Group of Bonds
Introduction
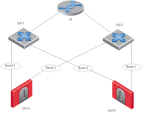
Group of Bonds, which is a logical group of existing Bond interfaces, provides additional link redundancy.
-
There is one router - R
-
There are two switches that connect to the router R: SW-1 and SW-2
-
There are two Cluster
 Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. Members GW-A (Active
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. Members GW-A (Active State of a Cluster Member that is fully operational: (1) In ClusterXL, this applies to the state of the Security Gateway component (2) In 3rd-party / OPSEC cluster, this applies to the state of the cluster State Synchronization mechanism.) and GW-B (Standby
State of a Cluster Member that is fully operational: (1) In ClusterXL, this applies to the state of the Security Gateway component (2) In 3rd-party / OPSEC cluster, this applies to the state of the cluster State Synchronization mechanism.) and GW-B (Standby State of a Cluster Member that is ready to be promoted to Active state (if the current Active Cluster Member fails). Applies only to ClusterXL High Availability Mode.)
State of a Cluster Member that is ready to be promoted to Active state (if the current Active Cluster Member fails). Applies only to ClusterXL High Availability Mode.) -
There are two Bond interfaces on each Cluster Member
 Security Gateway that is part of a cluster.: Bond-1 and Bond-2
Security Gateway that is part of a cluster.: Bond-1 and Bond-2 -
On the Cluster Member GW-A:
-
Bond-1 interface connects to the switch SW-1
-
Bond-2 interface connects to the switch SW-2
-
-
On the Cluster Member GW-B:
-
Bond-1 interface connects to the switch SW-2
-
Bond-2 interface connects to the switch SW-1
-
-
The Cluster Member GW-A is the Active and the Cluster Member GW-B is the Standby.
-
On the Cluster Member GW-A, the Bond-1 interface fails.
-
On the Cluster Member GW-A, the Critical Device
 A special software device on each Cluster Member, through which the critical aspects for cluster operation are monitored. When the critical monitored component on a Cluster Member fails to report its state on time, or when its state is reported as problematic, the state of that member is immediately changed to Down. The complete list of the configured critical devices (pnotes) is printed by the 'cphaprob -ia list' command or 'show cluster members pnotes all' command. Synonyms: Pnote, Problem Notification. Interface Active Check reports its state as "
A special software device on each Cluster Member, through which the critical aspects for cluster operation are monitored. When the critical monitored component on a Cluster Member fails to report its state on time, or when its state is reported as problematic, the state of that member is immediately changed to Down. The complete list of the configured critical devices (pnotes) is printed by the 'cphaprob -ia list' command or 'show cluster members pnotes all' command. Synonyms: Pnote, Problem Notification. Interface Active Check reports its state as "problem". -
The Cluster Member GW-A changes its cluster state from Active to Down
 State of a Cluster Member during a failure when one of the Critical Devices reports its state as "problem": In ClusterXL, applies to the state of the Security Gateway component; in 3rd-party / OPSEC cluster, applies to the state of the State Synchronization mechanism. A Cluster Member in this state does not process any traffic passing through cluster..
State of a Cluster Member during a failure when one of the Critical Devices reports its state as "problem": In ClusterXL, applies to the state of the Security Gateway component; in 3rd-party / OPSEC cluster, applies to the state of the State Synchronization mechanism. A Cluster Member in this state does not process any traffic passing through cluster.. -
The cluster fails over - the Cluster Member GW-B changes its cluster state from Standby to Active.
This is not the desired behavior, because the Cluster Member GW-A connects not only to the switch SW-1, but also to the switch SW-2. In our example topology, there is no actual reason to fail-over from the Cluster Member GW-A to the Cluster Member GW-B.
In order to overcome this problem, Cluster Members use the Group of Bonds consisting of Bond-1 and Bond-2. The Group of Bonds fails only when both Bond interfaces fail on the Cluster Member. Only then the cluster fails over.
-
The Cluster Member GW-A is the Active and the Cluster Member GW-B is the Standby.
-
On the Cluster Member GW-A, the Bond-1 interface fails.
-
On the Cluster Member GW-A, the Critical Device Interface Active Check reports its state as "
problem". -
The Cluster Member GW-A does not change its cluster state from Active to Down.
-
On the Cluster Member GW-A, the Bond-2 interface fails as well.
-
The Cluster Member GW-A changes its cluster state from Active to Down.
-
The cluster fails over - the Cluster Member GW-B changes its cluster state from Standby to Active.
Creating a new Group of Bonds
This procedure lets you create a new Group of Bonds.
|
|
Important - In a Cluster, you must configure all the Cluster Members in the same way. |
-
Connect to the command line on the Cluster Member.
-
Log in to the Expert mode.
-
In VSX
 Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts. Cluster, switch to the context of the applicable Virtual System:
Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts. Cluster, switch to the context of the applicable Virtual System:vsenv <VSID> -
Modify the current
$FWDIR/boot/modules/fwkern.conffile:-
cp -v $FWDIR/boot/modules/fwkern.conf{,_BKP} -
Edit the current file:
vi $FWDIR/boot/modules/fwkern.conf -
Add these two lines at the bottom of the file (spaces or comments are not allowed):
fwha_group_of_bonds_str=<Name for Group of Bonds>:<List of all Bonds in this Group separated by comma>fwha_arp_probe_method=1Example:
fwha_group_of_bonds_str=GoB0:bond0,bond1;GoB1:bond2,bond3fwha_arp_probe_method=1
Note - The kernel parameter "
fwha_arp_probe_method" configures the Cluster Member to use the Virtual IP address as the Source IP address in the ARP Requests during the probing If a Cluster Member fails to receive status for another member (does not receive CCP packets from that member) on a given segment, Cluster Member will probe that segment in an attempt to illicit a response. The purpose of such probes is to detect the nature of possible interface failures, and to determine which module has the problem. The outcome of this probe will determine what action is taken next (change the state of an interface, or of a Cluster Member). of the local network.
If a Cluster Member fails to receive status for another member (does not receive CCP packets from that member) on a given segment, Cluster Member will probe that segment in an attempt to illicit a response. The purpose of such probes is to detect the nature of possible interface failures, and to determine which module has the problem. The outcome of this probe will determine what action is taken next (change the state of an interface, or of a Cluster Member). of the local network. -
Save the changes in the file and exit the editor.
-
-
Change the value of the kernel parameter
fwha_group_of_bonds_strto add the Group of Bonds on-the-fly:fw ctl set str fwha_group_of_bonds_str '<Name for Group of Bonds>:<List of all Bonds in this Group separated by comma>'Example:
fw ctl set str fwha_group_of_bonds_str 'GoB0:bond0,bond1;GoB1:bond2,bond3'
Notes:
-
The apostrophe characters are mandatory part of the syntax.
-
Spaces are not allowed in the value of the kernel parameter
fwha_group_of_bonds_str.
-
-
Change the value of the kernel parameter
fwha_arp_probe_methodon-the-fly:fw ctl set int fwha_arp_probe_method 1 -
Make sure the Cluster Member accepted the new configuration:
fw ctl get str fwha_group_of_bonds_strfw ctl get int fwha_arp_probe_method -
In SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., install the Access Control Policy on the cluster object.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., install the Access Control Policy on the cluster object.
Adding a Bond interface to the existing Group of Bonds
This procedure lets you add an additional bond interface to the existing Group of Bonds.
|
|
Important - In a Cluster, you must configure all the Cluster Members in the same way. |
-
Connect to the command line on the Cluster Member.
-
In VSX Cluster, switch to the context of the applicable Virtual System:
vsenv <VSID> -
Log in to the Expert mode.
-
Modify the current
$FWDIR/boot/modules/fwkern.conffile:-
Backup the current file:
cp -v $FWDIR/boot/modules/fwkern.conf{,_BKP} -
Edit the current file:
vi $FWDIR/boot/modules/fwkern.conf -
Edit the value of the kernel parameter
fwha_group_of_bonds_strto add the Bond interface to the existing Group of Bonds.Example:
fwha_group_of_bonds_str=GoB0:bond0,bond1;GoB1:bond2,bond3,bond4 -
Save the changes in the file and exit the editor.
-
-
Get the current value of the kernel parameter
fwha_group_of_bonds_strand copy it:fw ctl get str fwha_group_of_bonds_str -
Reset the current value of the kernel parameter
fwha_group_of_bonds_str:fw ctl set str fwha_group_of_bonds_str '' -
Make sure the Cluster Member reset the value of the kernel parameter
fwha_group_of_bonds_str:fw ctl get str fwha_group_of_bonds_str -
Change the value of the kernel parameter
fwha_group_of_bonds_strto add the Bond interface to the existing Group of Bonds on-the-fly:fw ctl set str fwha_group_of_bonds_str '<Name for Group of Bonds>:<List of all Bonds in this Group separated by comma>'Example:
fw ctl set str fwha_group_of_bonds_str 'GoB0:bond0,bond1;GoB1:bond2,bond3,bond4'
Notes:
-
The apostrophe characters are mandatory part of the syntax.
-
Spaces are not allowed in the value of the kernel parameter
fwha_group_of_bonds_str.
-
-
Make sure the Cluster Member accepted the new configuration:
fw ctl get str fwha_group_of_bonds_str -
In SmartConsole, install the Access Control Policy on the cluster object.
Removing a Bond interface from the existing Group of Bonds
This procedure lets you remove a bond interface from an existing Group of Bonds.
|
|
Important - In a Cluster, you must configure all the Cluster Members in the same way. |
-
Connect to the command line on the Cluster Member.
-
Log in to the Expert mode.
-
In VSX Cluster, switch to the context of the applicable Virtual System:
vsenv <VSID> -
Modify the current
$FWDIR/boot/modules/fwkern.conffile:-
Backup the current file:
cp -v $FWDIR/boot/modules/fwkern.conf{,_BKP} -
Edit the current file:
vi $FWDIR/boot/modules/fwkern.conf -
Edit the value of the kernel parameter
fwha_group_of_bonds_strto remove the Bond interface from the existing Group of Bonds.Example:
fwha_group_of_bonds_str=GoB0:bond0,bond1;GoB1:bond2,bond3 -
Save the changes in the file and exit the editor.
-
-
Get the current value of the kernel parameter
fwha_group_of_bonds_strand copy it:fw ctl get str fwha_group_of_bonds_str -
Reset the current value of the kernel parameter
fwha_group_of_bonds_str:fw ctl set str fwha_group_of_bonds_str '' -
Make sure the Cluster Member reset the value of the kernel parameter
fwha_group_of_bonds_str:fw ctl get str fwha_group_of_bonds_str -
Change the value of the kernel parameter
fwha_group_of_bonds_strto remove the Bond interface from the existing Group of Bonds on-the-fly:fw ctl set str fwha_group_of_bonds_str '<Name for Group of Bonds>:<List of all Bonds in this Group separated by comma>'Example:
fw ctl set str fwha_group_of_bonds_str 'GoB0:bond0,bond1;GoB1:bond2,bond3
Notes:
-
The apostrophe characters are mandatory part of the syntax.
-
Spaces are not allowed in the value of the kernel parameter
fwha_group_of_bonds_str.
-
-
Make sure the Cluster Member accepted the new configuration:
fw ctl get str fwha_group_of_bonds_str -
In SmartConsole, install the Access Control Policy on the cluster object.
Deleting a Group of Bonds
This procedure lets you delete an existing Group of Bonds.
|
|
Important - In a Cluster, you must configure all the Cluster Members in the same way. |
-
Connect to the command line on the Cluster Member.
-
Log in to the Expert mode.
-
In VSX Cluster, switch to the context of the applicable Virtual System:
vsenv <VSID> -
Modify the current
$FWDIR/boot/modules/fwkern.conffile:-
Backup the current file:
cp -v $FWDIR/boot/modules/fwkern.conf{,_BKP} -
Edit the current file:
vi $FWDIR/boot/modules/fwkern.conf -
Delete these two lines in the file:
fwha_group_of_bonds_str=<Name for Group of Bonds>:<List of all Bonds in this Group separated by comma>fwha_arp_probe_method=1 -
Save the changes in the file and exit the editor.
-
-
Reset the current value of the kernel parameter
fwha_group_of_bonds_str:fw ctl set str fwha_group_of_bonds_str '' -
Make sure the Cluster Member reset the value of the kernel parameter
fwha_group_of_bonds_str:fw ctl get str fwha_group_of_bonds_str -
In SmartConsole, install the Access Control Policy on the cluster object.
Monitoring
To see the configured Groups of Bonds, run the "cphaprob show_bond_groups" command. See Viewing Bond Interfaces.
Logs
Cluster Members generate some applicable logs.
-
User Space logs:
-
In non-VSX Cluster:
In the
/var/log/messagesfiles.Output of the
dmesgcommand. -
In VSX Cluster:
In the
$FWDIR/log/fwk.elgfile in the context of the applicable Virtual System.
-
-
Kernel Space logs:
-
In the kernel module
fw, enable the debug flagserrorandioctl -
Kernel module
cluster, enable the debug flagif
See the R80.40 Quantum Security Gateway Guide - Chapter Kernel Debug on Security Gateway.
The kernel debug shows:
-
A physical subordinate interface goes down/up.
-
A Bond interface goes down/up (regardless of a change in the Cluster Member's state).
-
A Group of Bonds goes down/up.

Note - These logs are generated only once per event.
-
Limitations
Specific limitations apply to a Group of Bonds.
-
The maximal length on the text string "
<Name for Group of Bonds>" is 16 characters. -
The maximal length on this text string is 1024 characters:
<Name for Group of Bonds>:<List of all Bonds in this Group separated by comma> -
You can configure the maximum of five Groups of Bonds on a Cluster Member or Virtual System.
-
You can configure the maximum of five Bond interfaces in each Groups of Bonds.
-
Group of Bonds feature does support Virtual Switches and Virtual Routers. Meaning, do not configure Groups of Bonds in the context of these Virtual Devices.
-
Group of Bonds feature supports only Bond interfaces that belong to the same Virtual System.
You cannot configure bonds that belong to different Virtual Systems into the same Group of Bonds.
You must perform all configuration in the context of the applicable Virtual System.
-
Group of Bonds feature does support Sync interfaces (an interface on a Cluster Member, whose Network Type was set as
SyncorCluster+Syncin SmartConsole in cluster object). -
Group of Bonds feature does support Bridge interfaces.
-
If a Bond interface goes down on one Cluster Member, the "
cphaprob show_bond_groups" command (see Viewing Bond Interfaces) on the peer Cluster Members also shows the same Bond interface as DOWN.This is because the peer Cluster Members stop receiving the CCP packets on that Bond interface and cannot probe the local network to determine that their Bond interface is really working.
-
After you add a Bond interface to the existing Group of Bonds, you must install the Access Control Policy on the cluster object.
-
After you remove a Bond interface from the existing Group of Bonds, you must install the Access Control Policy on the cluster object.