
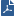

NetFlow is an industry standard for traffic monitoring. It is a network protocol developed by Cisco for collecting network traffic patterns and volume. It lets one host (the Exporter) send information about network flows to another host (the Collector). A network flow is a unidirectional stream of packets that share a set of characteristics.
You can configure Security Gateways and Cluster Members that run on Gaia Operating System as an Exporter of NetFlow records for all the traffic they inspect.
Note - The state of the SecureXL on a Security Gateway is irrelevant for NetFlow export.
The Collector is supplied by a different vendor, and is configured separately.
NetFlow Export configuration is a list of collectors, to which the service sends records:
You can configure up to three collectors. NetFlow records go to all configured collectors. If you configure three collectors, each record is sent three times.
Regardless of which NetFlow export format you choose, Gaia operating system exports values for the these fields:
Notes:
For more information, see sk102041: NetFlow support by Gaia OS.
Workflow:
To configure NetFlow export in Gaia Portal:
Important - In a cluster, you must configure all members in the same way.
Parameter |
Description |
|---|---|
IP address |
The IPv4 address, to which NetFlow packets are sent. This is mandatory. |
UDP port Number |
The UDP port number, on which the collector is listening. This is mandatory. There is no default or standard port number for NetFlow. |
Export format |
The NetFlow protocol version to send:
Each protocol version has a different packet format. The default is Netflow_V9. |
Source IP address |
Optional: The IPv4 address of the NetFlow packets source. This must be an IPv4 address of the local host. The default (which is recommended) is an IPv4 address from the network interface, on which the NetFlow traffic is going out. |
To configure the explicit Access Control rule in SmartConsole:
Important - In the Track column, you must select Log and Accounting.
Source |
Destination |
VPN |
Services & Applications |
Content |
Action |
Track |
|---|---|---|---|---|---|---|
Source |
Destination |
|
Applicable |
|
|
|
Workflow:
To configure NetFlow export in Gaia Clish:
Important - In a cluster, you must configure all members in the same way. After you add, configure, or delete features, run the save config command to save the settings permanently.
add netflow collector ip <IPv4 Address of Collector> port <Destination Port on Collector> [srcaddr <Source IPv4 Address> export-format {Netflow_V5 | Netflow_V9 | IPFIX}] enable |
set netflow collector for-ip <IPv4 Address of Collector> ip <IPv4 Address of Collector> port <Destination Port on Collector> srcaddr <Source IPv4 Address> export-format {Netflow_V5 | Netflow_V9 | IPFIX} export-format {Netflow_V5 | Netflow_V9 | IPFIX} enable disable |
show netflow collector |
show netflow collector<SPACE><TAB> |
show netflow all |
delete netflow collector for-ip <IPv4 Address of Collector> [for-port <Destination Port on Collector>] |
Parameters
Parameter |
Description |
|---|---|
|
Specifies the IPv4 address of the NetFlow Collector, to which NetFlow packets are sent. This is mandatory. |
|
Specifies the UDP port number on the NetFlow Collector, on which the collector is listening. This is mandatory. There is no default or standard port number for NetFlow. |
|
Optional: Specifies the IPv4 address of the NetFlow packets source. This must be an IPv4 address that belongs to one of the local interfaces of the local host. The default (which is recommended) is an IPv4 address that belongs to the network interface that connects to the NetFlow Collector. |
|
The NetFlow protocol version to send:
Each NetFlow protocol version has a different packet format. The default is NetFlow v9. |
|
These parameters specify the configured NetFlow Collector. If you only have one collector configured, you do not need these parameters. If you have two or three collectors with different IP addresses, use If you have two or three collectors with the same IP address and different UDP ports, you must use |
To configure the explicit Access Control rule in SmartConsole:
Important - In the Track column, you must select Log and Accounting.
Source |
Destination |
VPN |
Services & Applications |
Content |
Action |
Track |
|---|---|---|---|---|---|---|
Source |
Destination |
|
Applicable |
|
|
|