Configuring a Check Point Full Disk Encryption Policy
You can use the default Full Disk Encryption![]() A component on Endpoint Security Windows clients. This component combines Pre-boot protection, boot authentication, and strong encryption to make sure that only authorized users are given access to information stored on desktops and laptops. Acronym: FDE. rule
A component on Endpoint Security Windows clients. This component combines Pre-boot protection, boot authentication, and strong encryption to make sure that only authorized users are given access to information stored on desktops and laptops. Acronym: FDE. rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. Default Full Disk Encryption settings for the entire organization. Edit the actions of the rule to your requirements. and install the policy.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. Default Full Disk Encryption settings for the entire organization. Edit the actions of the rule to your requirements. and install the policy.
Alternatively, use the following procedure to create a new Check Point Full Disk Encryption policy rule and configure actions for a specific organizational unit. After you install the Full Disk Encryption policy, make sure the policy is installed on the client.
-
Open SmartEndpoint
 A Check Point GUI application which connects to the Endpoint Security Management Server, to manage your Endpoint Security environment - to deploy, monitor and configure Endpoint Security clients and policies. and go to the Policy tab.
A Check Point GUI application which connects to the Endpoint Security Management Server, to manage your Endpoint Security environment - to deploy, monitor and configure Endpoint Security clients and policies. and go to the Policy tab. -
In the Policy toolbar, click the Create a Rule button
 .
.The Create Rule Wizard opens.
-
Select Full Disk Encryption
- Click Next.
-
In the Select Entities page, select the computers for which you want to configure Check Point Full Disk Encryption.
-
Click Next.
-
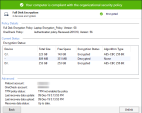
In the Change rule action settings page, select Encryption Engine: Use Check Point Full Disk Encryption .
-
Optionally, make changes to the default action settings.
-
Click Next.
-
In the Enter rule name and comment page, fill in the details.
-
Click Finish.
-
In the main toolbar, click Save rule, and Install the Policy.