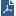
'g_fw sam_policy del' and 'g_fw6 sam_policy del'
Description
The 'g_fw sam_policy del' and 'g_fw6 sam_policy del' commands let you delete one configured Rate Limiting rule at a time.
Notes:
- Configuration is supported only from the Command Line.
- You must run these commands on a single Security Group member in the Expert mode:
- For IPv4:
g_fw sam_policy del ... - For IPv6:
g_fw6 sam_policy del ...
- You can run these commands interchangeably: '
g_fw sam_policy del add' and 'g_fw samp del'. - Security Group members store the SAM Policy rules in the
$FWDIR/database/sam_policy.db file. - Security Group members store the SAM Policy management settings in the
$FWDIR/database/sam_policy.mng file.
Important:
- R80.30SP does not support the Suspicious Activity Monitoring (SAM) rules and the '
fw sam' command (see 02641733 in sk113255 and in sk148074). - The Rate Limit is applied to each Security Group member and not globally.
- Configuration you make with these commands, survives reboot.
- The SAM Policy rules consume some CPU resources on Security Group members. We recommend to set an expiration that gives you time to investigate, but does not affect performance. The best practice is to keep only the SAM Policy rules that you need. If you confirm that an activity is risky, edit the Security Policy, educate users, or otherwise handle the risk.
- Support for VSX mode is planned (see sk155832).
Syntax for IPv4
g_fw [-d] sam_policy del '<Rule UID>'
|
Syntax for IPv6
g_fw6 [-d] sam_policy del '<Rule UID>'
|
Parameters
Parameter
|
Description
|
-d
|
Enables the debug mode for the fw command. By default, writes to the screen.
Note - If you use this parameter, then redirect the output to a file, or use the script command to save the entire CLI session.
|
'<Rule UID>'
|
Specifies the UID of the rule you wish to delete.
Important:
|
Procedure
Step
|
Description
|
1
|
List all the existing rules in the Suspicious Activity Monitoring policy database:
For IPv4: g_fw sam_policy get
For IPv6: g_fw6 sam_policy get
The rules show in this format:
operation=add uid=<Value1,Value2,Value3,Value4> target=... timeout=... action=... log= ... name= ... comment=... originator= ... src_ip_addr=... req_tpe=...
Example for IPv4:
operation=add uid=<5ac3965f,00000000,3403a8c0,0000264a> target=all timeout=300 action=notify log=log name=Test\ Rule comment=Notify\ about\ traffic\ from\ 1.1.1.1 originator=John\ Doe src_ip_addr=1.1.1.1 req_tpe=ip
|
2
|
Delete a rule from the list by its UID.
For IPv4: g_fw [-d] sam_policy del '<Rule UID>'
For IPv6: g_fw6 [-d] sam_policy del '<Rule UID>'
Example for IPv4:
g_fw samp del '<5ac3965f,00000000,3403a8c0,0000264a>'
|
3
|
Enter this flush-only add rule:
For IPv4: g_fw samp add -t 2 quota flush true
For IPv6: g_fw6 samp add -t 2 quota flush true
Explanation:
The g_fw samp del and g_fw6 samp del commands only remove a rule from the persistent database. The Security Group member continues to enforce the deleted rule until the next time you compiled and load a policy. To force the rule deletion immediately, you must enter a flush-only add rule right after the g_fw samp del and g_fw6 samp del command. This flush-only add rule immediately deletes the rule you specified in the previous step, and times out in 2 seconds. It is a good practice to specify a short timeout period for the flush-only rules. This prevents accumulation of rules that are obsolete in the database.
|