
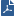

Syslog (System Logging Protocol) is a standard protocol used to send system log or event messages to a specific server, the syslog server. The syslog protocol is enabled on most network devices such as routers and switches.
Use Case
Syslog is used by many log analysis tools included in the cloud. If you want to use these tools, make sure Check Point logs are sent to from the gateway to the syslog server in syslog format.
By default, gateway logs are sent to the Security Management Server. But you can configure gateways to send logs directly to syslog servers.
These syslog protocols are supported: RFC 3164 (old) and RFC 5424 (new)
These features are not supported: IPv6 logs and Software Blade logs.
To create a syslog server:
Note - Syslog is not an encrypted protocol. Make sure the Security Gateway and the Log Proxy are located close to each other and that they communicate over a secure network.
You can configure a gateway to send logs to multiple syslog servers. The syslog servers must be the same type: BSD Protocol or Syslog Protocol.
To send the logs of a gateway to syslog servers:
Note - You cannot configure a Syslog server as a backup server.
The fwsyslog_enable kernel parameter enables or disables the Syslog in Kernel feature:
0 = Disabled (default)
1 = Enabled
You can enable or disable Syslog in Kernel temporarily (until the system reboots) or permanently (until manually disabled).
To temporarily enable Syslog in Kernel on a Security Gateway:
# fw ctl set int fwsyslog_enable 1To permanently enable Syslog in Kernel on a Security Gateway:
echo fwsyslog_enable=1 >> $FWDIR/modules/fwkern.conf
To disable Syslog in Kernel temporarily:
Run: # fw ctl set int fwsyslog_enable 0
To disable Syslog in Kernel permanently:
$FWDIR/modules/fwkern.conf in a text editor and do one of these actions:fwsyslog_enable=0or
fwsyslog_enable line.To see the Syslog in Kernel status:
[Expert@host:0]# fw ctl get int fwsyslog_enable
You can see the count of logs sent to syslog from the kernel. Log counters start when you install the policy.
To see log count for an instance:
[Expert@host:0]# fw -i <instance_number> ctl get size fwsyslog_nlogs_counter
Sample output:
fwsyslog_nlogs_counter = 21
To see log count for all instances:
# fw ctl zdebug# fw ctl set size fwsyslog_print_counter 1Sample output:
;[cpu_2];[fw4_0];Number of logs sent from instance 0 is 43;
;[cpu_2];[fw4_0];Number of logs sent from instance 1 is 39;
;[cpu_2];[fw4_0];Number of logs sent from instance 2 is 50;
;[cpu_2];[fw4_0];Total fwsyslog_nlogs_counter = 132;
To see the Syslog in Kernel status:
[Expert@host:0]# fw ctl get int fwsyslog_enable
You can see the count of logs sent to syslog from the kernel. Log counters start when you install the policy.
To see log count for an instance:
[Expert@host:0]# fw -i <instance_number> ctl get size fwsyslog_nlogs_counter
Sample output:
fwsyslog_nlogs_counter = 21
To see log count for all instances:
# fw ctl zdebug# fw ctl set size fwsyslog_print_counter 1Sample output:
;[cpu_2];[fw4_0];Number of logs sent from instance 0 is 43;
;[cpu_2];[fw4_0];Number of logs sent from instance 1 is 39;
;[cpu_2];[fw4_0];Number of logs sent from instance 2 is 50;
;[cpu_2];[fw4_0];Total fwsyslog_nlogs_counter = 132;
For more on syslog, see: Manual Syslog Parsing