Defining Endpoint Security Policies
To manage the Security Policies![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. for Endpoint Security, use the Policy tab of the SmartEndpoint
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. for Endpoint Security, use the Policy tab of the SmartEndpoint![]() A Check Point GUI application which connects to the Endpoint Security Management Server, to manage your Endpoint Security environment - to deploy, monitor and configure Endpoint Security clients and policies. console.
A Check Point GUI application which connects to the Endpoint Security Management Server, to manage your Endpoint Security environment - to deploy, monitor and configure Endpoint Security clients and policies. console.
![]()
The Policy tab contains the Policy Management Toolbar and the Policy Rule Base.
The Policy Rule Base contains a policy for each of the Endpoint Security components (formerly known as a Blades). These policies enforce protections on endpoint computers.
The policy for each component is made up of rules. This shows some example of rules in the Policy tab:
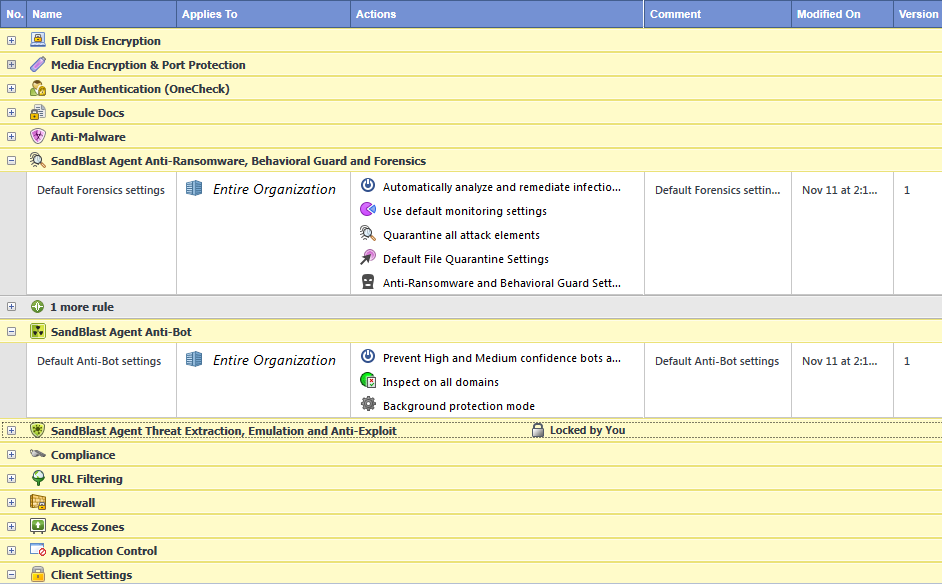
Each rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. applies to a specific component, and to a specific part of the organization. Each rule has a set of actions.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. applies to a specific component, and to a specific part of the organization. Each rule has a set of actions.
The policy for each component has a default rule that applies to the entire organization. You can change the actions of a default rule, but you cannot make the default rule apply to a specific part of the organization. You cannot delete the default rule.
You can create new rules that apply to specific parts of the organization.
