

Description
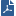
Shows the current Accelerated SYN Defender configuration.
Syntax for IPv4
|
Syntax for IPv6
|
Example
[Expert@MyGW:0]# fwaccel synatk config enabled 0 enforce 1 global_high_threshold 10000 periodic_updates 1 cookie_resolution_shift 6 min_frag_sz 80 high_threshold 5000 low_threshold 1000 score_alpha 100 monitor_log_interval (msec) 60000 grace_timeout (msec) 30000 min_time_in_active (msec) 60000 [Expert@MyGW:0]# |
Description of Configuration Parameters
Parameter |
Description |
|---|---|
|
Shows if the Accelerated SYN Defender is enabled or disabled.
|
|
When the Accelerated SYN Defender is enabled, shows it enforces the protection. Valid values:
|
|
Global high attack threshold number. See the ' |
|
For internal Check Point use only.
|
|
For internal Check Point use only.
|
|
During the TCP SYN Flood attack, the Accelerated SYN Defender prevents TCP fragments smaller than this minimal size value.
|
|
High attack threshold number. See the ' |
|
Low attack threshold number. See the ' |
|
For internal Check Point use only.
|
|
Interval, in milliseconds, between successive warning logs in the Monitor (Detect only) mode.
|
|
Maximal time, in milliseconds, to stay in the Grace state (which is a transitional state between Ready and Active ). In the Grace state, the Accelerated SYN Defender stops challenging Clients for TCP SYN Cookie, but continues to validate TCP SYN Cookies it receives from Clients.
|
|
Minimal time, in milliseconds, to stay in the Active mode. In the Active mode, the Accelerated SYN Defender is actively challenging TPC SYN packets with SYN Cookies.
|