
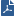

Define what happens to the components of an attack that is detected by Forensics. When files are quarantined, they are deleted and put in a secure location from which they can be restored, if necessary.
The automatic options are:
You can manually edit the treatment for each category of file: Malicious, suspicious, or unknown. For each category, you can select:
Trusted Files are those defined as trusted by the Check Point Reputation Service. The remediation options for Trusted Files are: