Deploying a CloudGuard Network Security Gateway for OpenStack
To deploy a Check Point Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. that secures traffic between the Internet and an internal network in an OpenStack
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. that secures traffic between the Internet and an internal network in an OpenStack![]() An open source cloud-computing infrastructure for service providers and enterprises. It includes modules for administration, storage, networking and Virtual Machine deployment and control.-based cloud:
An open source cloud-computing infrastructure for service providers and enterprises. It includes modules for administration, storage, networking and Virtual Machine deployment and control.-based cloud:
-
Deploy an internal OpenStack subnet that is routed to the Internet through a Check Point Security Gateway instance.
-
Install an OpenStack-ready Gaia
 Check Point security operating system that combines the strengths of both SecurePlatform and IPSO operating systems. image on the Security Gateway instance.
Check Point security operating system that combines the strengths of both SecurePlatform and IPSO operating systems. image on the Security Gateway instance.
OpenStack deployment prerequisites:
-
A public network.
-
An external network.
-
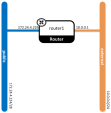
A router ("router1") that has one interface connected to a public network ("public"), and one interface connected to an external network ("external").
Defining the Network Topology
Deployment steps:
-
Add an "internal" network.
-
Configure a subnet ("internal-subnet") with the IP addresses in the "internal" network.
-
Launch a Check Point Security Gateway instance that connects the "external" network and the "internal" network.
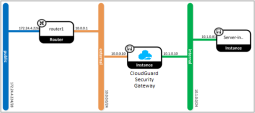
After the deployment, the network topology will look like the example on this picture:
Two ways to configure the gateway:
-
As a Security Gateway which can then connect from a Security Management Server
 Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. that is not in the cloud over the Internet to the Security Gateway.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. that is not in the cloud over the Internet to the Security Gateway. -
As a Security Gateway and Security Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. (a standalone
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. (a standalone Configuration in which the Security Gateway and the Security Management Server products are installed and configured on the same server. deployment) which can then connect from a SmartConsole
Configuration in which the Security Gateway and the Security Management Server products are installed and configured on the same server. deployment) which can then connect from a SmartConsole Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. over the Internet to the Security Management Server.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. over the Internet to the Security Management Server.
The Check Point Security Gateway inspects all traffic to and from the Internet and protects servers that are connected to the "internal" network.
Creating a Security Group
The Security Gateway instance enforces the Security Policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. configured using the Security Management Server. Because of that you must define the Security Group for traffic over the interfaces with a permissive policy:
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. configured using the Security Management Server. Because of that you must define the Security Group for traffic over the interfaces with a permissive policy:
-
Define the Security Group.
-
Add a permissive rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session..
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session..$ openstack security group create gateway-security-group --description "A permissive security group to be applied to the gateway"$ openstack security group rule create --protocol tcp --ingress --ethertype IPv4 --remote-ip 0.0.0.0/0 gateway-security-group
Creating the Internal Network
Create the "internal" network with this command:
$ openstack network create internal
Creating the Internal Subnet
Create the internal subnet and attach it to the "internal" network with this command:
$ openstack subnet create internal-subnet --network internal --subnet-range INTERNAL-SUBNET-CIDR --allocation-pool start=INTERNAL-START,end=INTERNAL-END --gateway INTERNAL-GATEWAY-ADDRESS
Where:
-
INTERNAL-STARTandINTERNAL-END- the IP address range for the "internal" network subnet. -
INTERNAL-SUBNET-CIDR- the "internal" network subnet address in CIDR notation. -
INTERNAL-GATEWAY-ADDRESS- an IP address from the internal subnet that will be used as the address of the Security Gateway interface connected to this subnet (for example, 10.1.0.10 - as shown on the network topology illustration above).
Creating the Internal Security Gateway Port
Create the internal Security Gateway port. This will be the interface of the Security Gateway that is attached to the "internal" network.
$ openstack port create --network internal --fixed-ip ip-address=INTERNAL-GATEWAY-ADDRESS --security-group gateway-security-group internal-gw-port
Where INTERNAL-GATEWAY-ADDRESS is the Security Gateway address defined in Creating the Internal Subnet.
Allowing Traffic from the Internet through the Internal Security Gateway Port
Edit the internal Security Gateway port to allow traffic from the Internet to the internal network. Traffic will pass through "router1" to the Security Gateway and finally to the internal network.
To allow traffic from any source IP address, edit the internal Gateway port:
-
Get MAC address:
$ int_port_mac=$(openstack port show internal-gw-port -f value -c mac_address) -
Allow traffic with source MAC and any Source IP address:
$ openstack port set internal-gw-port --allowed-address ip-address=0.0.0.0/0,mac-address=$int_port_mac
|
|
Note - These commands provide no output. |
Creating the External Security Gateway Port
Create the external Security Gateway port. The external port is used as the interface of the Security Gateway that is attached to the "external" network. The "external" network is connected to the "public" network and the Internet) through "router1" (as shown on the network topology illustration above).
$ openstack port create --network external –fixed-ip ip-address=EXTERNAL-GATEWAY-ADDRESS --security-group gateway-security-group external-gw-port
Where EXTERNAL-GATEWAY-ADDRESS is an IP address from the subnet of the "external" network (for example, 10.0.0.10 - as shown on the network topology illustration above).
Allowing Traffic from the Internal Network through the External Security Gateway Port
Edit the external Security Gateway port to allow traffic from the internal subnet addresses to the external Security Gateway port. Traffic from the internal network is allowed through the Security Gateway, routed to the "external" network, to "router1" and the Internet.
To allow traffic with a source IP address in the internal subnet IP address range, edit the external Security Gateway port:
-
Get MAC address:
$ ext_port_mac=$(openstack port show external-gw-port -f value -c mac_address) -
Allow traffic with source MAC and any Source IP address in internal subnet IP:
$ openstack port set external-gw-port --allowed-address ip-address=INTERNAL-SUBNET-CIDR,mac-address=$ext_port_macWhere
INTERNAL-SUBNET-CIDRis the internal subnet IP address range.
|
|
Note - These commands provide no output. |
Adding a Route to the Internal Network
Update the router with a route to the internal network:
$ openstack router set --route destination=INTERNAL-SUBNET-CIDR,gateway=EXTERNAL-GATEWAY-ADDRESS router1
Where:
-
EXTERNAL-GATEWAY-ADDRESS- the Security Gateway IP address defined earlier. -
INTERNAL-SUBNET-CIDR- the internal subnet IP address range.
Downloading the Image
-
Download the CloudGuard Security Gateway for OpenStack image version from sk158292.
-
Save the image to the OpenStack server.
-
Load the image.
$ image_path="<QCOW2-FILE-PATH>"$ image_name="IMAGE-NAME"$ openstack image create --disk-format qcow2 --min-disk 0 --min-ram 4096 --public --file $image_path $image_name --property hw_vif_multiqueue_enabled=trueWhere:
-
QCOW2 FILE PATH- the path to the saved qcow2 image. -
IMAGE-NAME- the name of the image (for example, "Check Point Image").
The command outputs the image ID (you can use it later to launch a Security Gateway instance).
-
|
|
Note - Do this step one time in an OpenStack deployment (you can use one image to launch many instances). |
Creating a Machine Flavor
A machine flavor is the list of resources allocated to a Virtual Machine instance. You can create a flavor with the resources required to run the image or use an existing flavor that meets the minimum resource requirements.
The 4096 parameter in the command line is a RAM quantity of 4096 MiB. You can set it to a different value depending on the expected load.
You must do this operation as the OpenStack admin.
$ openstack flavor create 4096Mib-50GiB-4CPU --vcpus 4 --ram 4096 --disk 50
|
|
Note - Do this step one time in an OpenStack deployment (you can use the same flavor to launch many instances). |
Importing a Key Pair
|
|
Note - If you do not have an RSA public key, you can use this command to create one:
|
Import a key pair into the OpenStack environment. For that, use the Web UI or this command:
$ openstack keypair create --public-key <KEY-PATH> <KEY-NAME>
Where:
-
KEY-PATH- the path toid_rsa.pub(usually located in~/.ssh/id_rsa.pub). -
KEY-NAME- the name of the key.
Launching a Security Gateway Instance
Before you launch a Security Gateway instance, extract the identifiers of the Security Gateway ports created in the earlier steps.
To launch a Security Gateway instance using the First Time Configuration Wizard:
-
Run these commands:
$ external_gw_port_id=`openstack port show external-gw-port -f value -c id`$ internal_gw_port_id=`openstack port show internal-gw-port -f value -c id`$ openstack server create <INSTANCE-NAME> --flavor 4096Mib-50GiB-4CPU --key-name <KEY-NAME> --image CloudGuardR82 --nic port-id=$external_gw_port_id --nic port-id=$internal_gw_port_id --use-config-driveWait for the process to finish.
Where:
-
KEY-NAME- the name of the imported key. -
INSTANCE-NAME- the desired instance name (for example, "R82-Instance").
-
-
Run the First Time Configuration Wizard (see Configuring the Check Point CloudGuard Security Gateway).
To launch a Security Gateway instance with an automated script:
-
Create a
USER-SCRIPTthat runs at the time the computer boots up for the first time. Use these commands in the script to configure the password for the OS admin user and to set the gateway as a standalone Security Management Server and Security Gateway:#!/bin/bash clish -c 'set user admin password-hash ADMIN-PASSWORD-HASH' -s (config_system -s 'install_security_gw=true&install_ppak=true&install_security_managment=true&install_mgmt_primary=true&install_mds_primary=false&mgmt_admin_name=MANAGEMENT-ADMIN-USERNAME&mgmt_admin_passwd=MANAGEMENT-ADMIN-PASSWORD&mgmt_gui_clients_radio=any' ; shutdown -r now &)Where:
-
ADMIN-PASSWORD-HASH- the hash of the OS admin user password. Generate the password hash with:openssl passwd -1<password>. -
INTERNAL-GATEWAY-ADDRESSandINTERNAL-GATEWAY-MASKLEN- the internal network address and mask size in bits. -
EXTERNAL-GATEWAY-ADDRESSandEXTERNAL-GATEWAY-MASKLEN- the internal network address and mask size in bits. -
MANAGEMENT-ADMIN-USERNAMEandMANAGEMENT-ADMIN-PASSWORD- the initial management administrator user name and password (not hash). -
USER-SCRIPT- the name of the script file.
-
-
Launch the instance with the flavor, key pair, image ID or name, and interfaces defined in the earlier steps:
$ external_gw_port_id=`openstack port show external-gw-port -f value -c id`$ internal_gw_port_id=`openstack port show internal-gw-port -f value -c id`$ openstack server create <INSTANCE-NAME> --flavor 4096Mib-50GiB-4CPU --key-name <KEY-NAME> --image <IMAGE-NAME or IMAGE-ID> --nic port-id=$external_gw_port_id --nic port-id=$internal_gw_port_id --use-config-drive --user-data <USER-SCRIPT> --waitWhere:
-
KEY-NAME- the name of the imported key. -
INSTANCE-NAME- the desired instance name (for example, "R82-Instance"). -
IMAGE-NAMEorIMAGE-ID- the name or ID of the image. -
USER-SCRIPT- the path to the script file.
-
Several minutes after you configure the Check Point Security Gateway for the first time, you can use the Gaia Portal![]() Web interface for the Check Point Gaia operating system. to configure your Security Gateway.
Web interface for the Check Point Gaia operating system. to configure your Security Gateway.
Configuring the Check Point CloudGuard Security Gateway
|
|
Note: - Use SSH to connect to the Security Gateway instance as the admin user. Compare the public fingerprint from the Security Gateway instance to the public key from the OpenStack Console. If you do not compare the fingerprints, you are vulnerable to a man-in-the-middle attack on your SSH session. It can take a few minutes after the launch of an instance before the system log is available on the OpenStack Console. To connect to the Gateway instance over SSH:
|
To configure the Check Point Security Gateway:
-
Set the admin password of the Security Gateway.
-
Connect to the Gaia Portal of the Security Gateway.
-
Configure the Gateway instance as a Security Gateway, or as a Security Gateway and Security Management Server (a standalone deployment).
|
|
Note - The host IP address and the default route are set automatically. Do not change them. |
To set the administrator password:
-
Set the administrator password. For that, in the management interface of Gaia Clish
 The name of the default command line shell in Check Point Gaia operating system. This is a restricted shell (role-based administration controls the number of commands available in the shell)., run:
The name of the default command line shell in Check Point Gaia operating system. This is a restricted shell (role-based administration controls the number of commands available in the shell)., run:set user admin passwordAt the prompt, enter the administrator password.
-
Run:
save config -
Exit the gateway shell. Run:
exit
To configure the Check Point Security Gateway:
-
Using a browser, connect to https://<GATEWAY-FLOATING-IP>
-
In the Gaia Portal window, log in using the administrator name (admin) and password that you defined earlier.
-
The Portal shows the First Time Configuration Wizard.
Click Next.
-
Set the date and time (manually, or enter the hostname or IP address of the NTP server).
Click Next.
-
Set the host name for the appliance.
-
Optional: Set the domain name, and IPv4 addresses for the DNS servers. You can configure IPv6 DNS servers.
Click Next.
-
The interface page shows the internal IPv4 address of the interface. Do not change this setting.
Click Next.
-
Set the username and password for the Security Management Server administrator account.
Click Next.
-
Select Security Gateway and/or Security Management
Click Next.
-
Define the GUI Clients that can log in to the Security Management Server.
Click Next.
-
If the Help Check Point Improve Software Updates window shows, click Yes or No as necessary.
-
Click Finish and then OK.
Associating a Public Address with the Security Gateway Instance
The "external" IP address of the launched Security Gateway is allocated from the "external" network. This address is usually not reachable from the Internet. To make the external address reachable, select a "floating" IP address from the "public" network subnet. Then, associate this address with the address of the external interface of the Security Gateway.
-
Extract the external interface identifier.
-
Select and assign a public IP address and print the address. We will refer to this IP address as GATEWAY-FLOATING-IP.
$ external_gw_port_id=`openstack port show external-gw-port -f value -c id`$ openstack floating ip create --port $external_gw_port_id public -f value -c floating_ip_address