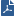
Overview of Full Disk Encryption
Full Disk Encryption includes two main components:
- - All volumes of the hard drive and hidden volumes are automatically fully encrypted. This includes system files, temporary files, and even deleted files. There is no user downtime because encryption occurs in the background without noticeable performance loss. The encrypted disk is inaccessible to all unauthorized people.
- - Users must authenticate to their computers in the Pre-boot, before the computer boots. This prevents unauthorized access to the operating system using authentication bypass tools at the operating system level or alternative boot media to bypass boot protection.
Configure the settings for Full Disk Encryption in SmartEndpoint in thetab > Rules.