
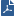

vSEC Controller integrates the Check Point Security Management Server with OpenStack Keystone. The Check Point Data Center server connects to OpenStack and retrieves network object data from OpenStack Neutron.
To connect to the OpenStack server:
http(s)://1.2.3.4:5000/<keystone_version>
Example: https://1.2.3.4:5000/v2.0
Note - If you do not know your keystone URL, use this command to find it:
openstack endpoint show keystone | grep publicurl
If the certificate window opens, confirm the certificate and click Trust.
If the status is not Connected, troubleshoot the issue before you continue.
Note - If you want to log into an OpenStack domain that is not your default domain, use this format: <OpenStack_domain_name>/<user_name>
Objects
Imported Properties
Imported Property |
Description |
|---|---|
IP |
VM - VM IP address Security Group - IP addresses of the VMs inside the group Subnets - IP addresses of the VMs inside the subnet |
Note |
Instances - Empty Security Group - Description of the group Subnet - IP address and mask of the subnet |
URI |
Object path |
To connect vSEC Controller to a VMware vCenter or VMware NSX Data Center Server:
The Check Point Data Center Server connects to the VMware vCenter and retrieves object data. vSEC Controller updates IP addresses and other object properties in the Data Center Objects.
You must have a VMware vCenter username with at least Read-Only permissions.
VMware vCenter objects appear in the Hosts and Clusters view in the vCenter vSphere Web Client.
Imported Properties |
Description |
|---|---|
IP |
vCenter server IP address or DNS name Note - You must install VMware tools on each virtual machine to retrieve the IP addresses for each computer |
Note |
VMware vCenter object notes |
URI |
Object path |
The vSEC Controller integrates the VMware NSX Manager Server with Check Point security. The Check Point Data Center Server connects to the VMware NSX Manager Server and retrieves object data. The vSEC Controller updates IP addresses and other object properties in the Data Center Objects group.
You must have a VMware NSX username with permission of an Auditor or greater to access the vSEC Controller.
Note - This role is sufficient for vSEC Controller functionality. More permissions can be required for service registration (vSEC Gateway for NSX).
The VMware NSX Controller object is the Security Group. It enables a static or dynamic grouping based on objects such as virtual machines, vNICs, vSphere clusters, logical switches, and so on.
Imported Properties |
Description |
|---|---|
IP |
All the security group IP addresses |
Note |
Description value of a security group |
URI |
Object path |
Threat Prevention Tagging
Threat Prevention Tagging automatically assigns Security Tags to Data Center objects based on Threat Prevention analysis and group affiliation. This enables the usage of dynamic Security Groups in policy rules.
Enable Threat Prevention Tagging for Anti-Bot and Anti-Virus services to the vSEC for NSX Gateway. When a threat from an infected VM reaches the gateway and is denied entry, it is tagged as an infected VM in the NSX Manager.
To apply Threat Prevention Tagging:
To activate tagging:
tagger_clivSEC for NSX Clusters with active Anti-Bot and/or Anti-Virus blades on them, show.
Make sure Cluster activated successfully shows.
When it is activated, the Cluster automatically tags infected VMs in the NSX Manager Server. The Security Tags are:
Check_Point.BotFoundCheck_Point.VirusFoundThe Security Tags are created automatically in the NSX Manager Server when the Cluster is activated.
When Security Tags are configured, you can create policy rules based on the Security Groups that contain those tags.
Advanced options:
Use advanced menu options to configure the tags.
Show Activated gateways - Lists the activated Clusters and the status of each vSEC for NSX Gateway.
Modify Anti-Bot Security Tag - Enable or disable the tagging for the Anti-Bot blade and change the Security Tag.
Modify Anti-Virus Security Tag - Enable or disable the tagging for the Anti-Virus Software Blade and change the Security Tag.
Modify White List - IP Addresses listed in the White List are not tagged. (Split by spaces. Ranges are not accepted.)
Create New Security Tag - Creates a new Security Tag in the NSX Manager Server.
Update Data - When you add a new ESX to a Cluster, vSEC for NSX Gateway automatically updates the Threat Prevention Tagging data within 15 minutes. Select this option to manually update the data on the new vSEC for NSX Gateway.
In SmartConsole, in the Logs & Monitor tab, see vSEC Tagging in the Blade column.
Message |
Description |
|---|---|
|
Threat Prevention tagging successfully tagged a VM due to malicious traffic. |
|
An IP address appears twice in the ESX. Tagging this prevents false positive tagging of Virtual Machines with duplicate IP addresses in the ESX. |
|
Error getting a Data Center object from the R80.10 Security Management Server API. Check that there is a trusted connection for vSEC Controller. |
|
VM IP address is on the White list and the Threat Prevention tag is ignored. |