VSX
Virtual System eXtension product runs several virtual firewalls on the same hardware.
Each Virtual System works as a virtual Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., typically protecting a specified network. When packets arrive at the VSX Gateway
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., typically protecting a specified network. When packets arrive at the VSX Gateway![]() Physical server that hosts VSX virtual networks, including all Virtual Devices that provide the functionality of physical network devices. It holds at least one Virtual System, which is called VS0., it sends traffic to the Virtual System
Physical server that hosts VSX virtual networks, including all Virtual Devices that provide the functionality of physical network devices. It holds at least one Virtual System, which is called VS0., it sends traffic to the Virtual System![]() Virtual Device on a VSX Gateway or VSX Cluster Member that implements the functionality of a Security Gateway. Acronym: VS. protecting the destination network. The Virtual System inspects all traffic and allows or rejects it according to rules defined in the security policy
Virtual Device on a VSX Gateway or VSX Cluster Member that implements the functionality of a Security Gateway. Acronym: VS. protecting the destination network. The Virtual System inspects all traffic and allows or rejects it according to rules defined in the security policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection..
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection..
In order to better understand how virtual networks work, it is important to compare physical network environments with their virtual (VSX![]() Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts.) counterparts. While physical networks consist of many hardware components, VSX virtual networks reside on a Security Group
Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts.) counterparts. While physical networks consist of many hardware components, VSX virtual networks reside on a Security Group![]() A logical group of Security Gateway Modules that provides Active/Active cluster functionality. A Security Group can contain one or more Security Gateway Modules. Security Groups work separately and independently from each other. To the production networks, a Security Group appears a single Security Gateway. (in VSX mode) that defines and protects multiple independent networks, together with their virtual components.
A logical group of Security Gateway Modules that provides Active/Active cluster functionality. A Security Group can contain one or more Security Gateway Modules. Security Groups work separately and independently from each other. To the production networks, a Security Group appears a single Security Gateway. (in VSX mode) that defines and protects multiple independent networks, together with their virtual components.
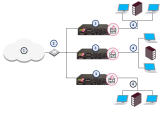
Example Physical Network Topology
In a typical deployment with multiple Security Gateways, each protects a separate network.
Each physical Security Gateway has interfaces to the perimeter router and to the network it protects.
|
Item |
Description |
|---|---|
|
1 |
Internet |
|
2 |
Router |
|
3 |
Security Gateways |
|
4 |
Network |
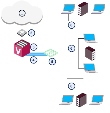
Example VSX Virtual Network Topology
Deploy one VSX Gateway with four Virtual Systems to protect multiple networks.
|
Item |
Description |
|---|---|
|
1 |
Internet |
|
2 |
Router |
|
3 |
VSX Gateway. Each Virtual System in a VSX environment is a Security Gateway, with the same security and networking functionality as a physical gateway. Each handles packet traffic to and from the one network it protects. |
|
4 |
Warp Links. Virtual interfaces and network cables connect the Virtual Systems and the Virtual Switch |
|
5 |
Virtual Switch. Connects all the Virtual Systems to the Internet router. |
|
6 |
Networks |
For more information, see the R80.20SP Quantum Scalable Chassis VSX Administration Guide.