
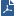

Define the automatic threat analysis settings in the Triggers and Automatic Response Action.
The automatic options are:
You can edit the selections manually to define when these processes occur.
The confidence level is how sure Endpoint Security is that a file is malicious. High confidence means that it is almost certain that a file is malicious. Medium confidence means that it is very likely that a file is malicious.
To granularly edit which type of events trigger a Forensics response:
You can override the settings of the rule for up to five different events.
The Triggers include:
To make triggers and remediation work for events detected by Network Threat Prevention Software Blades, you must configure gateway policy for the Threat Prevention Software Blades: Anti-Bot, Anti-Virus, and Threat Emulation.
Each Software Blade must be enabled and have Protection settings of Prevent or Ask, which include UserCheck.
Best practice is to use the Threat Prevention Recommended Profile (default) that includes all required settings.