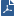
Profile - Mail Settings
What can I do here?
Use this window to create a policy for malicious email on MTA gateways.

|
Getting Here - Security Policies > Threat Prevention > Policy > Threat Tools > Profiles > Profile > Mail > General
|
General
- - When this option and the Threat Emulation blade are enabled, the Threat Emulation blade scans SMTP traffic.
- - When this option and the Anti-Virus blade are enabled, the Anti-Virus blade scans SMTP traffic.
- - When this option and the Threat Extraction blade are enabled, the Threat Extraction blade scans SMTP traffic.
- - Shows the current status of the email traffic which passed through the MTA in the selected time frame.
In this section you can decide whether to block or allow an email which was found malicious.
If you allow the email, you can select any or all of these options:
- - This option is selected by default. You can replace a link or an attachment found malicious with a neutralized version of the links and attachments. The neutralized email version is sent to the recipient with a customizable template. Click to edit the template:
- - Replaced by a neutralized txt file. You can customize the message which the user receives. Click to add more file-related information to your message (for example: file name or MD5 hash).
- - If the scanning of the attachment fails and fail mode is set to fail-close, the attachment is replaced with a txt attachment. If fail mode is set to fail-open, the original attachment is allowed. Click to add more file-related information to your message (for example: file name or MD5 hash).
- - Replaced by a neutralized link. Click to add more link-related information to your message, for example, neutralized url.
- - Tag the email found malicious with an X-Header. The X-Header format is: "X-Check Point-verdict: <verdict>; confidence: <confidence>". For example: "X-Check Point-verdict: malicious; confidence: high". With this option, you can configure the MTA Next Hop to quarantine all emails with a specific X-Header.
- - Adds a prefix to the subject of an email found malicious. For example: you can add a warning message that the email is malicious. Click to edit the prefix.
- - This option adds a section at the beginning of the email body, based on a customizable template, with an optional placeholder for the verdicts of the links and attachments found malicious or failed to be scanned. The links are given in their neutralized versions, and attachments are only given by file names. Click to edit the template.
- This option is available both if you allow or block the malicious email. With this option, the original email (with the malicious attachments and links) is attached to a new email, which contains: the verdict list with the neutralized links and attachment file names, and the SMTP envelope information. You can configure the email content on the gateway. You can use this option for research purposes. For example: The Incident Response Team needs to inquire the emails received in the organization for improved security and protection.
MIME Nesting
This is an optional configuration. In this section, you can configure the maximum number of MIME nesting levels to be scanned (A nesting level is an email within an email). These settings are the same for Anti-Virus, Threat Emulation and Threat Extraction.
- - Set the maximum number of levels in the email which the engine scans.
- - If there are more MIME nested levels than the configured amount, select to or the email.