
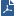

The Endpoint Security policy can include rules for these Software Blades.
Blade |
Rule |
Description |
Client OS |
|---|---|---|---|
Full Disk Encryption |
OneCheck User Settings |
Manages:
|
Windows |
Full Disk Encryption |
Full Disk Encryption |
Combines Pre-boot protection, boot authentication, and strong encryption to make sure that only authorized users are given access to information stored on desktops and laptops. |
Windows |
Media Encryption & Port Protection |
Media Encryption & Port Protection |
Protects data stored on the computers by encrypting removable media devices and allowing tight control over computers' ports (USB, Bluetooth, and so on). |
Windows Mac |
Anti-Malware |
Anti-Malware |
Protects clients from known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. |
Windows |
Firewall |
Access Zones |
Defines the topology of the organizational network, separating it into Trusted and Internet domains. |
Windows |
Firewall |
Firewall |
Blocks or allows network traffic based on attributes of network connections. |
Windows |
Firewall |
Application Control |
Controls network access on a per-application basis, letting you restrict application access by zone and direction. |
Windows |
Compliance |
Compliance |
Ensures that protected computers comply with your organization's requirements and allows you to assign different security levels according to the compliance state of the endpoint computer. For example, non-compliance can result in a remediation message, a warning, or restriction from the network. |
Windows |
Capsule Docs |
|
Provides security classifications and lets organizations protect and share documents safely with various groups - internal and external. |
Windows Mac |
URL Filtering |
URL Filtering |
Lets organizations control access to web sites by category, user or group. |
Windows |
SandBlast Agent Anti-Bot |
SandBlast Agent Anti-Bot |
Detects bot-infected machines and blocks bot C&C communication to prevent bot damage. Provides detailed information about the device affected by the bot activity, about the bot process itself, and other relevant information. |
Windows |
SandBlast Agent Forensics and Anti-Ransomware |
SandBlast Agent Forensics and Anti-Ransomware |
Analyzes incidents reported by other blades. Monitors files and the registry for suspicious processes and network activity. Prevents ransomware attacks. |
Windows |
SandBlast Agent Threat Extraction and Threat Emulation |
SandBlast Agent Threat Extraction and Threat Emulation |
Threat Emulation sends files on the endpoint computer to a sandbox for emulation to detect evasive zero-day attacks. Threat Extraction quickly delivers safe files while the original files are inspected for potential threats. |
Windows |
VPN |
Remote Access VPN |
Remote Access VPN lets users connect remotely to a Check Point Security Gateway using IPSec. |
Windows |
Settings for some Software Blades are defined for computers, while others are defined for users.
For example: