
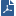

These preconfigured SIP services are available for gateways of version R80.xx or higher.
Services |
Port |
Protocol Type |
Description |
|---|---|---|---|
|
UDP 5060 |
|
This service enforces signal routing. Use a VoIP Domain in the source or destination of a rule, together with this service. When you use this service, registration messages are tracked and a database is maintained that includes the details of the IP phones and the users. If an incoming call is made to a Hide NATed address, the Security Gateway confirms the user exists in the SIP registration database. This can prevent DoS attacks. |
|
TCP 5060 |
|
Used for SIP over TCP. |
|
Not set |
Not set |
This service allows a SIP connection to be opened on a dynamic port and not on the SIP well-known port. |
|
TCP 5061 |
None |
Allows SIP over TLS to pass without inspection. It requires that you open the media ports manually. |
|
TCP 5061 |
|
SIP over non-encrypted TLS and authenticated only. NAT is not supported for connections of this type. |
These legacy SIP services are used for gateways of version R75.40 and below, if not enforcing handover. Do not use these services for R.80.xx (or higher).
Services |
Purpose |
|---|---|
|
Use sip_any for VoIP equipment that uses SIP UDP. Do not place a VoIP Domain in the Source or Destination of a rule. Instead, use * Any or a Network Object, together with one of these services.
Note - If a VoIP Domain is used with this service, the packet is dropped. Important - Do not use this service in the same rule with the sip service because they contradict each other. |
|
Use sip-tcp_any for VoIP equipment that uses SIP TCP. Use this service if you do not enforce signal routing. In that case, do not place a VoIP Domain in the Source or Destination of a rule. Instead, use * Any or a Network Object together with the sip_any-tcp service. Note - If a VoIP Domain is used with this service, the packet is dropped. Important - Do not use this service in the same rule with the sip-tcp service because they contradict each other. |
Legacy Solution for SIP TLS Support
If you are not able to use the sip_tls_authentication service, add these two rules instead:
AND
This can happen if connections are encrypted by TLS, or NAT must be done on the connections.
Important - SIP signaling and data is not inspected if you open all high UDP ports. The connection is not-secured.
To configure support for SIP TLS in environments where a secure solution is not available:
The rule below shows that the phones send data directly to each other, and not through the proxy.
No |
Name |
Source |
Destination |
VPN |
Services & Applications |
Action |
Track |
|---|---|---|---|---|---|---|---|
1 |
Transmit through proxy |
SIP Proxy SIP Phones |
SIP Phones SIP Proxy |
* Any |
TCP: sip_tls_not_inspected |
Accept |
Log |
2 |
Transmit directly |
SIP Phones |
SIP Phones |
* Any |
UDP: udp-high-ports |
Accept |
Log |