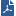
Scan All Files on Access
By default, all file are scanned when they are opened or used.
You can configureas exceptions. When a trusted process accesses a file, the file is not scanned. Exclude a process only if you fully trust it and are sure it is not malware.
You can also select or clear these options:
- - Use behavior detection methods to protect computers from new threats whose information has not been added to the databases yet. It does not monitor trusted processes.
- - Use cloud technologies to improve precision of scanning and monitoring functions. If you enable or disable this setting, it takes affect after the client computer restarts.
- - Change the maximum time to get a response from Reputation Services (in milliseconds).
Note - If you decrease this value, it can improve the performance of the Anti-Malware blade but reduces security, as clients might not get a reputation status that shows an item to be zero-day malware.
- - Prevents access to suspicious sites and execution of malicious scripts. Scans files, and packed executables transferred over HTTP, and alerts users if malicious content is found.
- - Enable or disable scans of email messages when they are passed as files across the file system.
To configure trusted processes:
- In the of theAction, click .
- In the window, enter the fully qualified path or an environment variable for the trusted executable file. For example:
C:\Program Files\MyTrustedDirectory\MyTrustedProgram.exe%programdata%\MyTrustedProgram.exe
- Click .
The trusted program shows in the list.