Appendix
Active Directory Size Estimation
You can use the external tool ADFind to estimate how many objects will be scanned by the Directory Scanner.
The query for counting the exact number of objects that will be scanned by the Directory Scanner on a given search base is:
|
|
The query counts:
-
Users that are not contacts.
-
Computers.
-
Groups that are security groups (not distribution groups).
-
Organizational Units (including "Users", "Computers" and "Built-in" containers).
For example:
If you want to scan the "marketing" OU in the "company.org" domain the query should be:
|
|
If you want to scan the whole "company.org" domain the query should be:
|
|
Architecture
The purpose of this document is to help you plan your Endpoint Security environment. It describes the best practices for server deployment and sizing the Endpoint Security servers.
Overview of the System Architecture
An Endpoint Security environment includes several components that should be configured correctly for the best performance.
Required Components:
-
Endpoint Security Management Server - Computer that contains the Endpoint Security software and databases. The Endpoint Security Management Server communicates with Endpoint Security clients to manage Endpoint Security client rules and to update protections.
-
SmartEndpoint- Application installed on a Windows platform that lets you deploy, monitor, and configure Endpoint Security clients and rules. You can install SmartEndpoint on the Endpoint Security Management Server (Windows only) or on a computer that supports the Endpoint Security client installation.
-
Endpoint Policy Server - Server that manages traffic from the Endpoint Security clients. The Endpoint Security Management Server also acts as an Endpoint Policy Server. You can add external Endpoint Policy Servers to improve performance in large environments.
-
Endpoint Security Management Server for High Availability - A backup server that is always available for down time situations.
-
Endpoint Security Database - Contains the policy that enforces security on Endpoint Security clients. This database also contains user and computer objects, licensing and Endpoint monitoring data.
-
Directory Scanner - Software component that synchronizes the structure and contents of the Active Directorywith the Endpoint Security database.
-
Endpoint Security Clients - Endpoint Security client application installed on end-user computers. These Endpoint Security clients monitor the security aspects of your endpoints and enforce security rules.
-
Endpoint Security Blades - Library of software blades available on the Endpoint Security Management Server. You can install any or all of these blades on individual Endpoint Security clients.
External Endpoint Policy Servers
External Endpoint Policy Servers decrease the load of the Endpoint Security Management Server and reduce the bandwidth required between sites. By default, the Endpoint Security Management Server also acts as an Endpoint Policy Server, in addition to the other Endpoint Policy Servers. The work of communication with the Endpoint Security clients is distributed among all of them.
The Endpoint Policy Servers are located between the Endpoint Security clients and the Endpoint Security Management Server. For most tasks, Endpoint Security clients communicate with the Endpoint Policy Servers and the Endpoint Policy Servers communicate with the Endpoint Security Management Server.
If there are multiple Endpoint Policy Servers in an environment, each Endpoint Security client does an analysis to find which Endpoint Policy Server is "closest" (will be fastest for communication) and automatically communicates with that server.
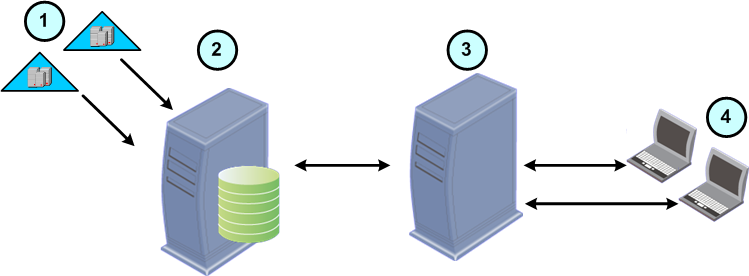
|
Item |
Description |
|---|---|
|
1 |
Active Directory Domains |
|
2 |
Endpoint Security Management Server |
|
3 |
External Endpoint Policy Server |
|
4 |
Enterprise workstations with Endpoint Security clients installed |
The Endpoint Policy Server handles the most frequent and bandwidth-consuming communication. The Endpoint Policy Server handles these requests without forwarding them to the Endpoint Security Management Server:
-
All heartbeat and synchronization requests.
-
Policy downloads
-
Anti-Malware updates
-
All Endpoint Security client logs (the Endpoint Policy Server is configured as Log Server by default).
The Endpoint Policy Server sends this data to the Endpoint Security Management Server:
-
All Software Blade-specific messages (which require information to be stored in the database). For example, Full Disk Encryption recovery data.
-
Monitoring data. This includes the connection state and other monitoring data for connected clients.
-
Policy Server generated messages.
Planning Your Environment
Consider these factors to plan an environment that is best for your organization:
Centralized Server Deployment
A centralized server deployment has one Endpoint Security Management Server:
-
The Endpoint Security Management Server, which is also an Endpoint Policy Server by default, manages all Endpoint Security client requests and communication.
-
The Endpoint Security Management Server, which is defined as Log Server by default, saves all Endpoint Security clients logs.
Distributed Server Deployment
In a distributed deployment, additional Policy Servers handle some activities instead of the Endpoint Security Management Server. This provides better performance in larger environments.
External Endpoint Policy Servers can perform these functions:
-
Reduce bandwidth between a remote site and the site where the Endpoint Security Management Server is located (the central site).
-
Let clients stay connected to the server if connectivity issues occur between a remote site and the central site. Clients can communicate with the local Endpoint Policy Server at the remote site.
-
Improve overall system performance by distributing common client messages and policy enforcement between multiple Endpoint Policy Servers.
See more about External Endpoint Policy Servers.
