
What can I do here?
Use this window to configure directional VPN enforcement -- allow VPN connections in one direction only.
|
Getting Here - Security Policies Access Control > Policy > VPN Column > Directional Match Condition. |
Configurable Objects in a Direction
Name of Object |
Description |
|---|---|
Remote Access |
Remote Access VPN community |
Site to Site VPN |
Regular Star or Mesh VPN community |
Any Traffic |
Any traffic |
All_GwToGw |
All Site to Site VPN communities |
All_Communities |
All Site to Site and Remote Access VPN communities |
External_clear |
For traffic outside the VPN community |
Internal_clear |
For traffic between local domains within the VPN community |
Note - Clear text connections originating from these objects are not subject to enforcement:
There is no limit to the number of VPN directions that you can configure in a single rule. In general, if you have many directional enforcements, consider replacing them with a standard bidirectional condition.
Directional Enforcement between Communities
$FWDIR/conf/vpn_route.conf file.To add a route entry to the enforcement point gateway:
On the management module of each gateway in the community (except for the enforcement point gateway), add an entry in the $FWDIR/conf/vpn_route.conf file:
Destination |
Next hop router interface |
Install on |
|---|---|---|
< |
< |
< |
These are the variables in the entry:
destination_community_obj - a network object for the combined encryption domain of the communityenforcement_point_gw - the gateway that is a member of both communities and transfers the encrypted traffic between themmanaged_FW_object - all community members that are managed by the management moduleIn the example below, Washington is a Mesh community, and London is a VPN Star.
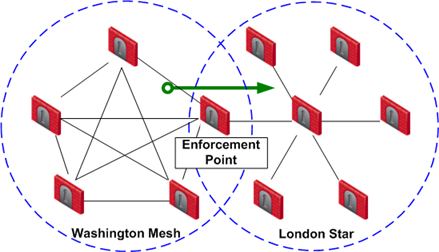
The directional VPN rule below must be configured for the enforcement point gateway in the Access Control Policy Rule Base:
Source |
Destination |
VPN |
Services & Applications |
Action |
|---|---|---|---|---|
|
|
Washington => London |
|
|
The rule is applied to all VPN traffic that passes through the enforcement point gateway between the Washington and London communities. If a connection is opened from a source in the Washington Mesh, and the destination is in the London Star, the connection is allowed. Otherwise, the connection is denied.
Note - The Directional Enforcement applies only to the first packet of a connection. If the connection is permitted, the following packets of this connection are also permitted, including the packets in the opposite direction.