
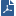

These tables show how identity sources are different in terms of usage and deployment considerations. Based on these considerations, you can configure Identity Awareness to use one or more identity of these identity sources.
Browser-Based Authentication - Captive Portal
Unidentified users log in with a user name and password in a Captive Portal. After authentication, the user clicks a link to go to the destination address.
Recommended Usage |
Deployment Considerations |
|
|
Browser-Based Authentication - Transparent Kerberos Authentication
The Transparent Kerberos Authentication Single-Sign On (SSO) solution transparently authenticates users already logged into the AD. This means that when a user authenticates to the domain, user gets access to all authorized network resources and does not have to enter credentials again. If Transparent Kerberos Authentication fails, the user is redirected to the Captive Portal for manual authentication.
Note -The Identity Agent download link and the Automatic Logout option are ignored when Transparent Kerberos Authentication SSO is successful. This is so, because the user does not see the Captive Portal.
Recommended Usage |
Deployment Considerations |
|
|
AD Query
Gets identity data seamlessly from Active Directory (AD).
Recommended Usage |
Deployment Considerations |
|---|---|
|
|
Identity Agent
A lightweight Identity Agent authenticates users securely with Single Sign-On (SSO).
Recommended Usage |
Deployment Considerations |
|
Terminal Servers Identity Agent
Identifies multiple users, who connect from one IP address. A terminal Server Identity Agent is installed on the application server, which hosts the terminal/Citrix services.
Recommended Usage |
Deployment Considerations |
|
RADIUS Accounting
You can configure an Identity Awareness Gateway to use RADIUS Accounting to get user and computer identities directly from a RADIUS accounting client. Identity Awareness Gateway uses this information to apply access permissions to the connection.
RADIUS Accounting gets identity data from RADIUS Accounting Requests generated by the RADIUS accounting client. Identity Awareness Gateway uses the data from these requests to get user and device group information from the LDAP server. Firewall rules apply these permissions to users, computers and networks.
Recommended Usage |
Deployment Considerations |
|
|
Identity Collector
The Identity Collector is a Windows-based application, which collects identity information and sends it to the Identity Awareness Gateways for identity enforcement.
Recommended Usage |
Deployment Considerations |
|
|
Identity Web API
The Web API is a flexible identity source that you can use for simple integration with 3rd party security and identity products.
Recommended Usage |
Deployment Considerations |
|
|
Remote Access
Users, who get access using IPsec VPN Office Mode can authenticate seamlessly.
Recommended Usage |
Deployment Considerations |
|