
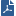

By default, SecureXL writes the output debug information to the /var/log/messages
To collect the applicable SecureXL debug and to make its analysis easier, perform the steps below.
Note - For more information, see the R80.20 Next Generation Security Gateway Guide - Chapter Kernel Debug on Security Gateway.
Important:
This is to avoid a possible issue when you cannot work with the CLI because of a high load on the CPU.
Procedure:
Step |
Description |
|---|---|
1 |
Connect to the command line on you Security Gateway. |
2 |
Log in to the Expert mode. |
3 |
Reset all kernel debug flags in all kernel debug modules:
|
4 |
Reset all the SecureXL debug flags in all SecureXL debug modules.
|
5 |
Allocate the kernel debug buffer:
|
6 |
Make sure the Security Gateway allocated the kernel debug buffer:
|
7 |
Configure the applicable kernel debug modules and kernel debug flags:
|
8 |
Configure the applicable SecureXL debug modules and SecureXL debug flags.
|
9 |
Examine the kernel debug configuration for kernel debug modules:
|
10 |
Examine the SecureXL debug configuration for SecureXL debug modules.
|
11 |
Remove all entries from both the Firewall Connections table and SecureXL Connections table:
Important:
|
12 |
Remove all entries from the Firewall Templates table:
Note - This command does not interrupt the existing connections. This step makes sure that you collect the debug of the real issue that is not affected by the existing connection templates. |
13 |
Start the kernel debug:
|
14 |
Replicate the issue, or wait for the issue to occur. |
15 |
Stop the kernel debug: Press CTRL+C. |
16 |
Reset all kernel debug flags in all kernel debug modules:
|
17 |
Reset all the SecureXL debug flags in all SecureXL debug modules.
|
18 |
Examine the kernel debug configuration to make sure it returned to the default:
|
19 |
Examine the SecureXL debug configuration to make sure it returned to the default.
|
20 |
Collect and analyze the debug output file:
|