Endpoint Security Architecture
An Endpoint Security environment includes the SmartEndpoint![]() A Check Point GUI application which connects to the Endpoint Security Management Server, to manage your Endpoint Security environment - to deploy, monitor and configure Endpoint Security clients and policies. console, Endpoint Security Management Server
A Check Point GUI application which connects to the Endpoint Security Management Server, to manage your Endpoint Security environment - to deploy, monitor and configure Endpoint Security clients and policies. console, Endpoint Security Management Server![]() A Security Management Server that manages your Endpoint Security environment. Includes the Endpoint Security policy management and databases. It communicates with endpoint clients to update their components, policies, and protection data., and Endpoint Security clients. It is integrated with the Check Point Security Management and SmartConsole
A Security Management Server that manages your Endpoint Security environment. Includes the Endpoint Security policy management and databases. It communicates with endpoint clients to update their components, policies, and protection data., and Endpoint Security clients. It is integrated with the Check Point Security Management and SmartConsole![]() Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on..
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on..
Endpoint Security Management Server
|
|
Item |
Description |
||
|---|---|---|---|---|
|
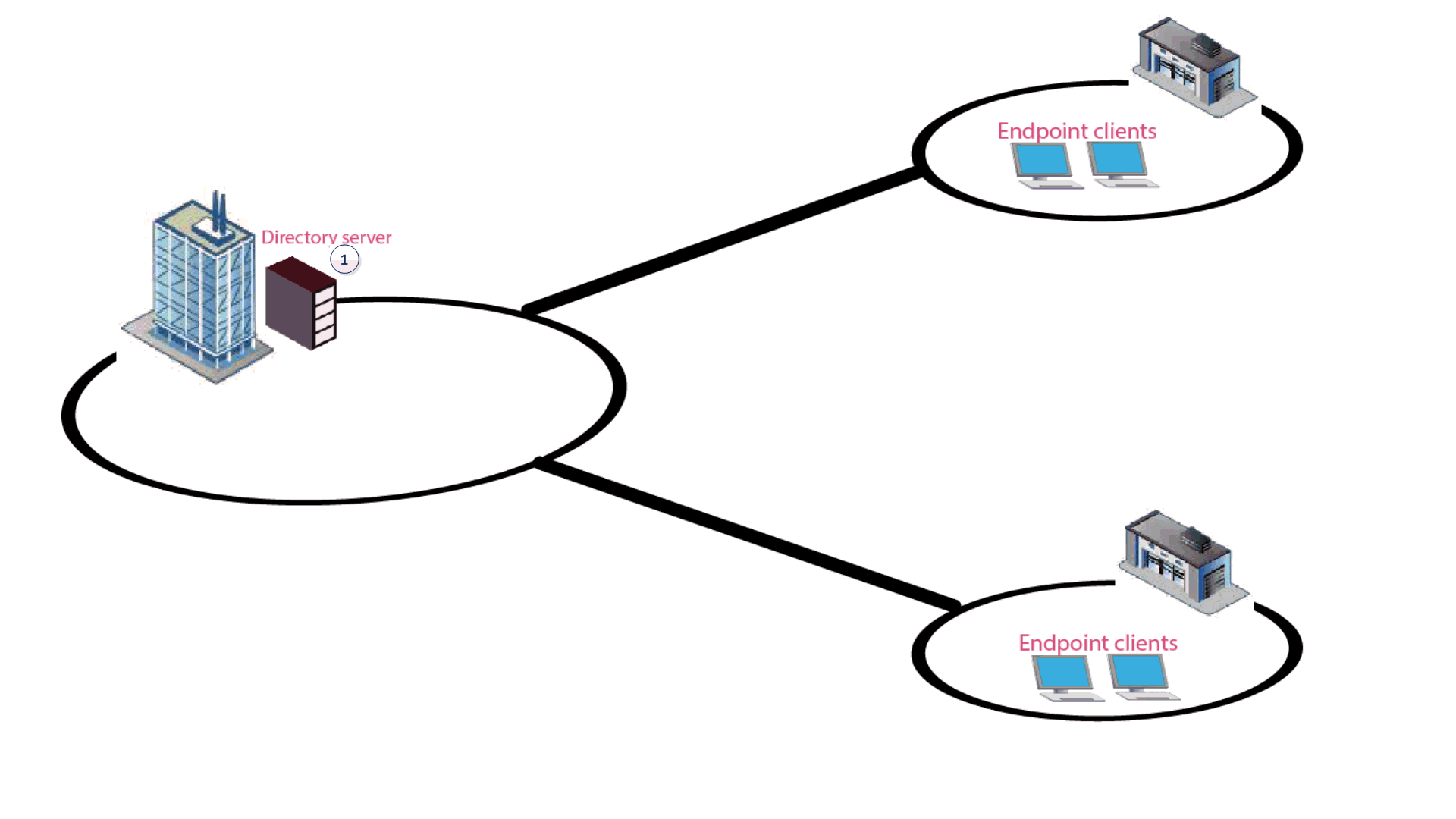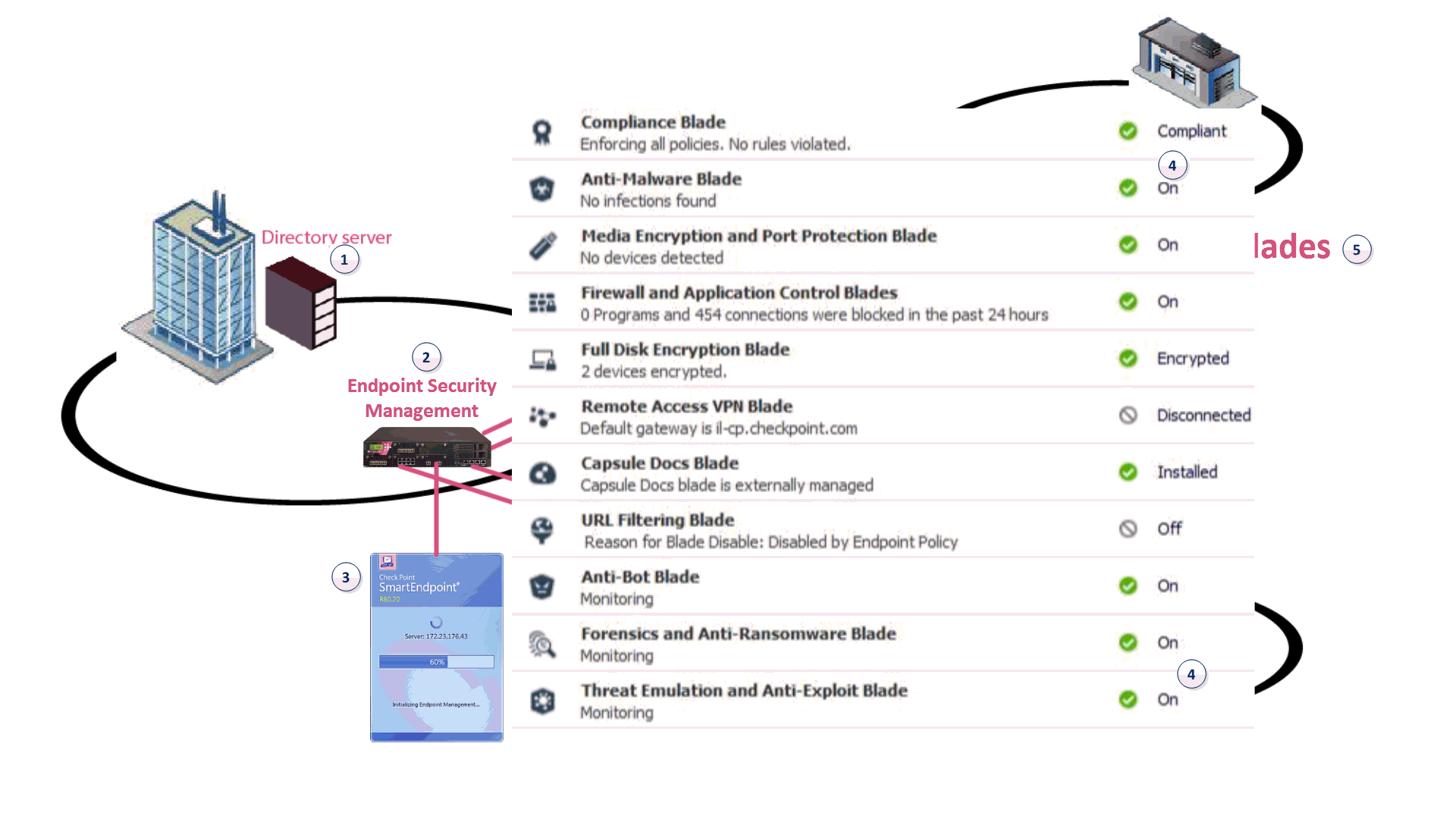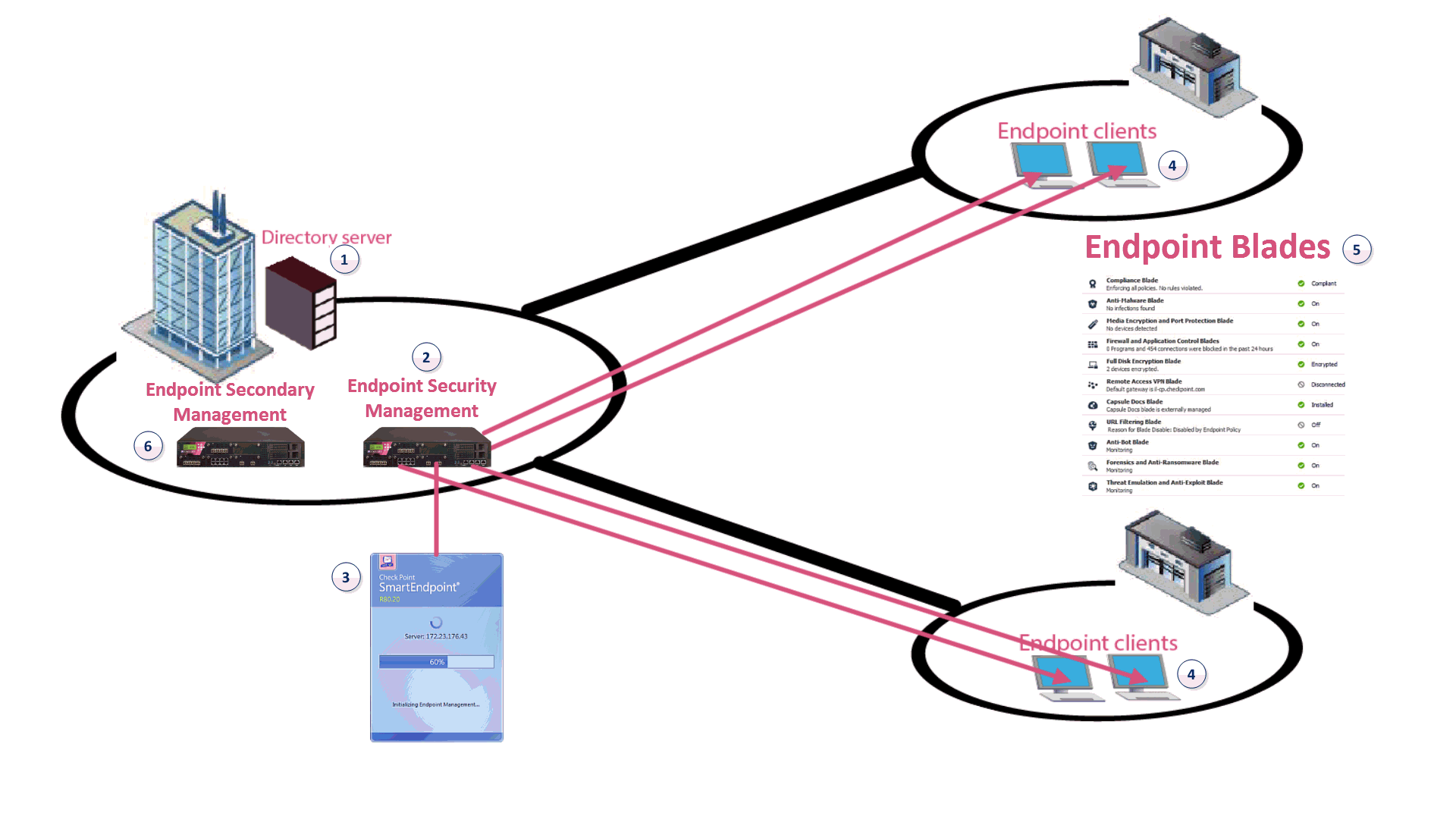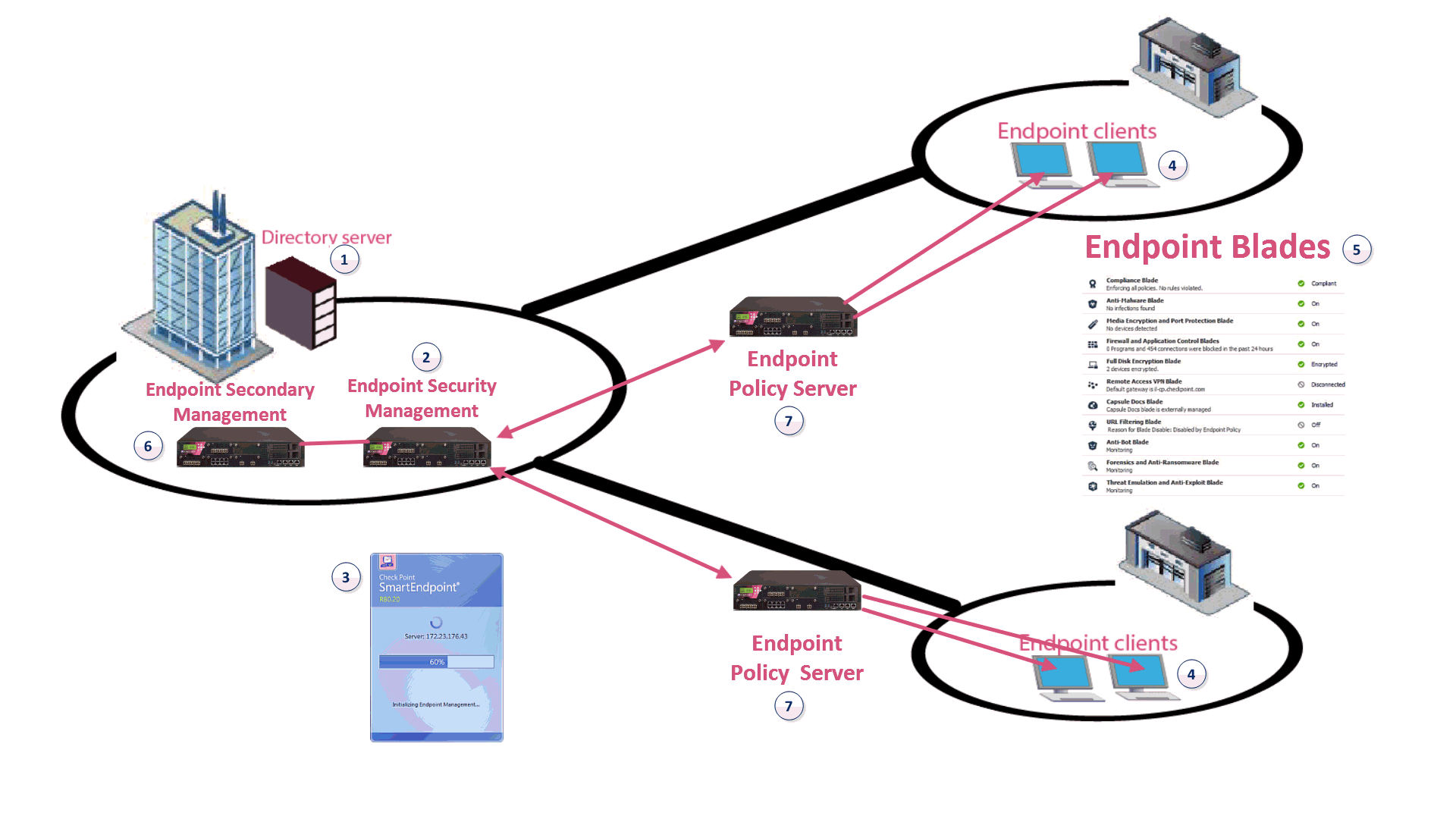
1 |
Active Directory Server |
The repository of the user information of the organization. (Not part of the Endpoint Security Management Server |
||
|
2 |
Endpoint Security Management Server |
Includes the Endpoint Security policy management and databases. It communicates with endpoint clients to update their components, policies, and protection data. The Endpoint Security Database holds policies that enforce security on endpoint clients, user and computer objects, licensing, and Endpoint monitoring data. Also contains the Directory Scanner, that gets the structure and contents of the Active Directory Server for directory-based policy assignment.
|
||
|
3 |
SmartEndpoint |
A Check Point SmartConsole application to deploy, monitor and configure Endpoint Security clients and policies. Install on the Endpoint Security Management Server or on a Windows computer that supports the client installation. |
Endpoint Security Clients
|
|
Item |
Description |
|---|---|---|
|
4 |
Endpoint Security Clients |
Application installed on end-user computers to monitor security status and enforce security policies |
|
5 |
Endpoint Security components |
The components deployed on the endpoint client. You can install any or all of these components from the Endpoint Security Management Server. |
For Endpoint Security Server and Endpoint Security Client![]() Application installed on end-user computers to monitor security status and enforce security policies. requirements, see the R80.40 Release Notes.
Application installed on end-user computers to monitor security status and enforce security policies. requirements, see the R80.40 Release Notes.
Optional Endpoint Security Elements
To make sure that your Endpoint Security system runs efficiently and without unnecessary down time, you can also include these optional elements in your system architecture:

