

Description
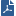
Firewall Monitor is the Check Point traffic capture tool.
In a Security Gateway, traffic passes through different inspection points - Chain Modules in the Inbound direction and then in the Outbound direction.
The FW Monitor tool captures the traffic at each Chain Module in both directions.
You can later analyze the captured traffic with the same FW Monitor tool, or with special tools like Wireshark.
Notes:
fw monitor can run at a time.fw monitor.$FWDIR/tmp/monitorfilter.*).Limitations:
FW Monitor shows TCP [SYN] packets of accelerated connections only at Pre-Inbound (small "i").
FW Monitor can monitor accelerated traffic only in Fast path.
FW Monitor can monitor accelerated traffic in both Fast path and Medium path.
For more information, see sk30583 and How to use FW Monitor.
Syntax for IPv4
fw monitor {-h | -help} |
fw monitor [-d] [-D] [-ci <Number of Inbound Packets>] [-co <Number of Outbound Packets>] [-e <INSPECT Expression> | -f {<INSPECT Filter File> | -}] [-F "<Source IP>,<Source Port>,<Dest IP>,<Dest Port>,<Protocol Number>"] [-i] [-l <Length>] [-m {i,I,o,O,e,E}] [-o <Output File> [-w]] [[-pi <Position>] [-pI <Position>] [-po <Position>] [-pO <Position>] | -p all [-a]] [-T] [-u | -s] [-U] [-v <VSID>] [-x <Offset>[,<Length>] [-w]] |
Syntax for IPv6
fw6 monitor {-h | -help} |
fw6 monitor [-d] [-D] [-ci <Number of Inbound Packets>] [-co <Number of Outbound Packets>] [-e <INSPECT Expression> | -f {<INSPECT Filter File> | -}] [-F "<Source IP>,<Source Port>,<Dest IP>,<Dest Port>,<Protocol Number>"] [-i] [-l <Length>] [-m {i,I,o,O,e,E}] [-o <Output File> [-w]] [[-pi <Position>] [-pI <Position>] [-po <Position>] [-pO <Position>] | -p all [-a]] [-T] [-u | -s] [-U] [-v <VSID>] [-x <Offset>[,<Length>] [-w]] |
Parameters
Parameter |
Description |
|---|---|
|
Shows the built-in usage. |
|
Runs the command in debug mode and shows some information about how the FW Monitor starts and compiles the specified INSPECT filter:
Note - You can specify both parameters to show more information. |
|
Specifies how many packets to capture. The FW Monitor stops the traffic capture if it counted the specified number of packets.
You can use the " |
or
|
Captures only specific packets:
Refer to the For syntax examples, see sk30583. Important - Make sure to enclose the INSPECT filter expression correctly in single quotes (ASCII value 39) or double quotes (ASCII value 34). Note - In R80.20, the FW Monitor filters do not apply to the accelerated traffic. |
|
Specifies the simple capture filter:
Notes:
|
|
Flushes the standard output. Note - This parameter is valid only with the " Use this parameter to make sure FW Monitor immediately writes the captured data for each packet to the standard output. This is especially useful if you want to kill a running FW Monitor process, and want to be sure that FW Monitor writes all the data to the specified file. |
|
Specifies the maximal length of the captured packets. FW Monitor reads only the specified number of bytes from each packet. Notes:
|
|
Specifies the capture mask (inspection point) in relation to Chain Modules, in which the FW Monitor captures the traffic. These are the inspection points, through which each packet passes on a Security Gateway.
|
|
Notes:
(*) The packet direction relates to each specific packet, and not to the connection's direction. (**) The letters "q" and "Q" after the inspection point mean that the QoS policy is applied to the interface. |
|
Example packet flows:
|
|
Specifies the output file, to which FW Monitor writes the captured raw data. Important - If you do not specify the path explicitly, FW Monitor creates this output file in the current working directory. Because this output file can grow very fast to very large size, we always recommend to specify the full path to the largest partition The format of this output file is the same format used by tools like You can later analyze the captured traffic with the same FW Monitor tool, or with special tools like Wireshark. |
or
|
Inserts the FW Monitor Chain Module at the specified position between the kernel Chain Modules. If the FW Monitor writes the captured data to the specified output file (with the parameter " You can insert the FW Monitor Chain Module in these positions only:
|
|
Notes:
Important - For more information about the inspection points, see the applicable table below. |
|
Shows the timestamp for each packet:
Note - Use this parameter if you do not save the output to a file, but print it on the screen. |
or
|
Shows UUID for each packet:
Note - It is only possible to print the UUID, or the SUUID - not both. |
|
Removes the simple capture filters specified with this parameter:
Note - This parameter exists only in R80.20 Jumbo Hotfix Accumulator Take 49 and above (sk137592). |
|
On a VSX Gateway or VSX Cluster Member, captures the packets on the specified Virtual System or Virtual Router. By default, FW Monitor captures the packets on all Virtual Systems and Virtual Routers. Example:
|
|
Captures the entire packet, instead of only the header. Must be used together with one of these parameters:
Note - This parameter exists only in R80.20 Jumbo Hotfix Accumulator Take 49 and above (sk137592). |
|
Specifies the position in each packet, where the FW Monitor starts to capture the data from each packet. Optionally, it is also possible to limit the amount of data the FW Monitor captures.
For example, to skip over the IP header and TCP header, enter |
Inspection points in Security Gateway and in FW Monitor output
Note - The Inbound and Outbound traffic direction relates to each specific packet, and not to the connection.
Name of inspection point |
Relation to FireWall |
Notion of inspection point |
Pre-Inbound |
Before the inbound FireWall VM |
i (for example, |
Post-Inbound |
After the inbound FireWall VM |
I (for example, |
Pre-Inbound VPN |
Inbound before decrypt |
id (for example, |
Post-Inbound VPN |
Inbound after decrypt |
ID (for example, |
Pre-Inbound QoS |
Inbound before QoS |
iq (for example, |
Post-Inbound QoS |
Inbound after QoS |
IQ (for example, |
Name of inspection point |
Relation to FireWall |
Notion of inspection point |
Pre-Outbound |
Before the outbound FireWall VM |
o (for example, |
Post-Outbound |
After the outbound FireWall VM |
O (for example, |
Pre-Outbound VPN |
Outbound before encrypt |
e (for example, |
Post-Outbound VPN |
Outbound after encrypt |
E (for example, |
Pre-Outbound QoS |
Outbound before QoS |
oq (for example, |
Post-Outbound QoS |
Outbound after QoS |
OQ (for example, |
Example 1 - Default syntax
[Expert@MyGW:0]# fw monitor monitor: getting filter (from command line) monitor: compiling monitorfilter: Compiled OK. monitor: loading monitor: monitoring (control-C to stop) [vs_0][fw_1] eth0:i[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=31789 TCP: 53901 -> 22 ....A. seq=761113cd ack=f92e2a13 [vs_0][fw_1] eth0:I[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=31789 TCP: 53901 -> 22 ....A. seq=761113cd ack=f92e2a13 [vs_0][fw_1] eth0:i[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=31790 TCP: 53901 -> 22 ....A. seq=761113cd ack=f92e2a47 ... ... ... monitor: caught sig 2 monitor: unloading [Expert@MyGW:0]# |
Example 2 - Capture only three Pre-Inbound packets at the FireWall Virtual Machine module
[Expert@MyGW:0]# fw monitor -m i -ci 3 monitor: getting filter (from command line) monitor: compiling monitorfilter: Compiled OK. monitor: loading monitor: monitoring (control-C to stop) [vs_0][fw_1] eth0:i[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=31905 TCP: 53901 -> 22 ....A. seq=76111bb5 ack=f92e683b [vs_0][fw_1] eth0:i[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=31906 TCP: 53901 -> 22 ....A. seq=76111bb5 ack=f92e68ef [vs_0][fw_1] eth0:i[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=31907 TCP: 53901 -> 22 ....A. seq=76111bb5 ack=f92e69a3 monitor: unloading Read 3 inbound packets and 0 outbound packets [Expert@MyGW:0]# |
Example 3 - Insert the FW Monitor chain is before the chain #2 and capture only three Pre-Inbound packets
[Expert@MyGW:0]# fw ctl chain in chain (15): 0: -7fffffff (0000000000000000) (00000000) SecureXL inbound (sxl_in) 1: -7ffffffe (0000000000000000) (00000000) SecureXL inbound CT (sxl_ct) 2: -7f800000 (ffffffff8b6718c0) (ffffffff) IP Options Strip (in) (ipopt_strip) 3: - 1fffff8 (ffffffff8b66f6f0) (00000001) Stateless verifications (in) (asm) 4: - 1fffff7 (ffffffff8b66f210) (00000001) fw multik misc proto forwarding 5: 0 (ffffffff8b8506a0) (00000001) fw VM inbound (fw) 6: 2 (ffffffff8b671d10) (00000001) fw SCV inbound (scv) 7: 4 (ffffffff8b061ed0) (00000003) QoS inbound offload chain module 8: 5 (ffffffff8b564d30) (00000003) fw offload inbound (offload_in) 9: 10 (ffffffff8b842710) (00000001) fw post VM inbound (post_vm) 10: 100000 (ffffffff8b7fd6c0) (00000001) fw accounting inbound (acct) 11: 22000000 (ffffffff8b0638d0) (00000003) QoS slowpath inbound chain mod (fg_sched) 12: 7f730000 (ffffffff8b3c40b0) (00000001) passive streaming (in) (pass_str) 13: 7f750000 (ffffffff8b0e5b40) (00000001) TCP streaming (in) (cpas) 14: 7f800000 (ffffffff8b671870) (ffffffff) IP Options Restore (in) (ipopt_res) out chain (14): 0: -7f800000 (ffffffff8b6718c0) (ffffffff) IP Options Strip (out) (ipopt_strip) 1: - 1fffff0 (ffffffff8b0d0190) (00000001) TCP streaming (out) (cpas) 2: - 1ffff50 (ffffffff8b3c40b0) (00000001) passive streaming (out) (pass_str) 3: - 1f00000 (ffffffff8b66f6f0) (00000001) Stateless verifications (out) (asm) 4: - 1ff (ffffffff8aeec0a0) (00000001) NAC Packet Outbound (nac_tag) 5: 0 (ffffffff8b8506a0) (00000001) fw VM outbound (fw) 6: 10 (ffffffff8b842710) (00000001) fw post VM outbound (post_vm) 7: 15000000 (ffffffff8b062540) (00000003) QoS outbound offload chain modul (fg_pol) 8: 21000000 (ffffffff8b0638d0) (00000003) QoS slowpath outbound chain mod (fg_sched) 9: 7f000000 (ffffffff8b7fd6c0) (00000001) fw accounting outbound (acct) 10: 7f700000 (ffffffff8b0e4660) (00000001) TCP streaming post VM (cpas) 11: 7f800000 (ffffffff8b671870) (ffffffff) IP Options Restore (out) (ipopt_res) 12: 7f900000 (0000000000000000) (00000000) SecureXL outbound (sxl_out) 13: 7fa00000 (0000000000000000) (00000000) SecureXL deliver (sxl_deliver) [Expert@MyGW:0]# [Expert@MyGW:0]# fw monitor -pi 2 -ci 3 monitor: getting filter (from command line) monitor: compiling monitorfilter: Compiled OK. monitor: loading in chain (17): 0: -7fffffff (0000000000000000) (00000000) SecureXL inbound (sxl_in) 1: -7ffffffe (0000000000000000) (00000000) SecureXL inbound CT (sxl_ct) 2: -7f800001 (ffffffff8b6774d0) (ffffffff) fwmonitor (i/f side) 3: -7f800000 (ffffffff8b6718c0) (ffffffff) IP Options Strip (in) (ipopt_strip) 4: - 1fffff8 (ffffffff8b66f6f0) (00000001) Stateless verifications (in) (asm) 5: - 1fffff7 (ffffffff8b66f210) (00000001) fw multik misc proto forwarding 6: 0 (ffffffff8b8506a0) (00000001) fw VM inbound (fw) 7: 2 (ffffffff8b671d10) (00000001) fw SCV inbound (scv) 8: 4 (ffffffff8b061ed0) (00000003) QoS inbound offload chain module 9: 5 (ffffffff8b564d30) (00000003) fw offload inbound (offload_in) 10: 10 (ffffffff8b842710) (00000001) fw post VM inbound (post_vm) 11: 100000 (ffffffff8b7fd6c0) (00000001) fw accounting inbound (acct) 12: 22000000 (ffffffff8b0638d0) (00000003) QoS slowpath inbound chain mod (fg_sched) 13: 70000000 (ffffffff8b6774d0) (ffffffff) fwmonitor (IP side) 14: 7f730000 (ffffffff8b3c40b0) (00000001) passive streaming (in) (pass_str) 15: 7f750000 (ffffffff8b0e5b40) (00000001) TCP streaming (in) (cpas) 16: 7f800000 (ffffffff8b671870) (ffffffff) IP Options Restore (in) (ipopt_res) out chain (16): 0: -7f800000 (ffffffff8b6718c0) (ffffffff) IP Options Strip (out) (ipopt_strip) 1: -70000000 (ffffffff8b6774d0) (ffffffff) fwmonitor (i/f side) 2: - 1fffff0 (ffffffff8b0d0190) (00000001) TCP streaming (out) (cpas) 3: - 1ffff50 (ffffffff8b3c40b0) (00000001) passive streaming (out) (pass_str) 4: - 1f00000 (ffffffff8b66f6f0) (00000001) Stateless verifications (out) (asm) 5: - 1ff (ffffffff8aeec0a0) (00000001) NAC Packet Outbound (nac_tag) 6: 0 (ffffffff8b8506a0) (00000001) fw VM outbound (fw) 7: 10 (ffffffff8b842710) (00000001) fw post VM outbound (post_vm) 8: 15000000 (ffffffff8b062540) (00000003) QoS outbound offload chain modul (fg_pol) 9: 21000000 (ffffffff8b0638d0) (00000003) QoS slowpath outbound chain mod (fg_sched) 10: 70000000 (ffffffff8b6774d0) (ffffffff) fwmonitor (IP side) 11: 7f000000 (ffffffff8b7fd6c0) (00000001) fw accounting outbound (acct) 12: 7f700000 (ffffffff8b0e4660) (00000001) TCP streaming post VM (cpas) 13: 7f800000 (ffffffff8b671870) (ffffffff) IP Options Restore (out) (ipopt_res) 14: 7f900000 (0000000000000000) (00000000) SecureXL outbound (sxl_out) 15: 7fa00000 (0000000000000000) (00000000) SecureXL deliver (sxl_deliver) monitor: monitoring (control-C to stop) [vs_0][fw_1] eth0:oq1 (TCP streaming (out))[1228]: 192.168.204.40 -> 192.168.204.1 (TCP) len=1228 id=37575 TCP: 22 -> 51702 ...PA. seq=34e2af31 ack=e6c995ce [vs_0][fw_1] eth0:OQ10 (TCP streaming post VM)[1228]: 192.168.204.40 -> 192.168.204.1 (TCP) len=1228 id=37575 TCP: 22 -> 51702 ...PA. seq=34e2af31 ack=e6c995ce [vs_0][fw_1] eth0:iq2 (IP Options Strip (in))[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=32022 TCP: 51702 -> 22 ....A. seq=e6c995ce ack=34e2af31 [vs_0][fw_1] eth0:IQ13 (TCP streaming (in))[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=32022 TCP: 51702 -> 22 ....A. seq=e6c995ce ack=34e2af31 [vs_0][fw_1] eth0:oq1 (TCP streaming (out))[1356]: 192.168.204.40 -> 192.168.204.1 (TCP) len=1356 id=37576 TCP: 22 -> 51702 ...PA. seq=34e2b3d5 ack=e6c995ce [vs_0][fw_1] eth0:OQ10 (TCP streaming post VM)[1356]: 192.168.204.40 -> 192.168.204.1 (TCP) len=1356 id=37576 TCP: 22 -> 51702 ...PA. seq=34e2b3d5 ack=e6c995ce [vs_0][fw_1] eth0:iq2 (IP Options Strip (in))[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=32023 TCP: 51702 -> 22 ....A. seq=e6c995ce ack=34e2b8f9 [vs_0][fw_1] eth0:IQ13 (TCP streaming (in))[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=32023 TCP: 51702 -> 22 ....A. seq=e6c995ce ack=34e2b8f9 [vs_0][fw_1] eth0:oq1 (TCP streaming (out))[1356]: 192.168.204.40 -> 192.168.204.1 (TCP) len=1356 id=37577 TCP: 22 -> 51702 ...PA. seq=34e2b8f9 ack=e6c995ce [vs_0][fw_1] eth0:OQ10 (TCP streaming post VM)[1356]: 192.168.204.40 -> 192.168.204.1 (TCP) len=1356 id=37577 TCP: 22 -> 51702 ...PA. seq=34e2b8f9 ack=e6c995ce [vs_0][fw_1] eth0:oq1 (TCP streaming (out))[412]: 192.168.204.40 -> 192.168.204.1 (TCP) len=412 id=37578 TCP: 22 -> 51702 ...PA. seq=34e2be1d ack=e6c995ce [vs_0][fw_1] eth0:OQ10 (TCP streaming post VM)[412]: 192.168.204.40 -> 192.168.204.1 (TCP) len=412 id=37578 TCP: 22 -> 51702 ...PA. seq=34e2be1d ack=e6c995ce [vs_0][fw_1] eth0:iq2 (IP Options Strip (in))[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=32024 TCP: 51702 -> 22 ....A. seq=e6c995ce ack=34e2bf91 [vs_0][fw_1] eth0:IQ13 (TCP streaming (in))[40]: 192.168.204.1 -> 192.168.204.40 (TCP) len=40 id=32024 TCP: 51702 -> 22 ....A. seq=e6c995ce ack=34e2bf91 [vs_0][fw_1] eth0:oq1 (TCP streaming (out))[716]: 192.168.204.40 -> 192.168.204.1 (TCP) len=716 id=37579 TCP: 22 -> 51702 ...PA. seq=34e2bf91 ack=e6c995ce [vs_0][fw_1] eth0:OQ10 (TCP streaming post VM)[716]: 192.168.204.40 -> 192.168.204.1 (TCP) len=716 id=37579 TCP: 22 -> 51702 ...PA. seq=34e2bf91 ack=e6c995ce monitor: unloading Read 3 inbound packets and 5 outbound packets [Expert@MyGW:0]# |
Example 4 - Show timestamps in the output for each packet
[Expert@MyGW:0]# fw monitor -T monitor: getting filter (from command line) monitor: compiling monitorfilter: Compiled OK. monitor: loading monitor: monitoring (control-C to stop) [vs_0][fw_1] 12Sep2018 19:08:05.453947 eth0:oq[124]: 192.168.3.53 -> 172.20.168.16 (TCP) len=124 id=38414 TCP: 22 -> 64424 ...PA. seq=1c23924a ack=3c951092 [vs_0][fw_1] 12Sep2018 19:08:05.453960 eth0:OQ[124]: 192.168.3.53 -> 172.20.168.16 (TCP) len=124 id=38414 TCP: 22 -> 64424 ...PA. seq=1c23924a ack=3c951092 [vs_0][fw_1] 12Sep2018 19:08:05.454059 eth0:oq[252]: 192.168.3.53 -> 172.20.168.16 (TCP) len=252 id=38415 TCP: 22 -> 64424 ...PA. seq=1c23929e ack=3c951092 [vs_0][fw_1] 12Sep2018 19:08:05.454064 eth0:OQ[252]: 192.168.3.53 -> 172.20.168.16 (TCP) len=252 id=38415 TCP: 22 -> 64424 ...PA. seq=1c23929e ack=3c951092 [vs_0][fw_1] 12Sep2018 19:08:05.454072 eth0:oq[252]: 192.168.3.53 -> 172.20.168.16 (TCP) len=252 id=38416 TCP: 22 -> 64424 ...PA. seq=1c239372 ack=3c951092 [vs_0][fw_1] 12Sep2018 19:08:05.454074 eth0:OQ[252]: 192.168.3.53 -> 172.20.168.16 (TCP) len=252 id=38416 TCP: 22 -> 64424 ...PA. seq=1c239372 ack=3c951092 [vs_0][fw_1] 12Sep2018 19:08:05.463165 eth0:iq[40]: 172.20.168.16 -> 192.168.3.53 (TCP) len=40 id=17398 TCP: 64424 -> 22 ....A. seq=3c951092 ack=1c239446 [vs_0][fw_1] 12Sep2018 19:08:05.463177 eth0:IQ[40]: 172.20.168.16 -> 192.168.3.53 (TCP) len=40 id=17398 TCP: 64424 -> 22 ....A. seq=3c951092 ack=1c239446 monitor: unloading [Expert@MyGW:0]# |
Example - List of Chain Modules with the FW Monitor, when you do not change the default capture positions
[Expert@MyGW:0]# fw ctl chain in chain (17): 0: -7fffffff (0000000000000000) (00000000) SecureXL inbound (sxl_in) 1: -7ffffffe (0000000000000000) (00000000) SecureXL inbound CT (sxl_ct) 2: -7f800000 (ffffffff8b6718c0) (ffffffff) IP Options Strip (in) (ipopt_strip) 3: -70000000 (ffffffff8b6774d0) (ffffffff) fwmonitor (i/f side) 4: - 1fffff8 (ffffffff8b66f6f0) (00000001) Stateless verifications (in) (asm) 5: - 1fffff7 (ffffffff8b66f210) (00000001) fw multik misc proto forwarding 6: 0 (ffffffff8b8506a0) (00000001) fw VM inbound (fw) 7: 2 (ffffffff8b671d10) (00000001) fw SCV inbound (scv) 8: 4 (ffffffff8b061ed0) (00000003) QoS inbound offload chain module 9: 5 (ffffffff8b564d30) (00000003) fw offload inbound (offload_in) 10: 10 (ffffffff8b842710) (00000001) fw post VM inbound (post_vm) 11: 100000 (ffffffff8b7fd6c0) (00000001) fw accounting inbound (acct) 12: 22000000 (ffffffff8b0638d0) (00000003) QoS slowpath inbound chain mod (fg_sched) 13: 70000000 (ffffffff8b6774d0) (ffffffff) fwmonitor (IP side) 14: 7f730000 (ffffffff8b3c40b0) (00000001) passive streaming (in) (pass_str) 15: 7f750000 (ffffffff8b0e5b40) (00000001) TCP streaming (in) (cpas) 16: 7f800000 (ffffffff8b671870) (ffffffff) IP Options Restore (in) (ipopt_res) out chain (16): 0: -7f800000 (ffffffff8b6718c0) (ffffffff) IP Options Strip (out) (ipopt_strip) 1: -70000000 (ffffffff8b6774d0) (ffffffff) fwmonitor (i/f side) 2: - 1fffff0 (ffffffff8b0d0190) (00000001) TCP streaming (out) (cpas) 3: - 1ffff50 (ffffffff8b3c40b0) (00000001) passive streaming (out) (pass_str) 4: - 1f00000 (ffffffff8b66f6f0) (00000001) Stateless verifications (out) (asm) 5: - 1ff (ffffffff8aeec0a0) (00000001) NAC Packet Outbound (nac_tag) 6: 0 (ffffffff8b8506a0) (00000001) fw VM outbound (fw) 7: 10 (ffffffff8b842710) (00000001) fw post VM outbound (post_vm) 8: 15000000 (ffffffff8b062540) (00000003) QoS outbound offload chain modul (fg_pol) 9: 21000000 (ffffffff8b0638d0) (00000003) QoS slowpath outbound chain mod (fg_sched) 10: 70000000 (ffffffff8b6774d0) (ffffffff) fwmonitor (IP side) 11: 7f000000 (ffffffff8b7fd6c0) (00000001) fw accounting outbound (acct) 12: 7f700000 (ffffffff8b0e4660) (00000001) TCP streaming post VM (cpas) 13: 7f800000 (ffffffff8b671870) (ffffffff) IP Options Restore (out) (ipopt_res) 14: 7f900000 (0000000000000000) (00000000) SecureXL outbound (sxl_out) 15: 7fa00000 (0000000000000000) (00000000) SecureXL deliver (sxl_deliver) [Expert@MyGW:0]# |