-
Select Browser-Based Authentication
 Authentication of users in Check Point Identity Awareness web portal - Captive Portal, to which users connect with their web browser to log in and authenticate. as an identity source.
Authentication of users in Check Point Identity Awareness web portal - Captive Portal, to which users connect with their web browser to log in and authenticate. as an identity source. -
In the Gateway properties > Identity Awareness tab > Browser-Based Authentication Settings, select Unregistered guests login and in Settings, select the fields you want guests to fill when they register.
-
Select Log out users when they close the portal browser.
Security Challenge
You have several Security Gateway that protect the Data Center or Internet access where access is based on identity acquisition. The Security Gateway run different blades and deal with heavy traffic inspection.
To avoid an impact on performance of the Security Gateway in terms of user identity acquisition and authentication, it is possible to offload this functionality to a separate Security Gateway. The dedicated Security Gateway is responsible for acquiring user identity, performing authentication and sharing learned identities with all Security Gateway in the network.
Deployment Scenario
In this deployment scenario, you have to choose an appropriate appliance to deploy as the dedicated Identity Awareness Security Gateway. All users authenticate with this Security Gateway.
If you enable AD Query, the dedicated Security Gateway should communicate with all Active Directory domain controllers over WMI.
Configuration
-
On the dedicated identity acquisition Security Gateway, enable the Identity Awareness feature and select the identity method.
-
On the Security Gateway, enable Identity Awareness and select Get identities from other gateways and Share local identities with other gateways.